Question 11
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can initiate malicious code against a targeted machine.
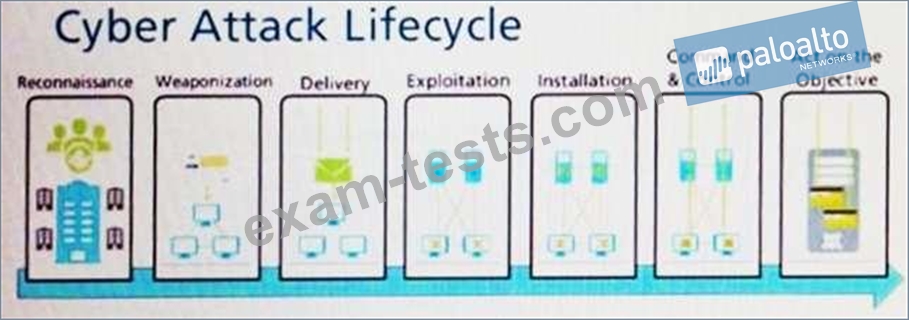

Question 12
An administrator notices that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would the administrator need to monitor and block to mitigate the malicious activity?
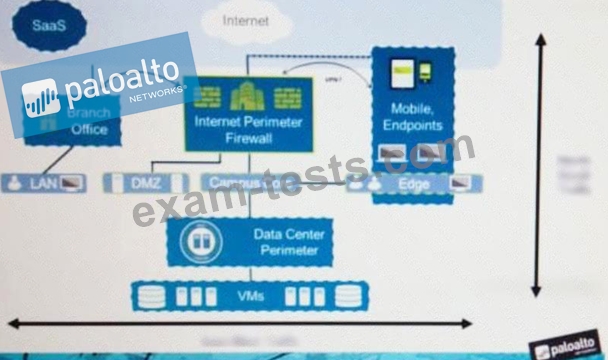

Question 13
Which action results in the firewall blocking network traffic with out notifying the sender?
Question 14
Access to which feature requires the PAN-OS Filtering license?
Question 15
Which two configuration settings shown are not the default? (Choose two.)
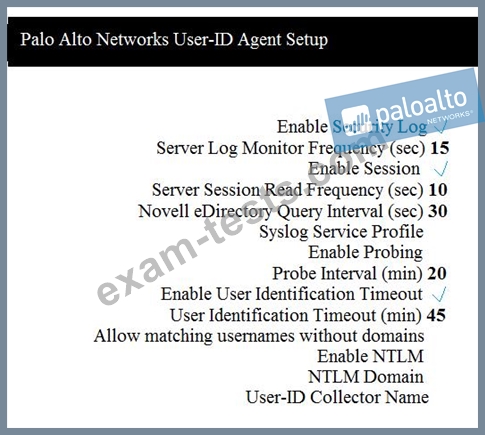

Premium Bundle
Newest PCNSA Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing PCNSA Exam! BraindumpsPass.com now offer the updated PCNSA exam dumps, the BraindumpsPass.com PCNSA exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com PCNSA pdf dumps with Exam Engine here:

