Question 21
Which User-ID agent would be appropriate in a network with multiple WAN links, limited network bandwidth, and limited firewall management plane resources?
Question 22
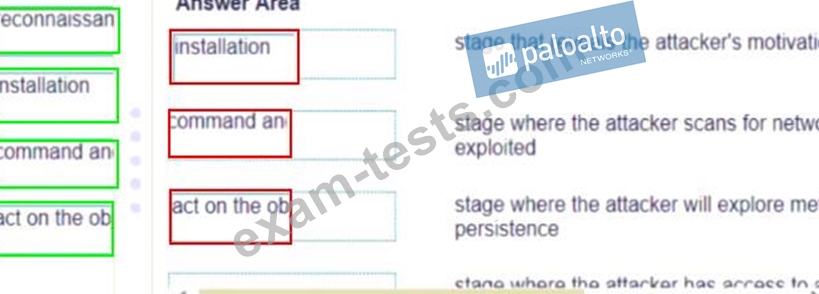
Match the cyber-attack lifecycle stage to its correct description.


Question 23
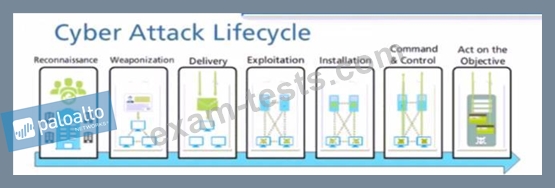
At which stage of the cyber-attack lifecycle would the attacker attach an infected PDF file to an email?

Question 24
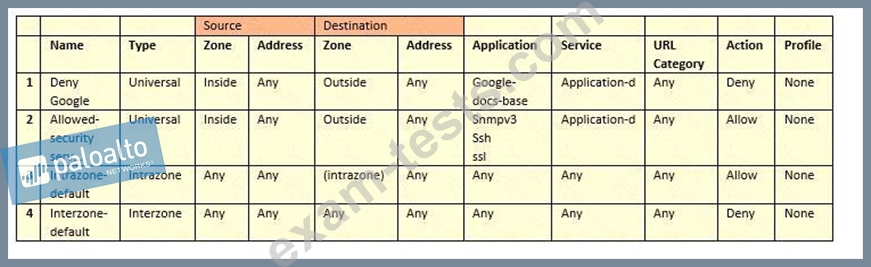
Based on the security policy rules shown, ssh will be allowed on which port?

Question 25
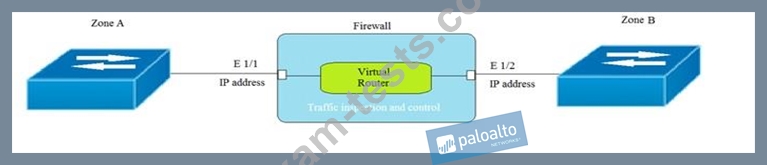
Given the topology, which zone type should zone A and zone B to be configured with?