Question 186
A penetration tester has been asked to conduct OS fingering with Nmap using a company-provided text file that contains a list of IP addresses. Which of the following are needed to conduct this scan? (Choose two.).
Question 187
Which of the following tools is used to perform a credential brute force attack?
Question 188
A penetration tester executes the following commands:
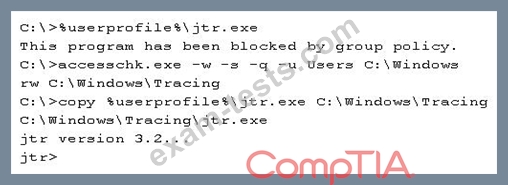
Which of the following is a local host vulnerability that the attacker is exploiting?

Which of the following is a local host vulnerability that the attacker is exploiting?
Question 189
When performing compliance-based assessments, which of the following is the MOST important Key consideration?
Question 190
A penetration tester has been asked to conduct OS fingering with Nmap using a company-provided text file that contains a list of IP addresses. Which of the following are needed to conduct this scan? (Choose two.).
Premium Bundle
Newest PT0-001 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing PT0-001 Exam! BraindumpsPass.com now offer the updated PT0-001 exam dumps, the BraindumpsPass.com PT0-001 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com PT0-001 pdf dumps with Exam Engine here:

