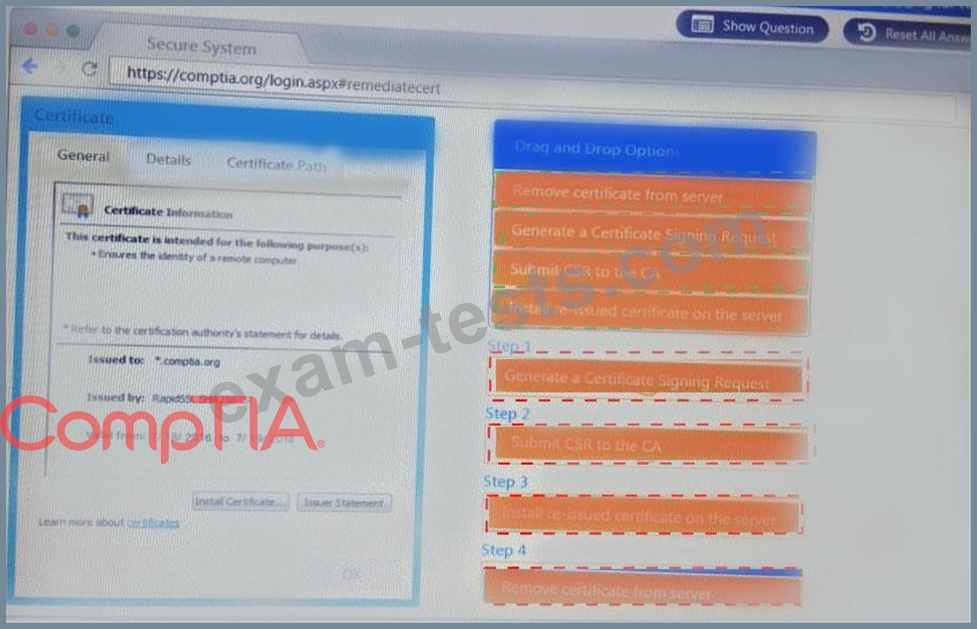
Question 196
Performance based
You are a penetration Inter reviewing a client's website through a web browser.
Instructions:
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate source or cookies.
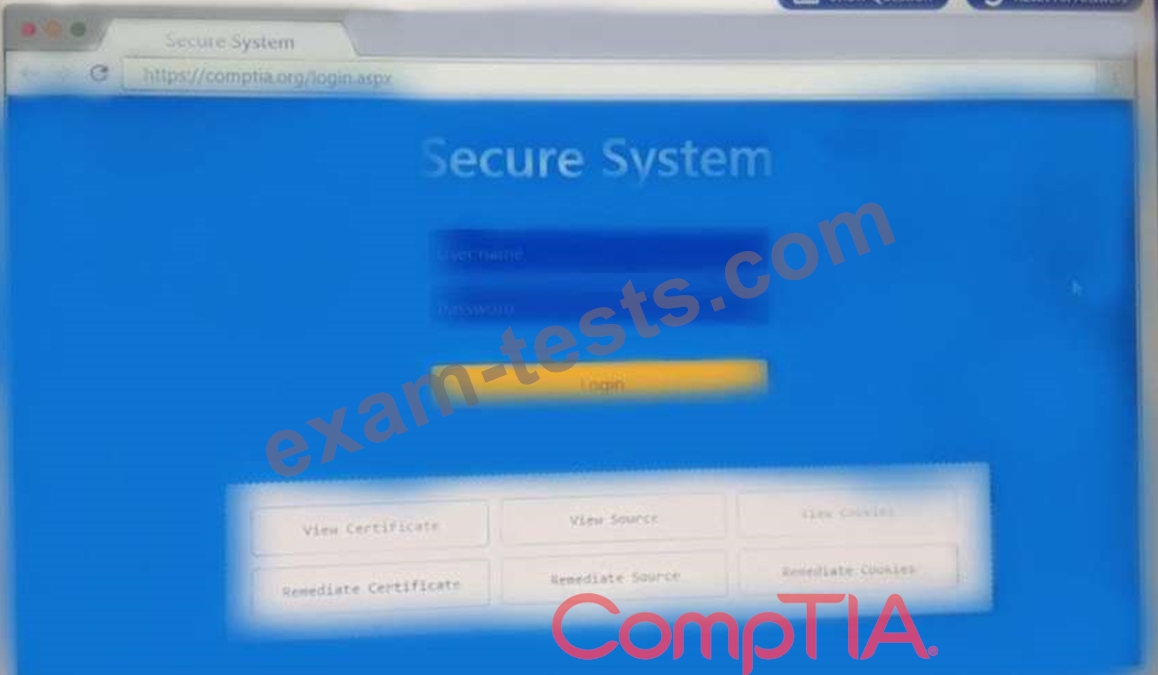
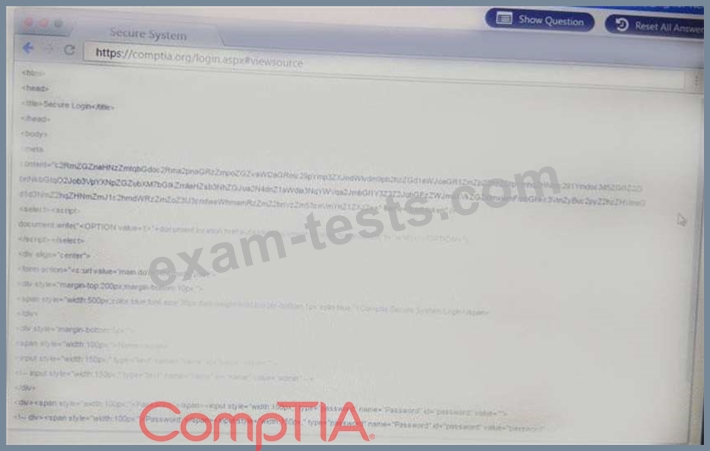

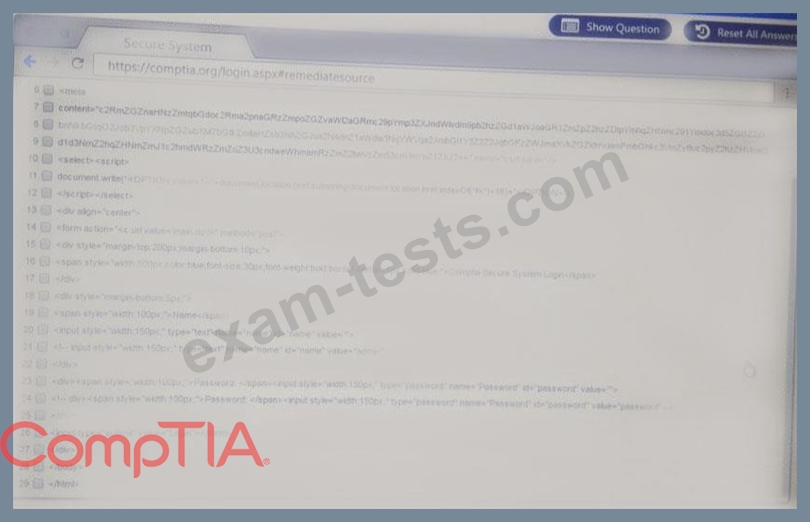
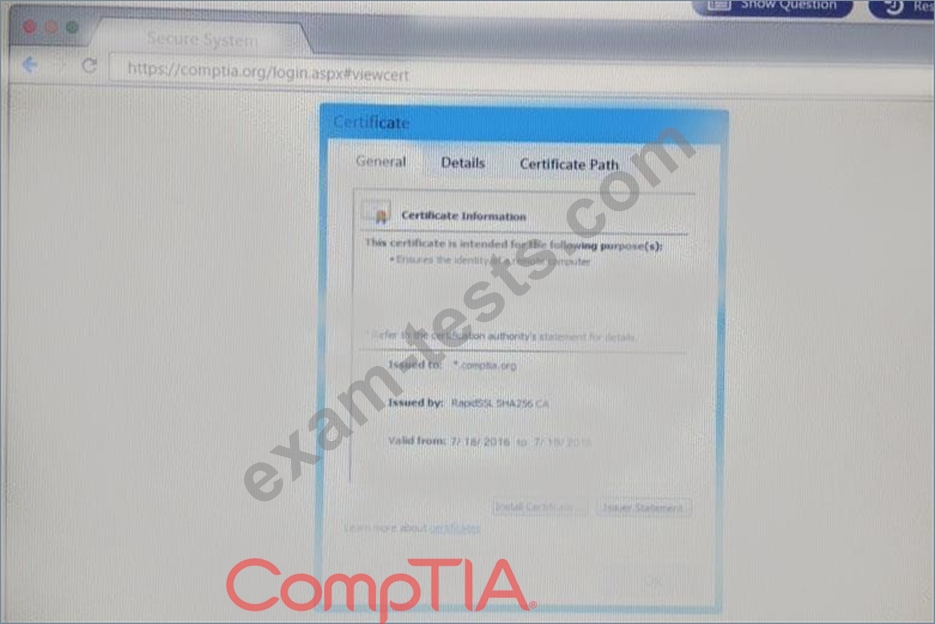
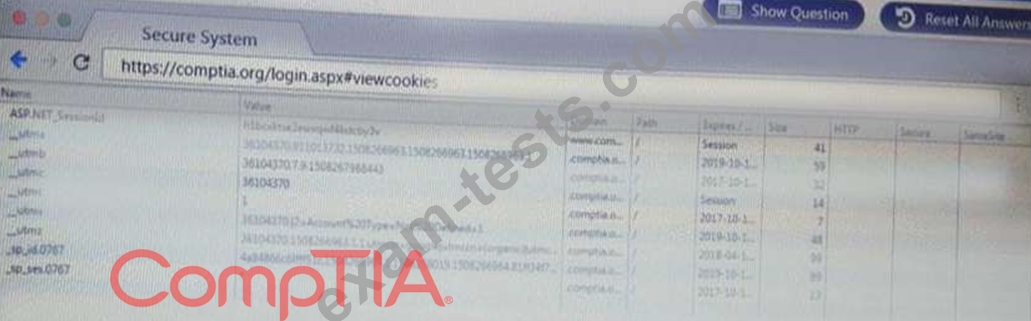
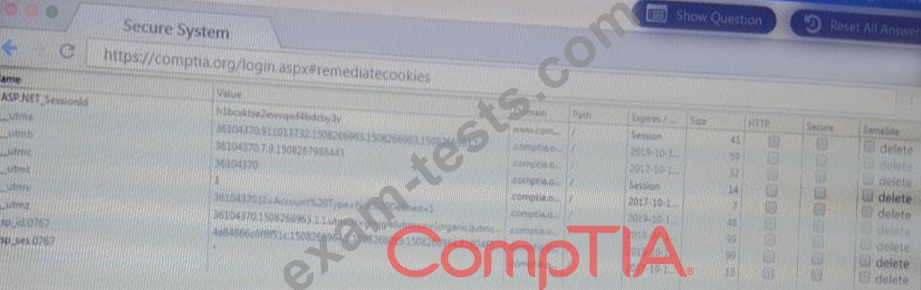
