Question 141
Which protocol is used to map usernames to user groups when User-ID is configured?
Question 142
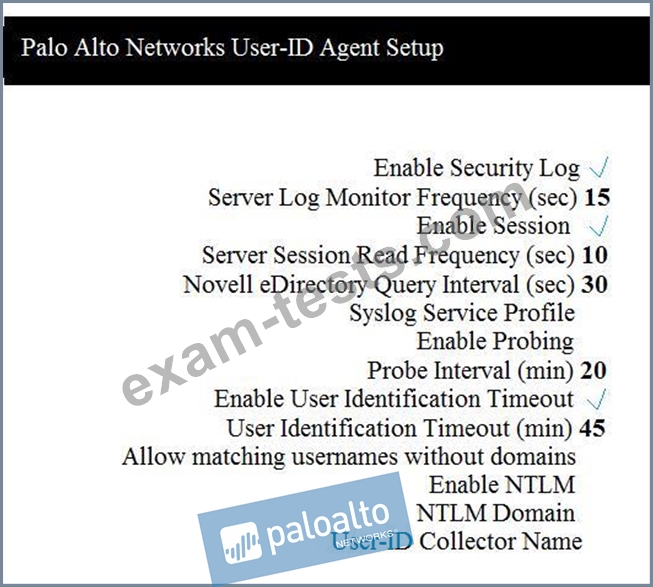
Which two configuration settings shown are not the default? (Choose two.)

Question 143
Which data-plane processor layer of the graphic shown provides uniform matching for spyware and vulnerability exploits on a Palo Alto Networks Firewall?


Question 144
What must be configured for the firewall to access multiple authentication profiles for external services to authenticate a non-local account?
Question 145
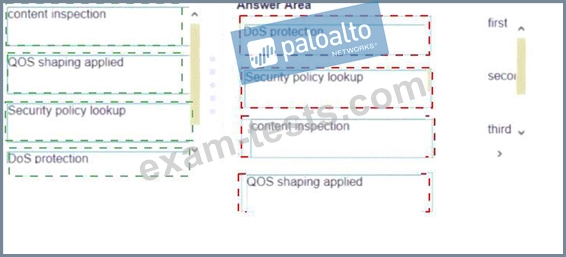
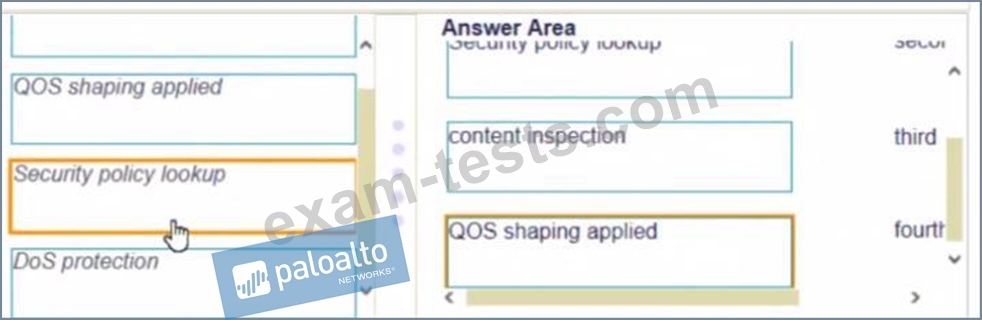
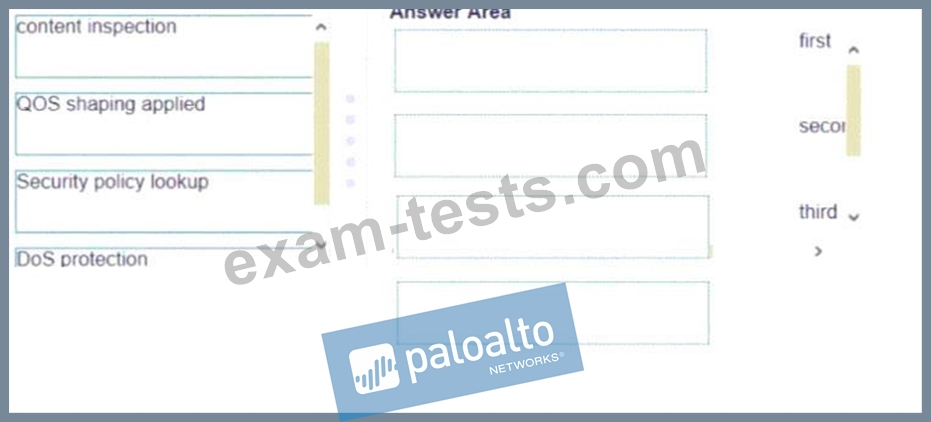
Place the following steps in the packet processing order of operations from first to last.

Premium Bundle
Newest PCNSA Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing PCNSA Exam! BraindumpsPass.com now offer the updated PCNSA exam dumps, the BraindumpsPass.com PCNSA exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com PCNSA pdf dumps with Exam Engine here: