Question 66
A penetration tester has been hired to perform a penetration test for an organization. Which of the following is indicative of an error-based SQL injection attack?
Question 67
Performance based
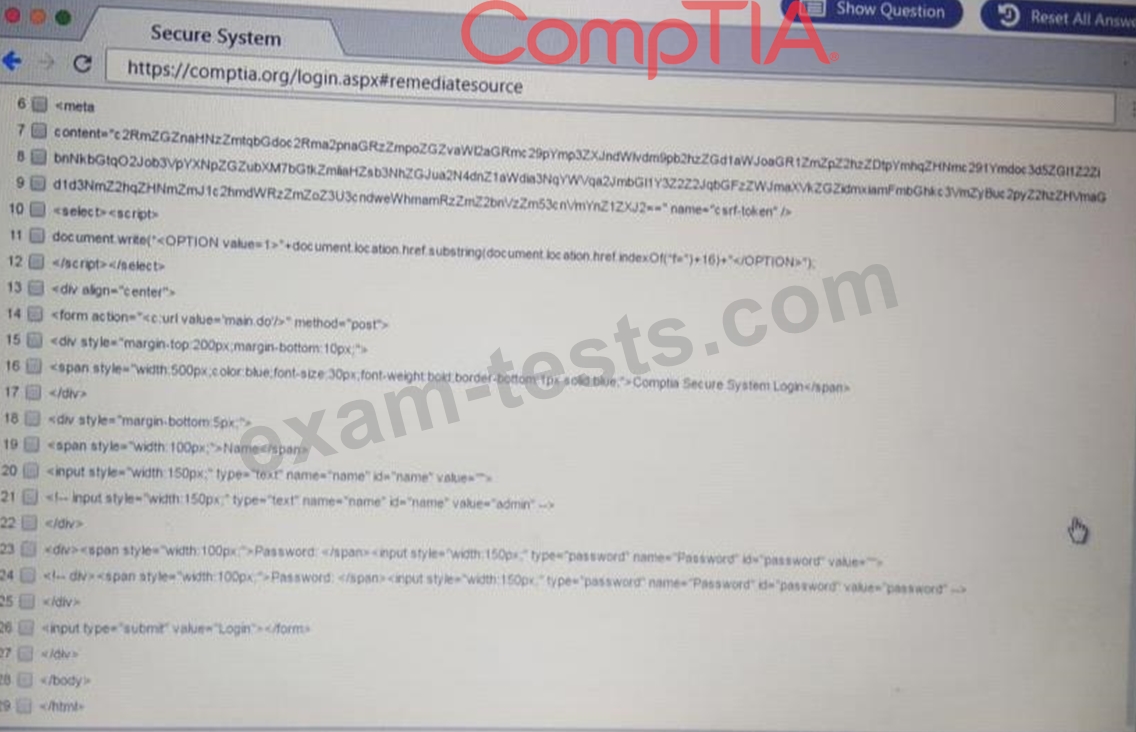
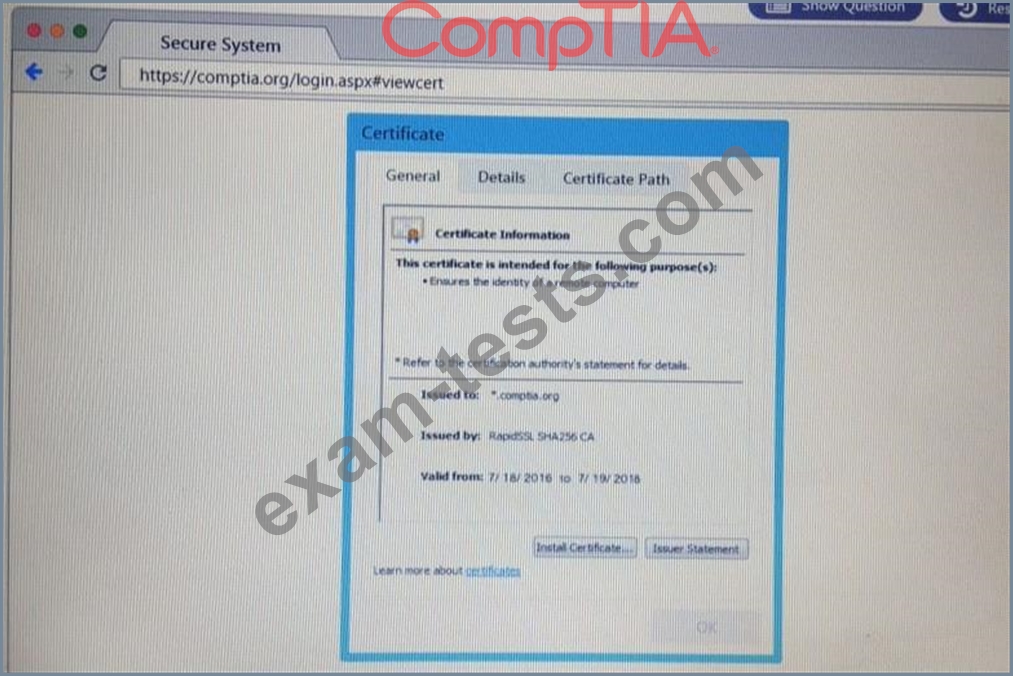
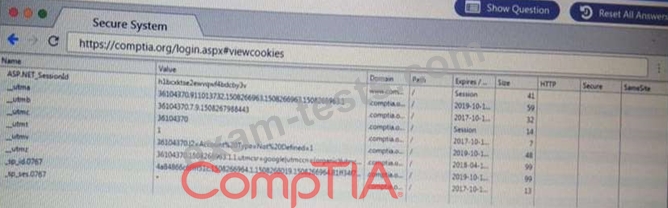
