Question 111
A penetration tester reviews the scan results of a web application. Which of the following vulnerabilities is MOST critical and should be prioritized for exploitation?
Question 112
A penetration tester discovers Heartbleed vulnerabilities in a target network Which of the following impacts would be a result of exploiting this vulnerability?
Question 113
Click the exhibit button.
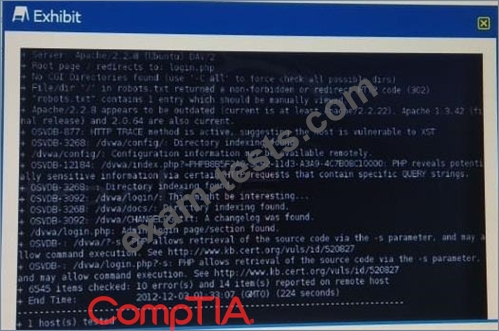
Given the Nikto vulnerability scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Select TWO)

Given the Nikto vulnerability scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Select TWO)
Question 114
A penetration tester wants to check manually if a "ghost" vulnerability exists in a system. Which of the following methods is the correct way to validate the vulnerability?
Question 115
A penetration tester is preparing to conduct API testing. Which of the following would be MOST helpful in preparing for this engagement?

