Question 106
A penetration tester ran an Nmap scan against a target and received the following output:
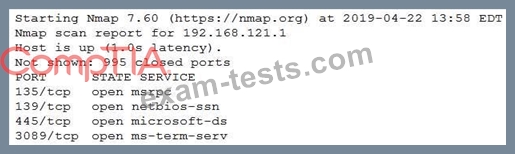
Which of the following commands would be best for the penetration tester to execute NEXT to discover any weaknesses or vulnerabilities?

Which of the following commands would be best for the penetration tester to execute NEXT to discover any weaknesses or vulnerabilities?
Question 107
A penetration tester is exploiting the use of default public and private community strings Which of the following protocols is being exploited?
Question 108
A tester has determined that null sessions are enabled on a domain controller. Which of the following attacks can be performed to leverage this vulnerability?
Question 109
A penetration tester was able to retrieve the initial VPN user domain credentials by phishing a member of the IT department. Afterward, the penetration tester obtained hashes over the VPN and easily cracked them using a dictionary attack Which of the following remediation steps should be recommended? (Select THREE)
Question 110
A penetration tester identifies the following findings during an external vulnerability scan:
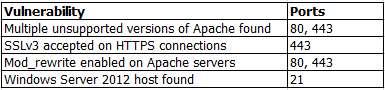
Which of the following attack strategies should be prioritized from the scan results above?

Which of the following attack strategies should be prioritized from the scan results above?