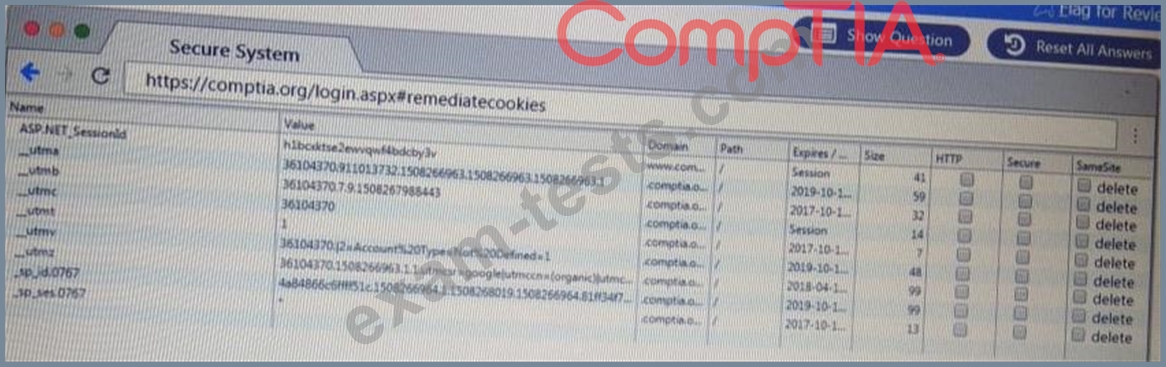
You are a penetration Inter reviewing a client's website through a web browser.
Instructions:
Review all components of the website through the browser to determine if vulnerabilities are present.
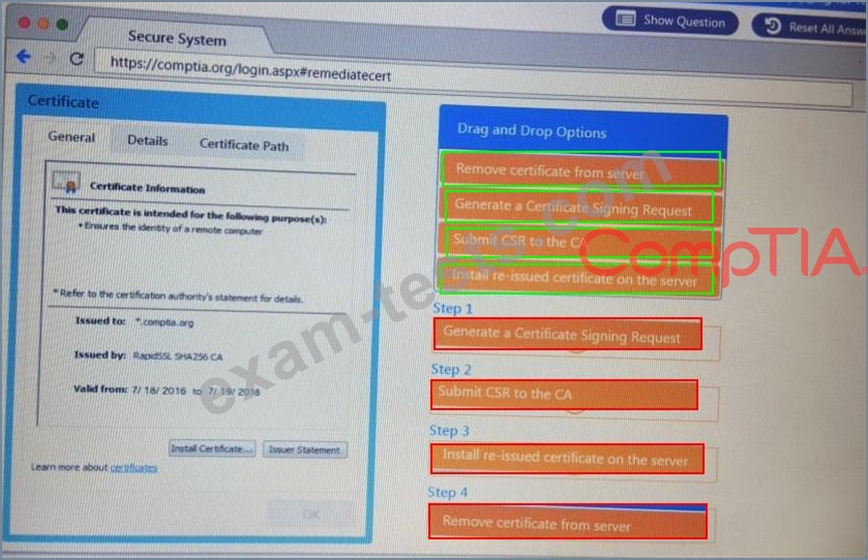
Remediate ONLY the highest vulnerability from either the certificate source or cookies.
