Question 66
Which operations are allowed when working with App-ID application tags?
Question 67
Complete the statement. A security profile can block or allow traffic.
Question 68
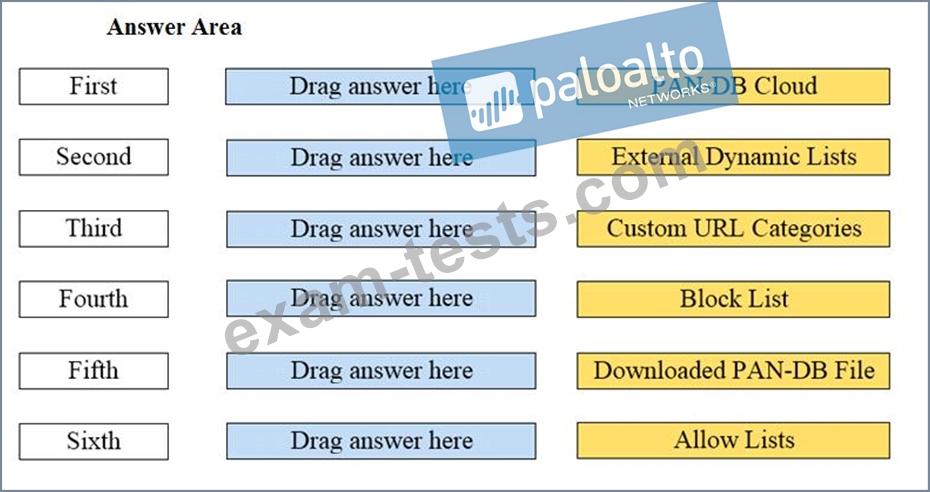
Arrange the correct order that the URL classifications are processed within the system.

Question 69
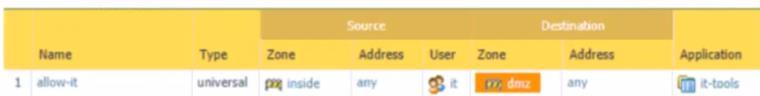
Based on the screenshot what is the purpose of the group in User labelled ''it"?

Question 70
Given the network diagram, traffic should be permitted for both Trusted and Guest users to access general Internet and DMZ servers using SSH. web-browsing and SSL applications Which policy achieves the desired results?
A)

B)

C)
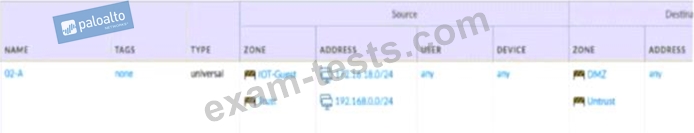
D)

A)

B)

C)

D)