Question 31
A penetration tester conducted a discovery scan that generated the following:
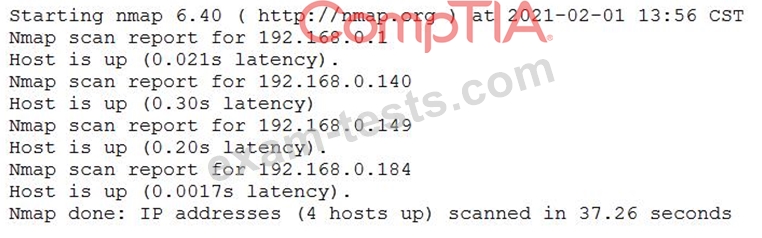
Which of the following commands generated the results above and will transform them into a list of active hosts for further analysis?

Which of the following commands generated the results above and will transform them into a list of active hosts for further analysis?
Question 32
A company is concerned that its cloud service provider is not adequately protecting the VMs housing its software development. The VMs are housed in a datacenter with other companies sharing physical resources. Which of the following attack types is MOST concerning to the company?
Question 33
A penetration tester is working on a scoping document with a new client. The methodology the client uses includes the following:
Pre-engagement interaction (scoping and ROE)
Intelligence gathering (reconnaissance)
Threat modeling
Vulnerability analysis
Exploitation and post exploitation
Reporting
Which of the following methodologies does the client use?
Pre-engagement interaction (scoping and ROE)
Intelligence gathering (reconnaissance)
Threat modeling
Vulnerability analysis
Exploitation and post exploitation
Reporting
Which of the following methodologies does the client use?
Question 34
A penetration tester runs the following command on a system:
find / -user root -perm -4000 -print 2>/dev/null
Which of the following is the tester trying to accomplish?
find / -user root -perm -4000 -print 2>/dev/null
Which of the following is the tester trying to accomplish?
Question 35
Which of the following tools provides Python classes for interacting with network protocols?

