Question 6
An administrator notices that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would the administrator need to monitor and block to mitigate the malicious activity?
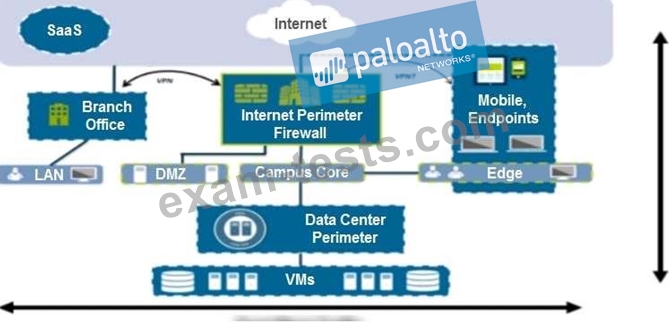

Question 7
An administrator wishes to follow best practices for logging traffic that traverses the firewall Which log setting is correct?
Question 8
Which user mapping method could be used to discover user IDs in an environment with multiple Windows domain controllers?
Question 9
What is the minimum timeframe that can be set on the firewall to check for new WildFire signatures?
Question 10
Selecting the option to revert firewall changes will replace what settings?

