Question 41
A penetration tester who is conducting a web-application test discovers a clickjacking vulnerability associated with a login page to financial dat a. Which of the following should the tester do with this information to make this a successful exploit?
Question 42
The results of an Nmap scan are as follows:
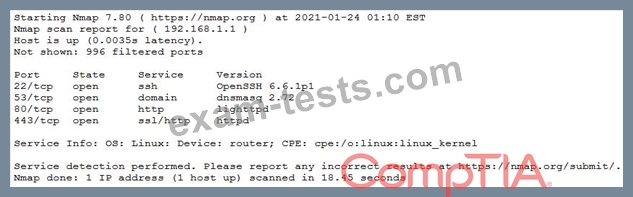
Which of the following would be the BEST conclusion about this device?

Which of the following would be the BEST conclusion about this device?
Question 43
A penetration tester has been given eight business hours to gain access to a client's financial system. Which of the following techniques will have the highest likelihood of success?
Question 44
A mail service company has hired a penetration tester to conduct an enumeration of all user accounts on an SMTP server to identify whether previous staff member accounts are still active. Which of the following commands should be used to accomplish the goal?
Question 45
A penetration tester runs the following command on a system:
find / -user root -perm -4000 -print 2>/dev/null
Which of the following is the tester trying to accomplish?
find / -user root -perm -4000 -print 2>/dev/null
Which of the following is the tester trying to accomplish?