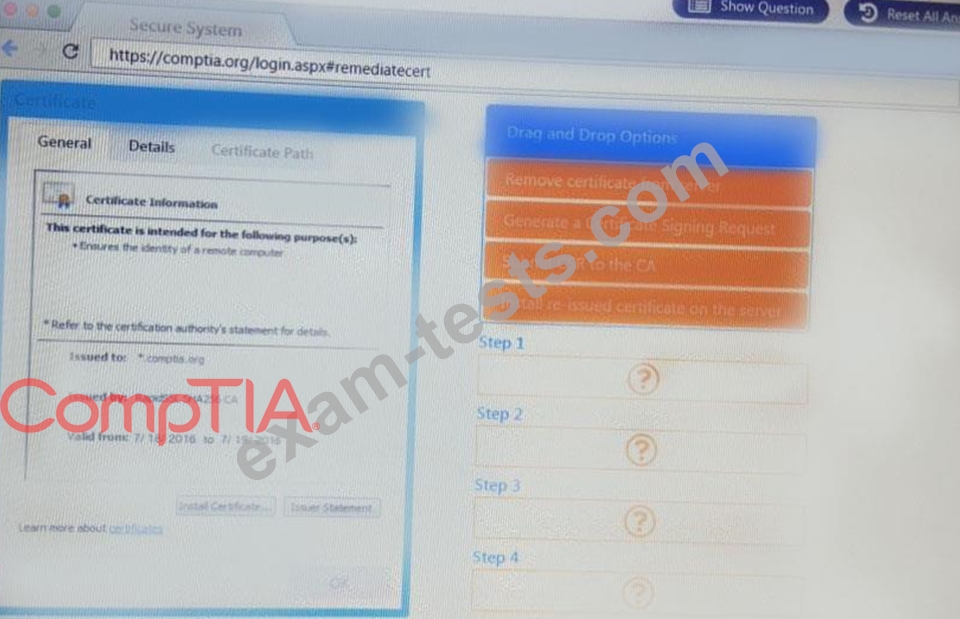
You are a penetration Inter reviewing a client's website through a web browser.
Instructions:
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate source or cookies.








Question 197
Black box penetration testing strategy provides the tester with:
Question 198
Which of the following tools is used to perform a credential brute force attack?
Question 199
A penetration tester is designing a phishing campaign and wants to build list of users (or the target organization. Which of the following techniques would be the MOST appropriate? (Select TWO)
Question 200
A penetration tester observes that several high-numbered ports are listening on a public web server.
However, the system owner says the application only uses port 443. Which of the following would be BEST to recommend?
However, the system owner says the application only uses port 443. Which of the following would be BEST to recommend?