Question 206
A security consultant is trying to attack a device with a previously identified user account.
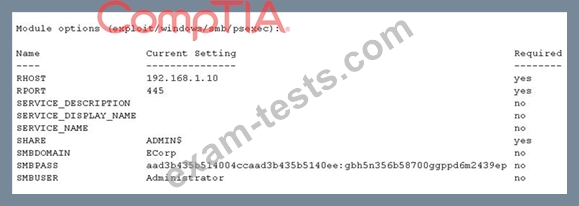
Which of the following types of attacks is being executed?

Which of the following types of attacks is being executed?
Question 207
Given the following script:
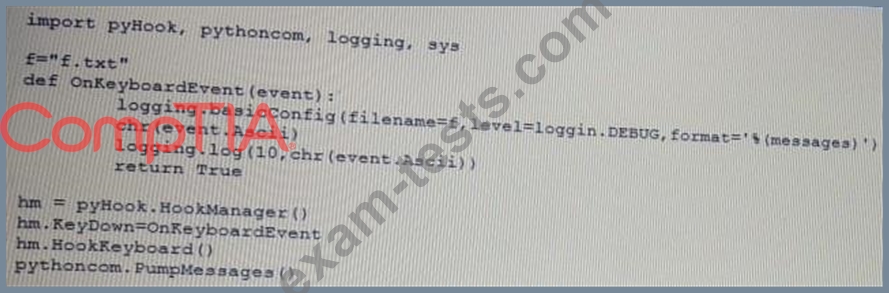
Which of the following BEST describes the purpose of this script?

Which of the following BEST describes the purpose of this script?
Question 208
A client requests that a penetration tester emulate a help desk technician who was recently laid off. Which of the following BEST describes the abilities of the threat actor?

