Question 6
If the firewall is configured for credential phishing prevention using the "Domain Credential Filter" method, which login will be detected as credential theft?
Question 7
Which option describes the operation of the automatic commit recovery feature?
Question 8
Where can an administrator see both the management plane and data plane CPU utilization in the WebUI?
Question 9
How does Panorama prompt VMWare NSX to quarantine an infected VM?
Question 10
Refer to the exhibit. An administrator is using DNAT to map two servers to a single public IP address. Traffic will be steered to the specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and HOST B (10.1.1.101) receives SSH traffic.)
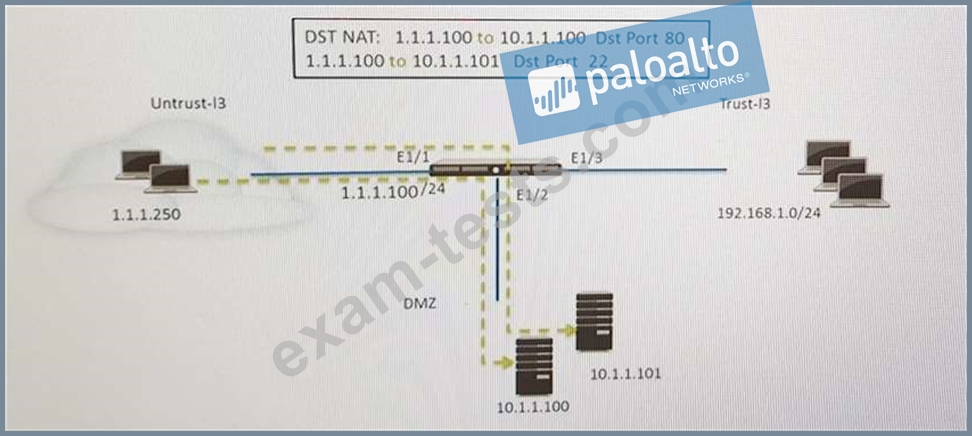
Which two security policy rules will accomplish this configuration? (Choose two.)

Which two security policy rules will accomplish this configuration? (Choose two.)

