Question 16
Which of the following tools provides Python classes for interacting with network protocols?
Question 17
A penetration tester gains access to a system and establishes persistence, and then runs the following commands:
cat /dev/null > temp
touch -r .bash_history temp
mv temp .bash_history
Which of the following actions is the tester MOST likely performing?
cat /dev/null > temp
touch -r .bash_history temp
mv temp .bash_history
Which of the following actions is the tester MOST likely performing?
Question 18
A penetration tester is scanning a corporate lab network for potentially vulnerable services. Which of the following Nmap commands will return vulnerable ports that might be interesting to a potential attacker?
Question 19
A penetration tester recently completed a review of the security of a core network device within a corporate environment. The key findings are as follows:
* The following request was intercepted going to the network device:
GET /login HTTP/1.1
Host: 10.50.100.16
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Accept-Language: en-US,en;q=0.5 Connection: keep-alive Authorization: Basic WU9VUilOQU1FOnNlY3JldHBhc3N3b3jk
* Network management interfaces are available on the production network.
* An Nmap scan returned the following:
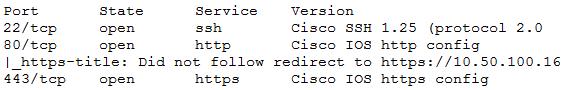
Which of the following would be BEST to add to the recommendations section of the final report? (Choose two.)
* The following request was intercepted going to the network device:
GET /login HTTP/1.1
Host: 10.50.100.16
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Accept-Language: en-US,en;q=0.5 Connection: keep-alive Authorization: Basic WU9VUilOQU1FOnNlY3JldHBhc3N3b3jk
* Network management interfaces are available on the production network.
* An Nmap scan returned the following:

Which of the following would be BEST to add to the recommendations section of the final report? (Choose two.)
Question 20
A penetration tester runs a scan against a server and obtains the following output:
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-12-20 09:23AM 331 index.aspx
| ftp-syst:
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2012 Std
3389/tcp open ssl/ms-wbt-server
| rdp-ntlm-info:
| Target Name: WEB3
| NetBIOS_Computer_Name: WEB3
| Product_Version: 6.3.9600
|_ System_Time: 2021-01-15T11:32:06+00:00
8443/tcp open http Microsoft IIS httpd 8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
Which of the following command sequences should the penetration tester try NEXT?
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-12-20 09:23AM 331 index.aspx
| ftp-syst:
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2012 Std
3389/tcp open ssl/ms-wbt-server
| rdp-ntlm-info:
| Target Name: WEB3
| NetBIOS_Computer_Name: WEB3
| Product_Version: 6.3.9600
|_ System_Time: 2021-01-15T11:32:06+00:00
8443/tcp open http Microsoft IIS httpd 8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
Which of the following command sequences should the penetration tester try NEXT?

