Question 31
A client has requested that the penetration test scan include the following UDP services: SNMP, NetBIOS, and DNS. Which of the following Nmap commands will perform the scan?
Question 32
Penetration-testing activities have concluded, and the initial findings have been reviewed with the client. Which of the following best describes the NEXT step in the engagement?
Question 33
Which of the following protocols or technologies would provide in-transit confidentiality protection for emailing the final security assessment report?
Question 34
A penetration tester ran the following commands on a Windows server:
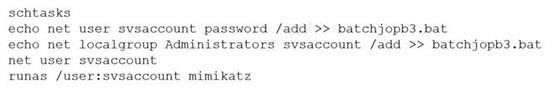
Which of the following should the tester do AFTER delivering the final report?

Which of the following should the tester do AFTER delivering the final report?
Question 35
A penetration tester is reviewing the following SOW prior to engaging with a client:
"Network diagrams, logical and physical asset inventory, and employees' names are to be treated as client confidential. Upon completion of the engagement, the penetration tester will submit findings to the client's Chief Information Security Officer (CISO) via encrypted protocols and subsequently dispose of all findings by erasing them in a secure manner." Based on the information in the SOW, which of the following behaviors would be considered unethical? (Choose two.)
"Network diagrams, logical and physical asset inventory, and employees' names are to be treated as client confidential. Upon completion of the engagement, the penetration tester will submit findings to the client's Chief Information Security Officer (CISO) via encrypted protocols and subsequently dispose of all findings by erasing them in a secure manner." Based on the information in the SOW, which of the following behaviors would be considered unethical? (Choose two.)

