Question 131
A security analyst was provided with a detailed penetration report, which was performed against the organization's DMZ environment. It was noted on the report that a finding has a CVSS base score of 10.0.
Which of the following levels of difficulty would be required to exploit this vulnerability?
Which of the following levels of difficulty would be required to exploit this vulnerability?
Question 132
A penetration tester has compromised a host. Which of the following would be the correct syntax to create a Netcat listener on the device?
Question 133
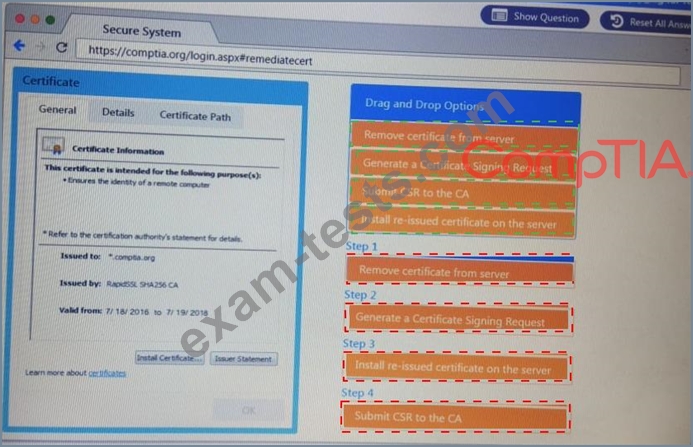
