Question 76
A company requested a penetration tester review the security of an in-house-developed Android application. The penetration tester received an APK file to support the assessment. The penetration tester wants to run SAST on the APK file. Which of the following preparatory steps must the penetration tester do FIRST? (Select TWO)
Question 77
During an internal penetration test, several multicast and broadcast name resolution requests are observed traversing the network. Which of the following tools could be used to impersonate network resources and collect authentication requests?
Question 78
Given the following Python script:
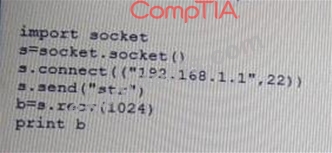
Which of the following actions will it perform?

Which of the following actions will it perform?
Question 79
A penetration tester wants to check manually if a "ghost" vulnerability exists in a system. Which of the following methods is the correct way to validate the vulnerability?
Question 80
During a full-scope security assessment, which of the following is a prerequisite to social engineer a target by physically engaging them?

