Question 6
How are Application Fillers or Application Groups used in firewall policy?
Question 7
Which data flow direction is protected in a zero trust firewall deployment that is not protected in a perimeter-only firewall deployment?
Question 8
Which link in the web interface enables a security administrator to view the security policy rules that match new application signatures?
Question 9
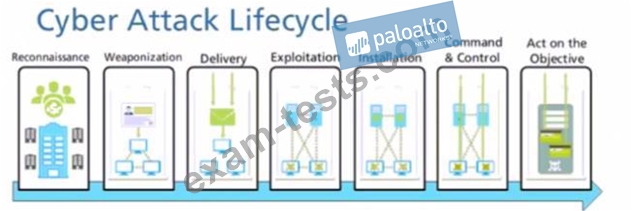
Given the cyber-attack lifecycle diagram identify the stage in which the attacker can run malicious code against a vulnerability in a targeted machine.

Question 10
Which type of security rule will match traffic between the Inside zone and Outside zone, within the Inside zone, and within the Outside zone?