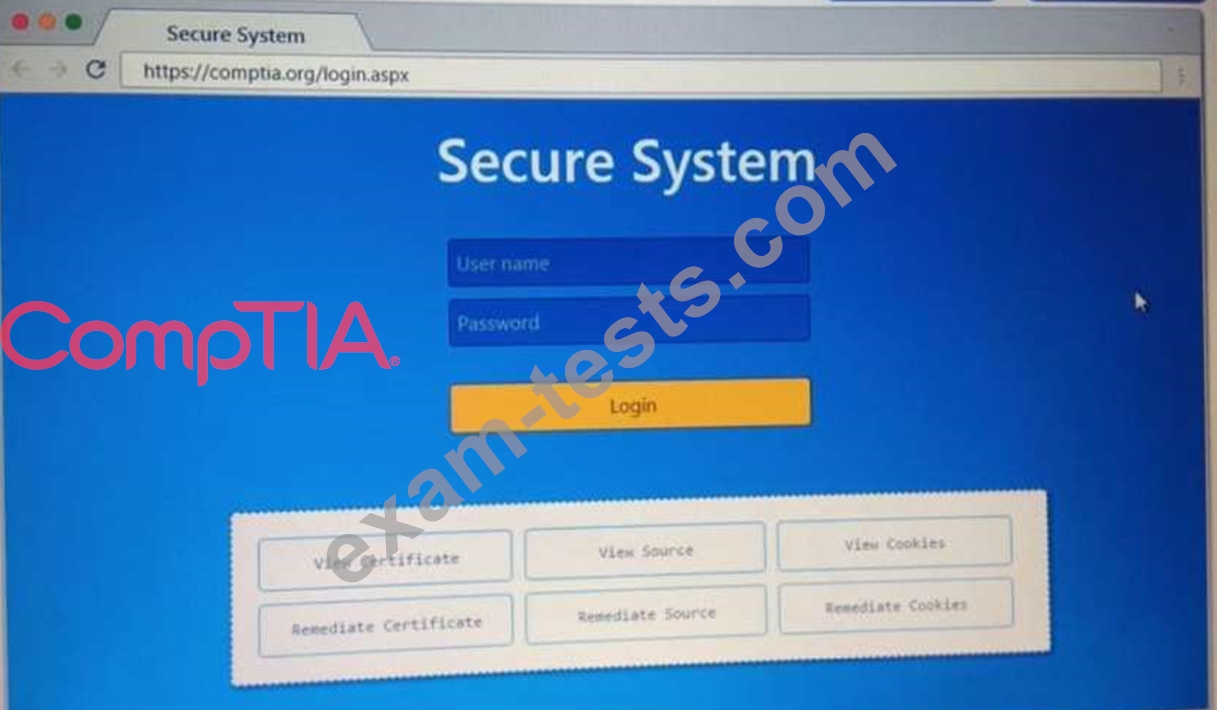
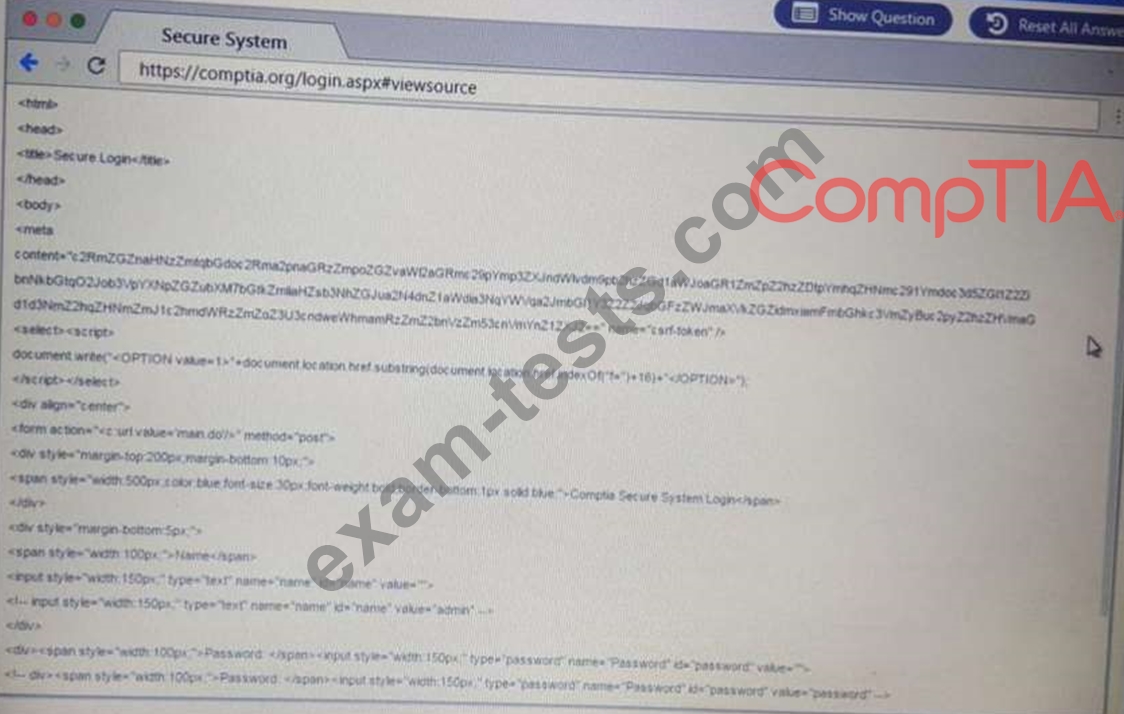
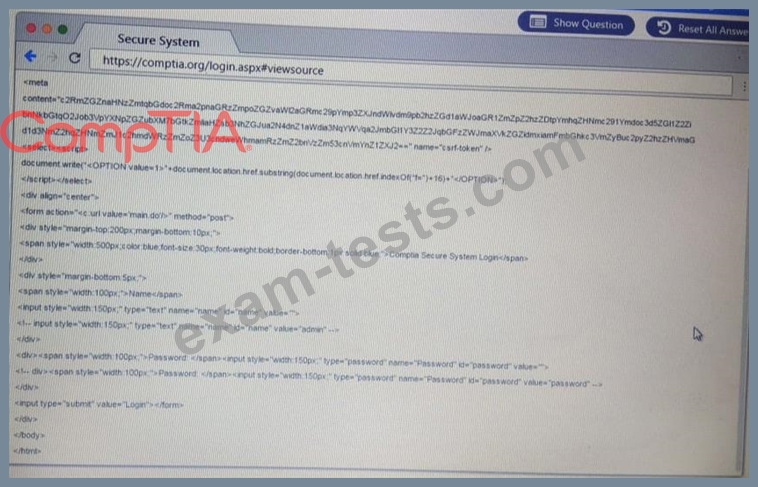
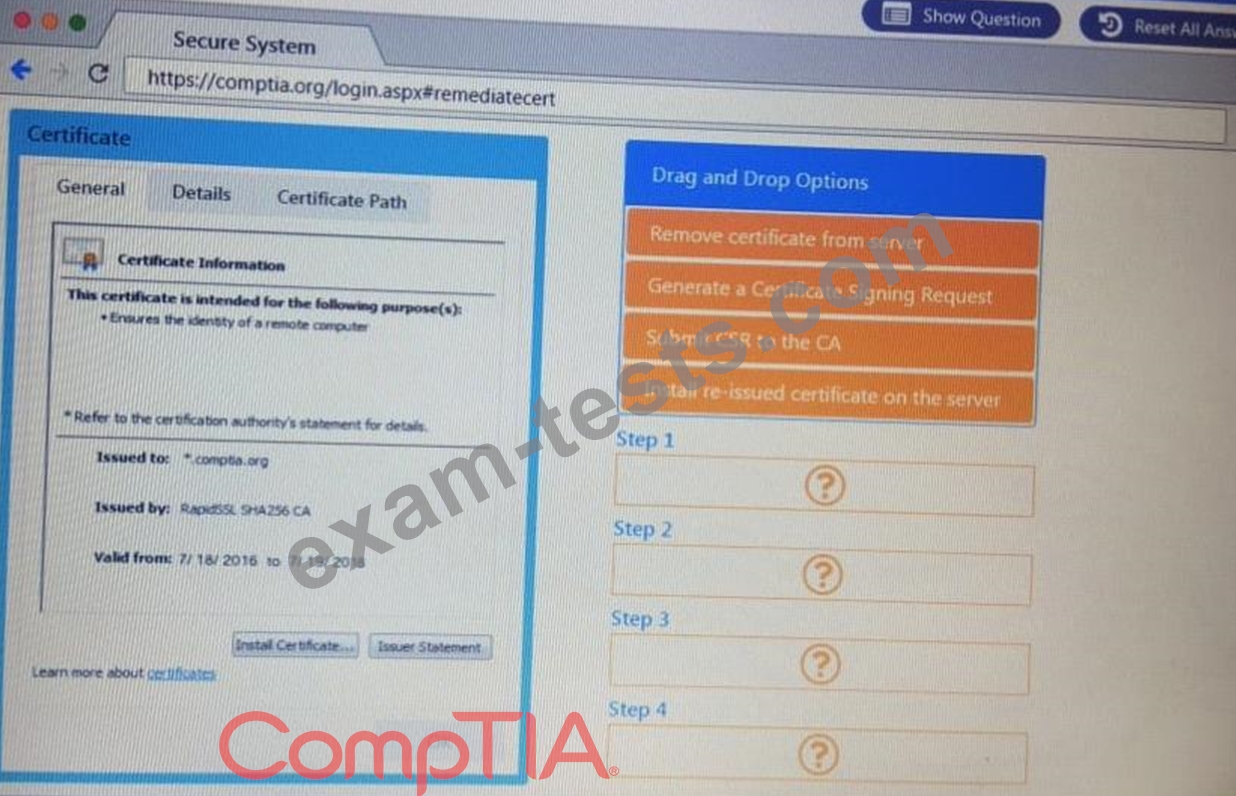
You are a penetration Inter reviewing a client's website through a web browser.
Instructions:
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate source or cookies.








Question 68
