Question 136
Which interface does not require a MAC or IP address?
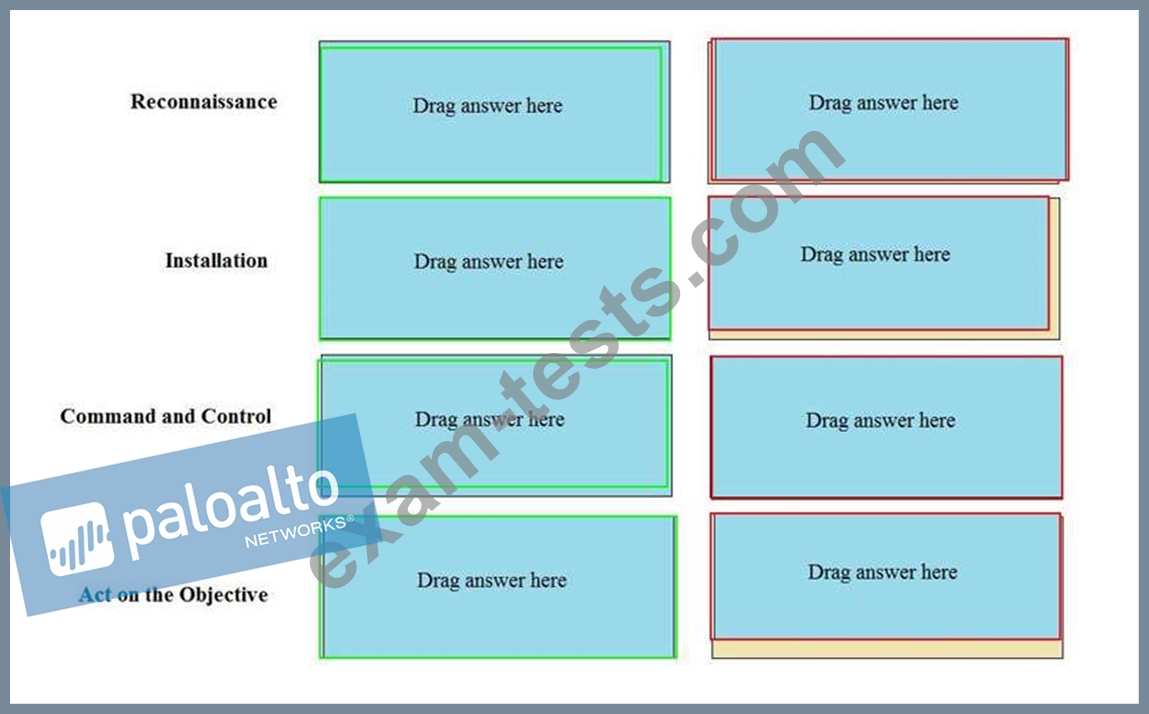
Question 137
Match the Cyber-Attack Lifecycle stage to its correct description.
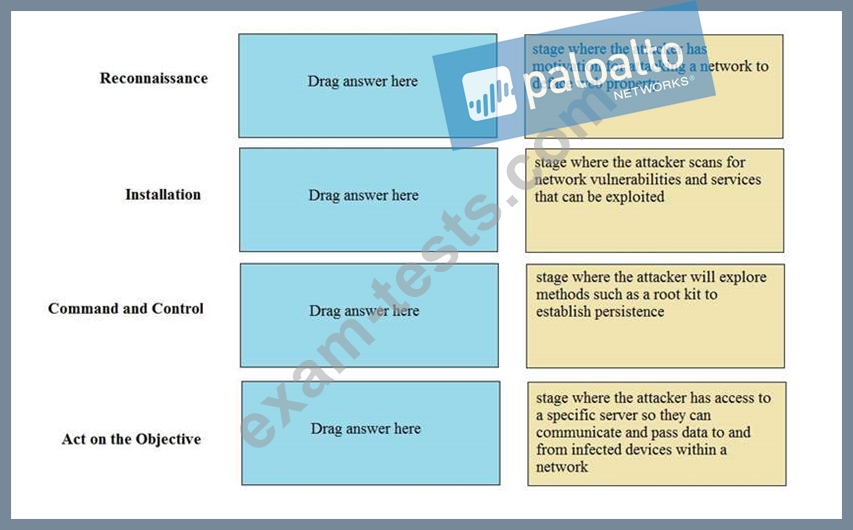

Question 138
Which service protects cloud-based applications such as Dropbox and Salesforce by administering permissions and scanning files for sensitive information?
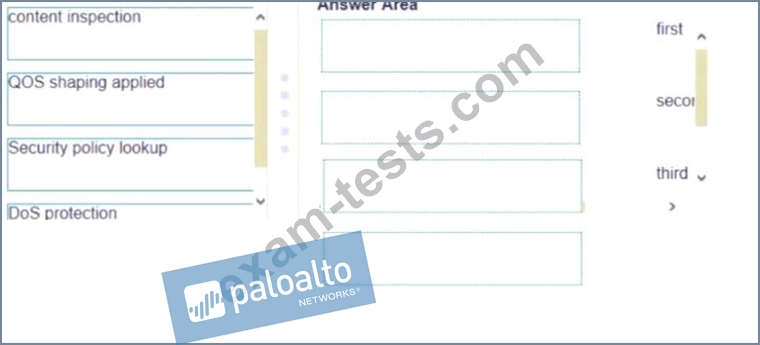
Question 139
Place the following steps in the packet processing order of operations from first to last.

Question 140
Your company occupies one floor in a single building you have two active directory domain controllers on a single networks the firewall s management plane is only slightly utilized.
Which user-ID agent sufficient in your network?
Which user-ID agent sufficient in your network?