Question 1
Which feature would be useful for preventing traffic from hosting providers that place few restrictions on content, whose services are frequently used by attackers to distribute illegal or unethical material?
Question 2
Which data-plane processor layer of the graphic shown provides uniform matching for spyware and vulnerability exploits on a Palo Alto Networks Firewall?


Question 3
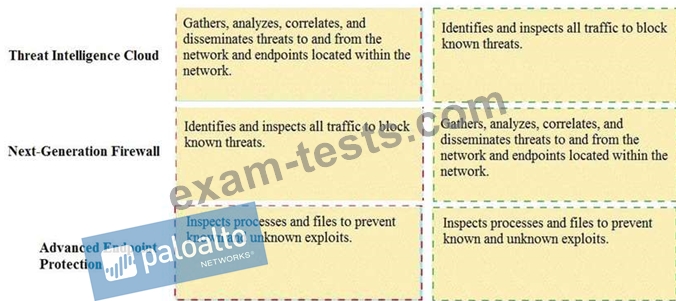
Match the Palo Alto Networks Security Operating Platform architecture to its description.


Question 4
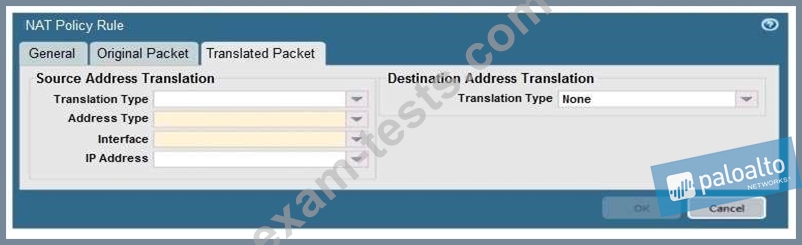
When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None?

Question 5
Which URL Filtering Profile action does not generate a log entry when a user attempts to access a URL?