Question 1
SIMULATION
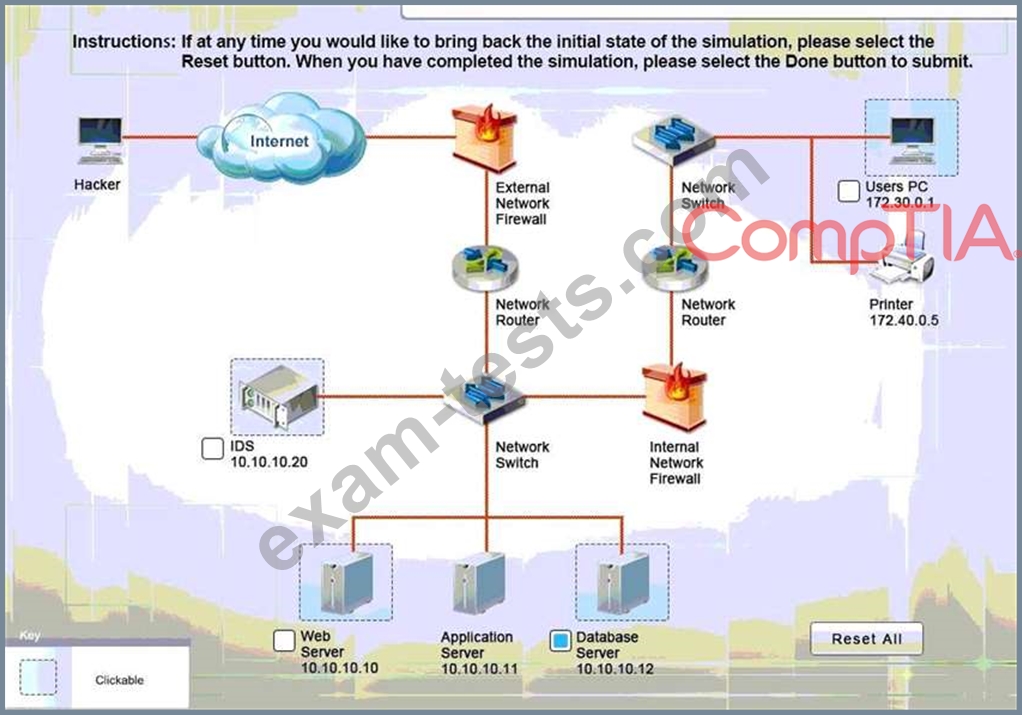
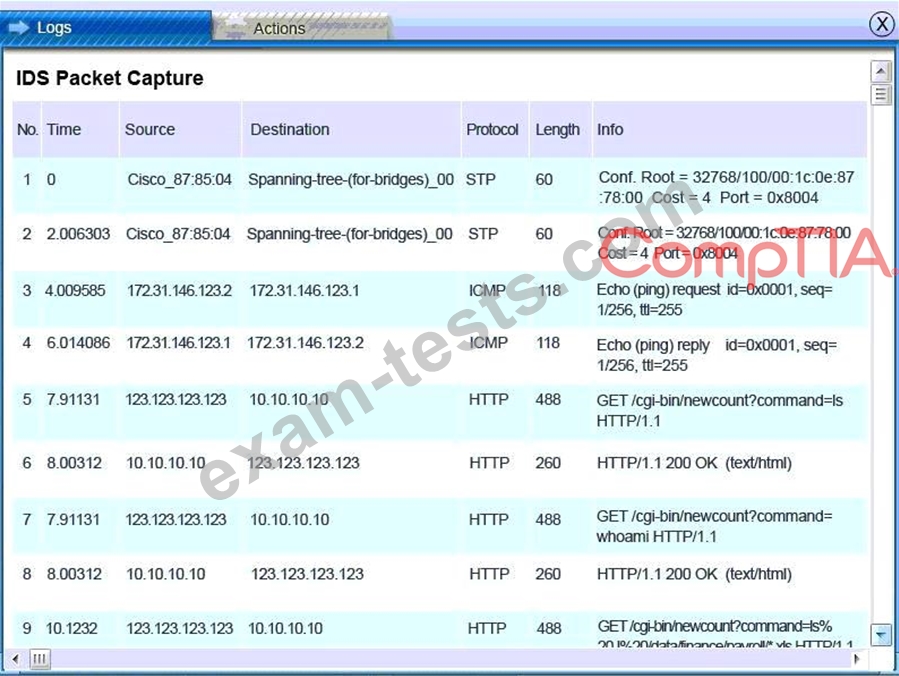
