Question 11
At which stage of the cyber-attack lifecycle would the attacker attach an infected PDF file to an email?
Question 12
Which two methods can be used to mitigate resource exhaustion of an application server?
(Choose two)
(Choose two)
Question 13
An administrator needs to determine why users on the trust zone cannot reach certain websites. The only information available is shown on the following image. Which configuration change should the administrator make?
A)
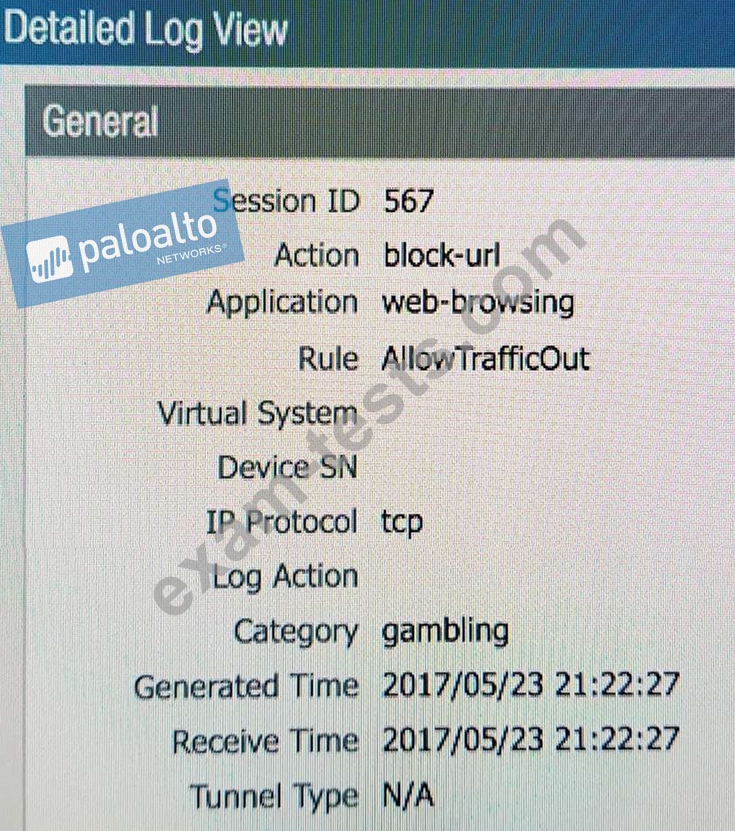
B)
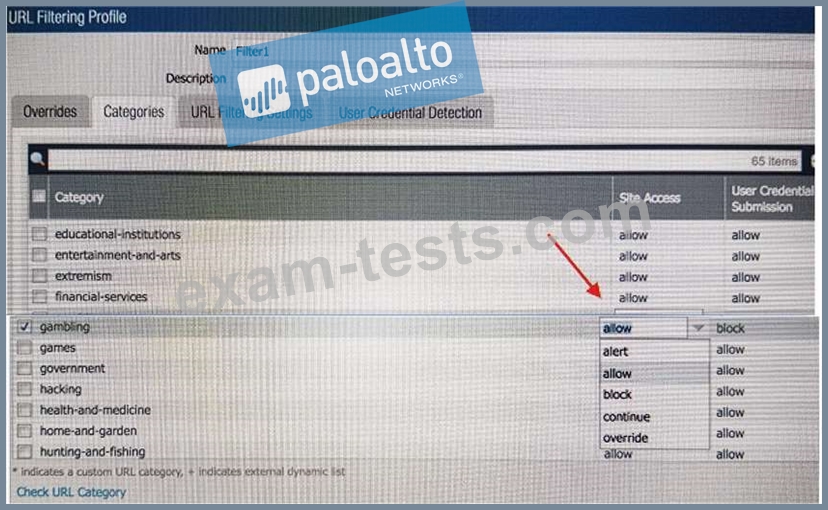
C)
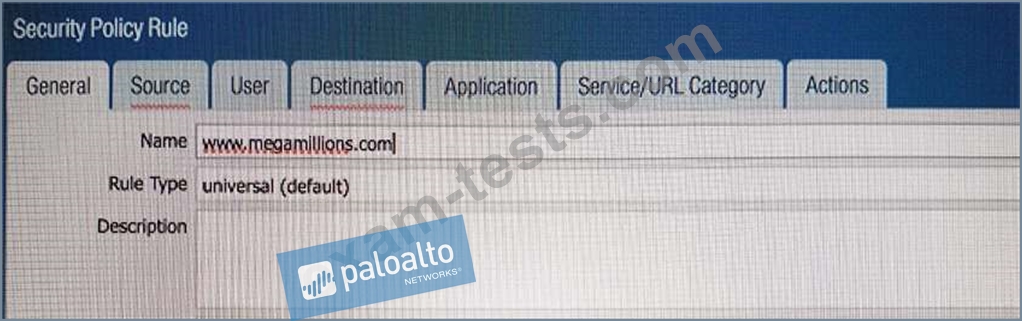
D)

E)
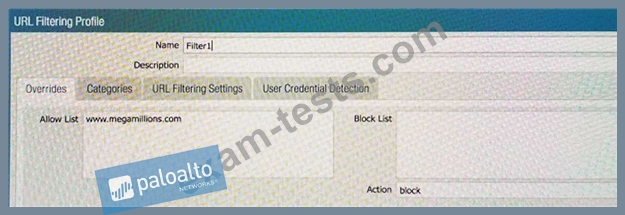
A)

B)

C)

D)

E)

Question 14
Which three authentication services can administrator use to authenticate admins into the Palo Alto Networks NGFW without defining a corresponding admin account on the local firewall? (Choose three.)
Question 15
A company is upgrading its existing Palo Alto Networks firewall from version 7.0.1 to 7.0.4.
Which three methods can the firewall administrator use to install PAN-OS 7.0.4 across the enterprise?( Choose three)
Which three methods can the firewall administrator use to install PAN-OS 7.0.4 across the enterprise?( Choose three)

