Question 1
What are three valid actions in a File Blocking Profile? (Choose three)
Question 2
Refer to Exhibit:
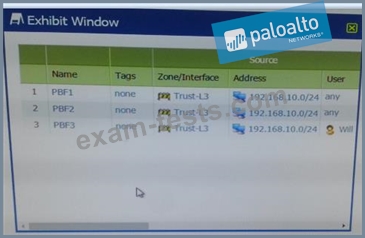

A firewall has three PDF rules and a default route with a next hop of 172.29.19.1 that is configured in the default VR. A user named XX-bes a PC with a 192.168.101.10 IP address.
He makes an HTTPS connection to 172.16.10.29.
What is the next hop IP address for the HTTPS traffic from Wills PC.


A firewall has three PDF rules and a default route with a next hop of 172.29.19.1 that is configured in the default VR. A user named XX-bes a PC with a 192.168.101.10 IP address.
He makes an HTTPS connection to 172.16.10.29.
What is the next hop IP address for the HTTPS traffic from Wills PC.
Question 3
When using certificate authentication for firewall administration, which method is used for authorization?
Question 4
Which feature must you configure to prevent users form accidentally submitting their corporate credentials to a phishing website?
Question 5
Refer to the exhibit.

Which certificates can be used as a Forwarded Trust certificate?

Which certificates can be used as a Forwarded Trust certificate?