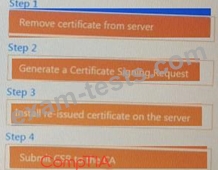
DRAG DROP
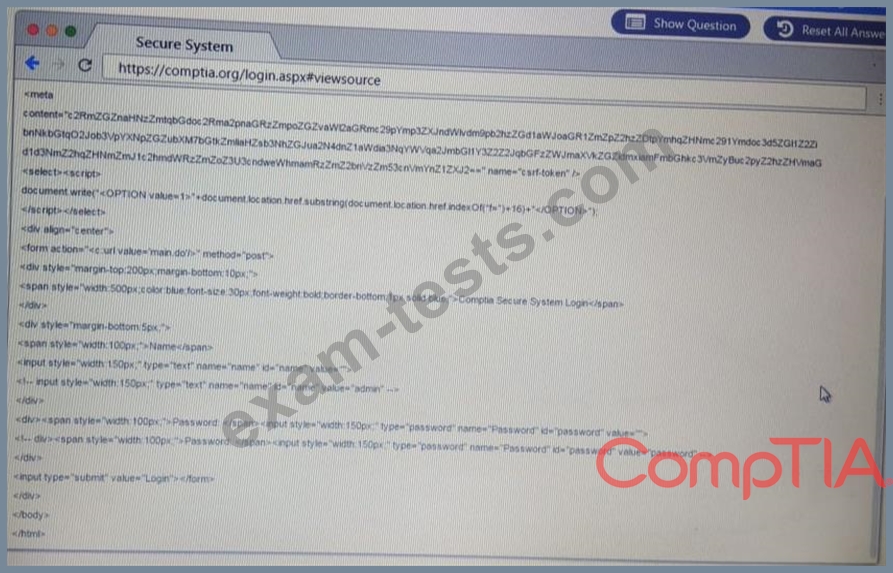
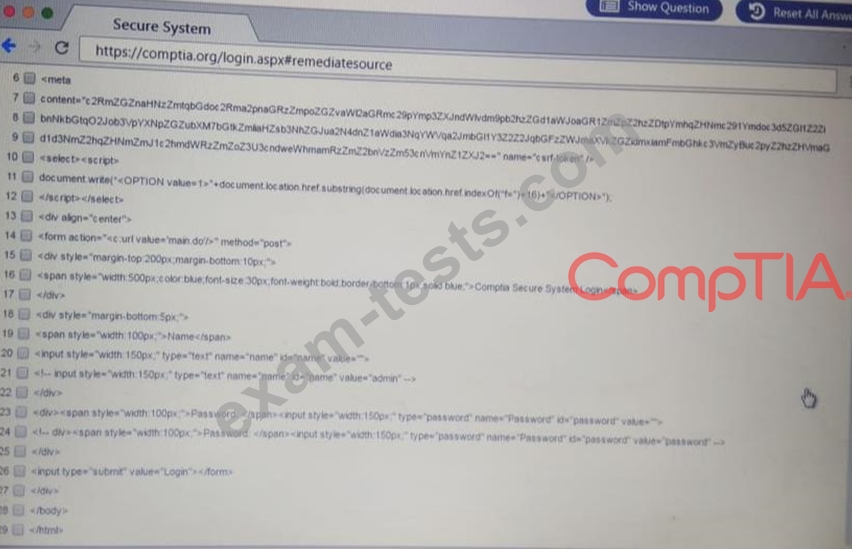
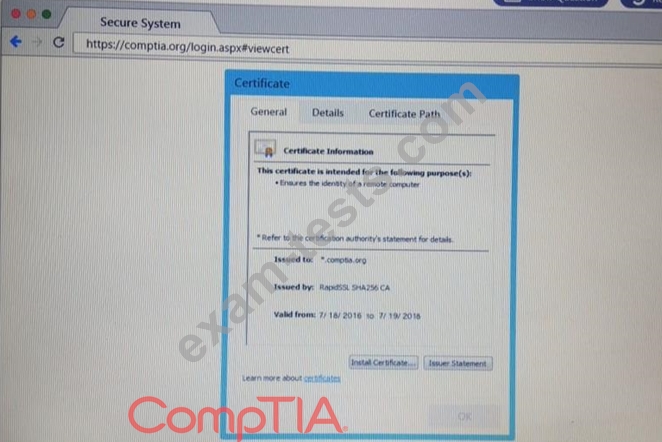
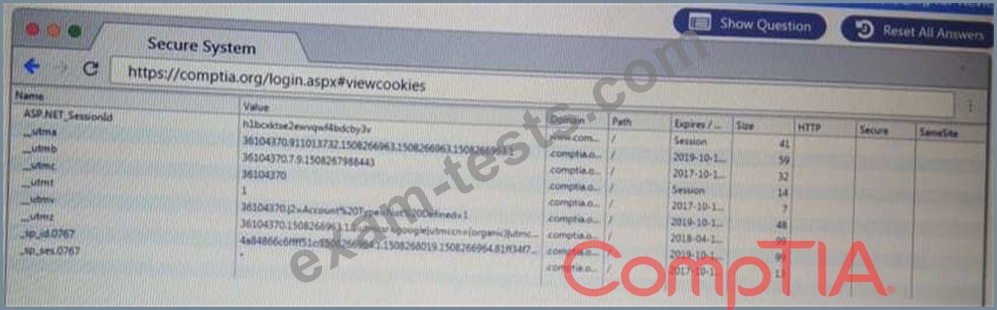
Performance based
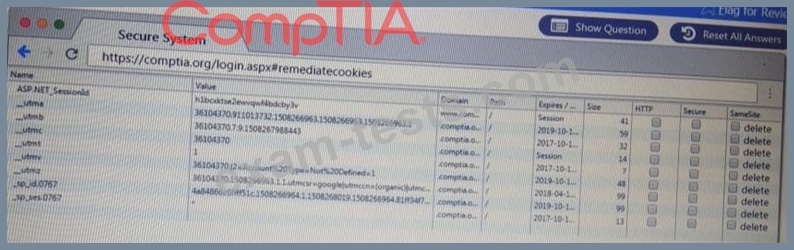
You are a penetration Inter reviewing a client's website through a web browser.
Instructions:
Review all components of the website through the browser to determine if vulnerabilities are present.
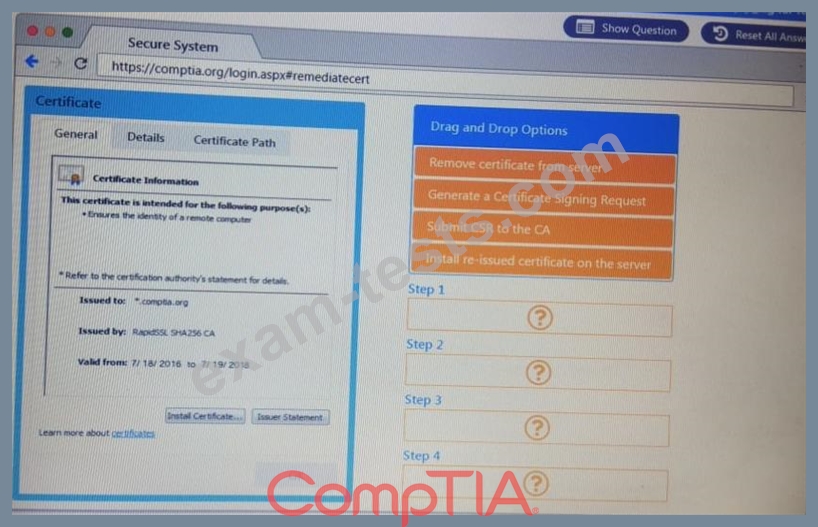
Remediate ONLY the highest vulnerability from either the certificate source or cookies.
