Question 86
Which of the following excerpts would come from a corporate policy?
Question 87
Black box penetration testing strategy provides the tester with:
Question 88
A penetration tester is reviewing a Zigbee Implementation for security issues. Which of the following device types is the tester MOST likely testing?
Question 89
A penetration tester is reviewing the following output from a wireless sniffer:
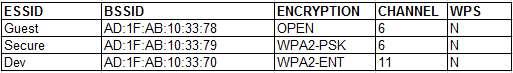
Which of the following can be extrapolated from the above information?

Which of the following can be extrapolated from the above information?
Question 90
After successfully enumerating users on an Active Directory domain controller using enum4linux a penetration tester wants to conduct a password-guessing attack Given the below output:
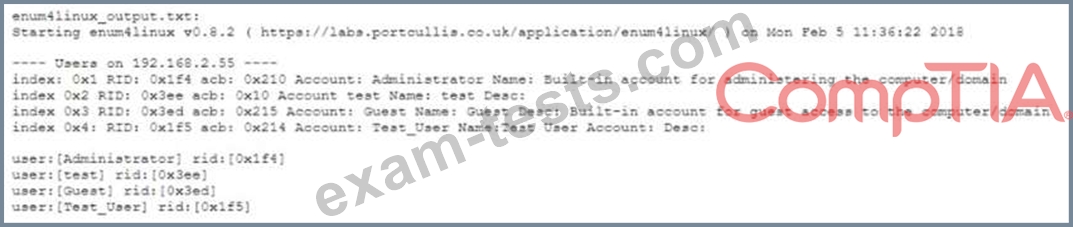
Which of the following can be used to extract usernames from the above output prior to conducting the attack?

Which of the following can be used to extract usernames from the above output prior to conducting the attack?

