Question 31
Which two statements are correct about App-ID content updates? (Choose two.)
Question 32
Selecting the option to revert firewall changes will replace what settings?
Question 33
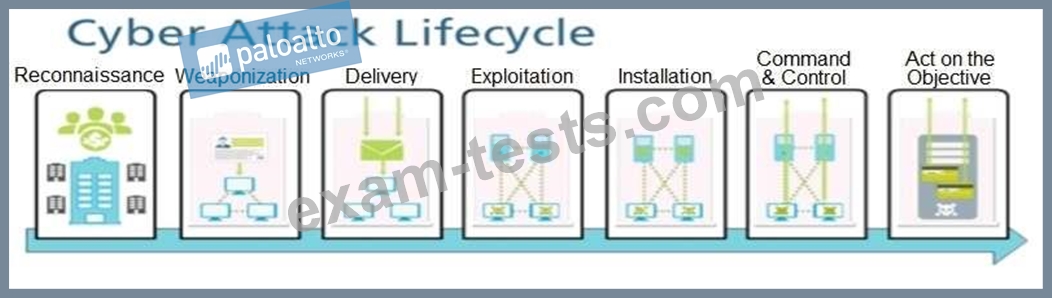
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can initiate malicious code against a targeted machine.

Question 34
You receive notification about new malware that infects hosts through malicious files transferred by FTP.
Which Security profile detects and protects your internal networks from this threat after you update your firewall's threat signature database?
Which Security profile detects and protects your internal networks from this threat after you update your firewall's threat signature database?
Question 35
Which statement is true regarding a Prevention Posture Assessment?