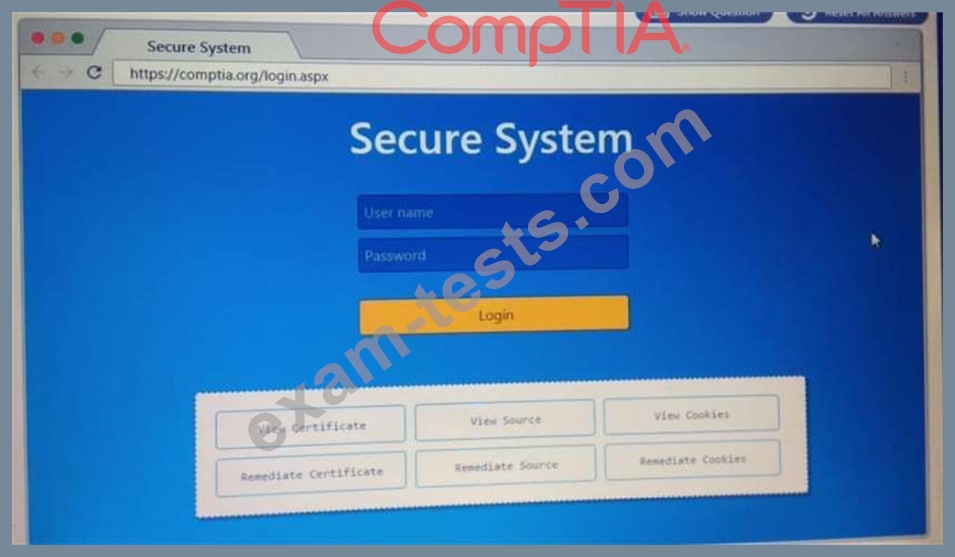
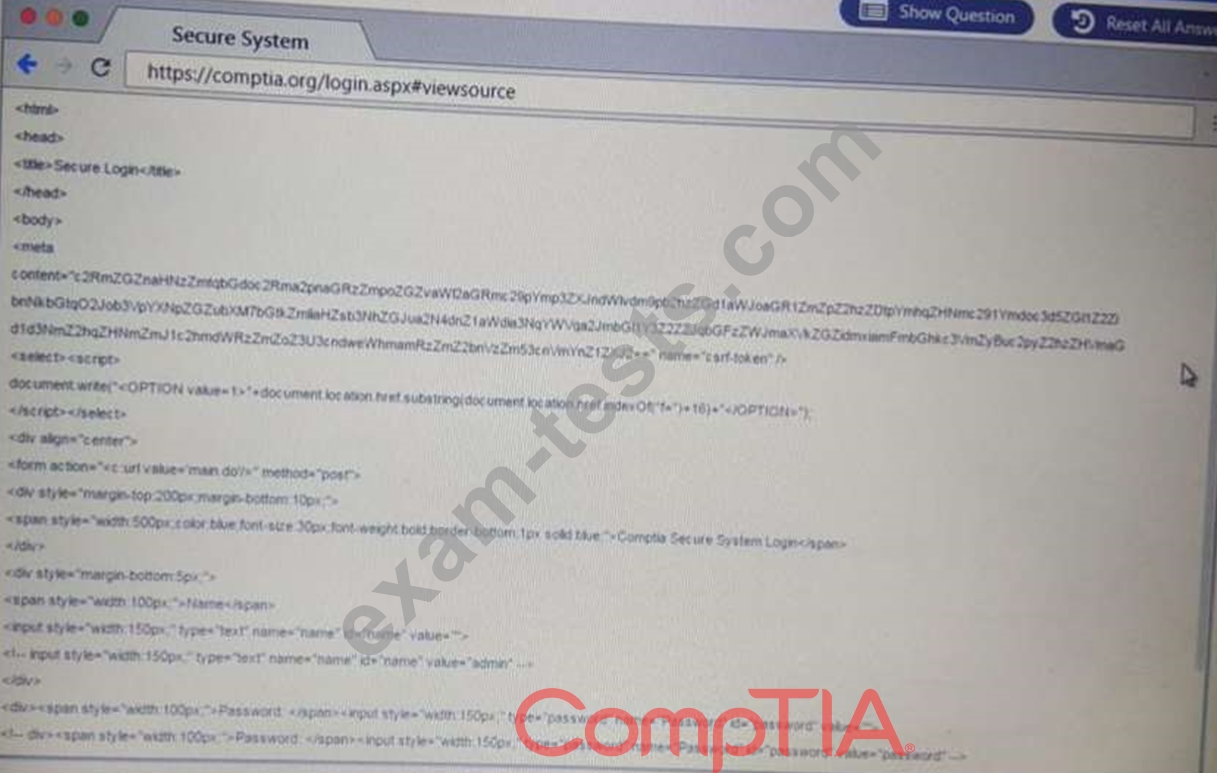
Performance based
You are a penetration Inter reviewing a client's website through a web browser.
Instructions:
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate source or cookies.








Question 134
While reviewing logs, a web developer notices the following user input string in a field:
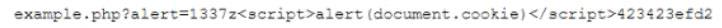
Which of the following types of attacks was done to the website?
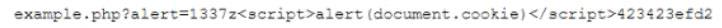
Which of the following types of attacks was done to the website?
Question 135
A penetration tester is checking a script to determine why some basic math errors are persisting. The expected result was the program outputting "True".
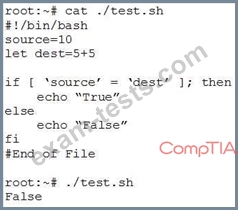
Given the output from the console above, which of the following explains how to correct the errors in the script?
(Choose two.)

Given the output from the console above, which of the following explains how to correct the errors in the script?
(Choose two.)