Click the exhibit button.
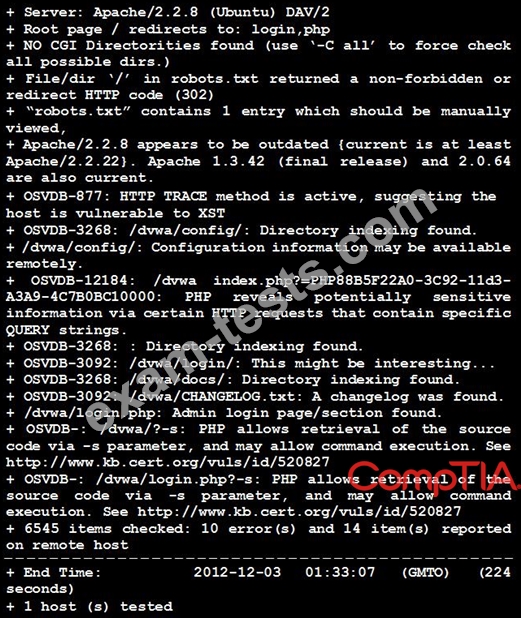
Given the Nikto vulnerability, scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Choose two.)

Given the Nikto vulnerability, scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Choose two.)
Question 69
A penetration tester has gained access to a marketing employee's device. The penetration tester wants to ensure that if the access is discovered, control of the device can be regained. Which of the following actions should the penetration tester use to maintain persistence to the device? (Select TWO.)
Question 70
Which of the following CPU register does the penetration tester need to overwrite in order to exploit a simple butter overflow?