Question 121
Which protocol used to map username to user groups when user-ID is configured?
Question 122
What must be configured for the firewall to access multiple authentication profiles for external services to authenticate a non-local account?
Question 123
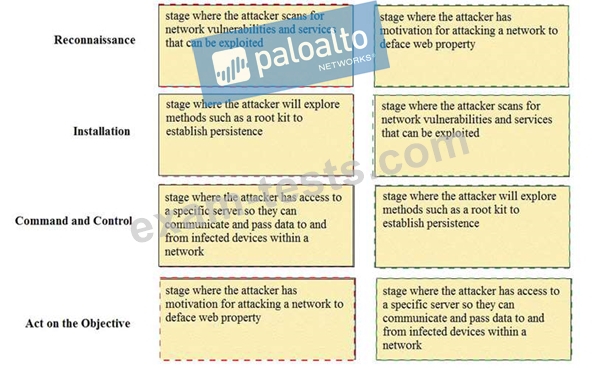
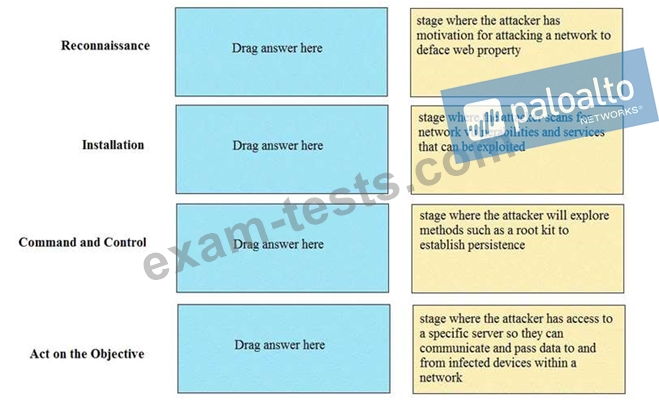
Match the Cyber-Attack Lifecycle stage to its correct description.

Question 124
What do dynamic user groups you to do?
Question 125
Recently changes were made to the firewall to optimize the policies and the security team wants to see if those changes are helping.
What is the quickest way to reset the hit counter to zero in all the security policy rules?
What is the quickest way to reset the hit counter to zero in all the security policy rules?
Premium Bundle
Newest PCNSA Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing PCNSA Exam! BraindumpsPass.com now offer the updated PCNSA exam dumps, the BraindumpsPass.com PCNSA exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com PCNSA pdf dumps with Exam Engine here: