Question 46
A penetration tester has been hired to configure and conduct authenticated scans of all the servers on a software company's network. Which of the following accounts should the tester use to return the MOST results?
Question 47
A penetration tester is looking for a vulnerability that enables attackers to open doors via a specialized TCP service that is used for a physical access control system. The service exists on more than 100 different hosts, so the tester would like to automate the assessment. Identification requires the penetration tester to:
* Have a full TCP connection
* Send a "hello" payload
* Walt for a response
* Send a string of characters longer than 16 bytes
Which of the following approaches would BEST support the objective?
* Have a full TCP connection
* Send a "hello" payload
* Walt for a response
* Send a string of characters longer than 16 bytes
Which of the following approaches would BEST support the objective?
Question 48
A penetration tester runs the unshadow command on a machine. Which of the following tools will the tester most likely use NEXT?
Question 49
A penetration tester ran the following commands on a Windows server:
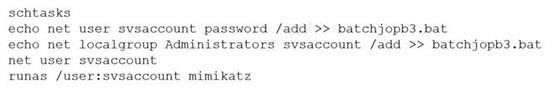
Which of the following should the tester do AFTER delivering the final report?

Which of the following should the tester do AFTER delivering the final report?
Question 50
A penetration tester has identified several newly released CVEs on a VoIP call manager. The scanning tool the tester used determined the possible presence of the CVEs based off the version number of the service. Which of the following methods would BEST support validation of the possible findings?

