Question 211
A security analyst has uncovered a suspicious request in the logs for a web application.
Given the following URL:
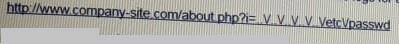
Given the following URL:

Question 212
A malicious user wants to perform an MITM attach on a computer. The computer network configuration is given below:
IP: 192.168.1.20
NETMASK: 255.255.255.0
DEFAULT GATEWAY: 192.168.1.254
DHCP: 192.168.1.253
DNS: 192.168.10.10, 192.168.20.10
Which of the following commands should the malicious user execute to perform the MITM attack?
IP: 192.168.1.20
NETMASK: 255.255.255.0
DEFAULT GATEWAY: 192.168.1.254
DHCP: 192.168.1.253
DNS: 192.168.10.10, 192.168.20.10
Which of the following commands should the malicious user execute to perform the MITM attack?
Question 213
Which of the following BEST explains why it is important to maintain confidentiality of any identified findings when performing a penetration test?
Question 214
During an internal network penetration test the tester is able to compromise a Windows system and recover the NTLM hash for a local wrltsrnAdrain account Attempting to recover the plaintext password by cracking the hash has proved to be unsuccessful, and the tester has decided to try a pass-the-hash attack to see if the credentials are reused on other in-scope systems Using the Medusa tool the tester attempts to authenticate to a list of systems, including the originally compromised host, with no success Given the output below:
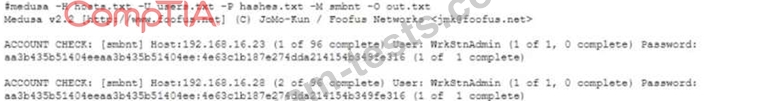
Which of the following Medusa commands would potentially provide better results?

Which of the following Medusa commands would potentially provide better results?
Question 215
A penetration tester is perform initial intelligence gathering on some remote hosts prior to conducting a vulnerability < The tester runs the following command nmap -D 192.168.1.1,192.168.1.2,192.168.1.3 -sV -o -max rate 2 192. 168.130 Which ol the following BEST describes why multiple IP addresses are specified?