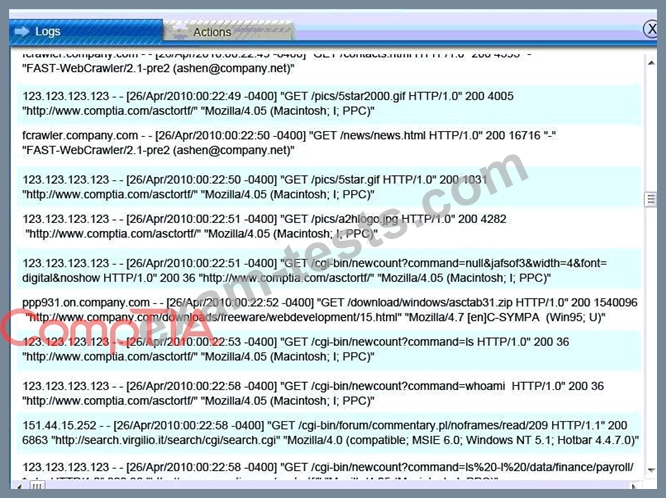
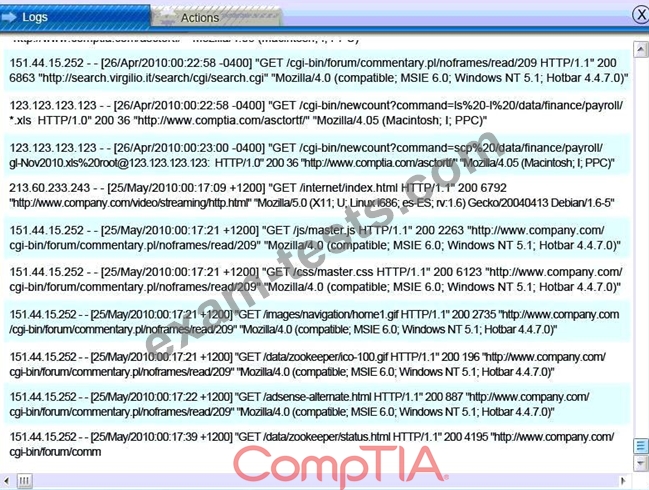
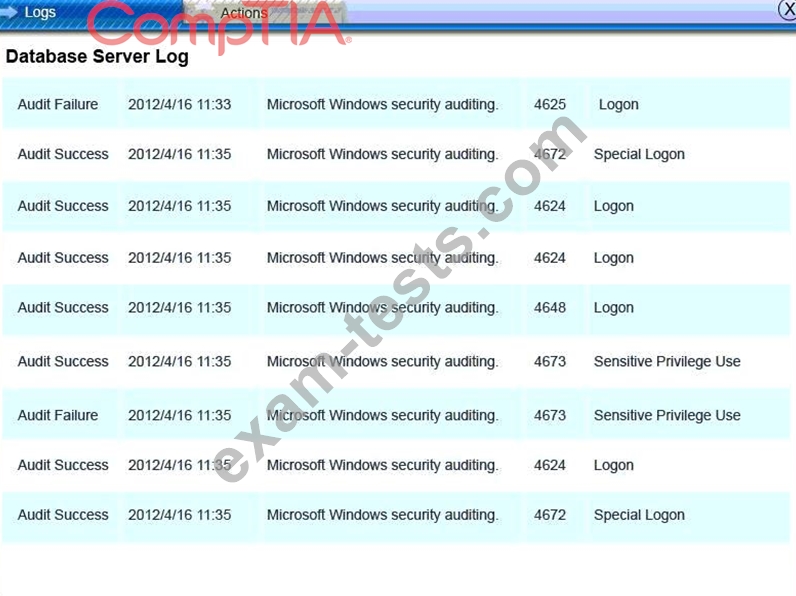
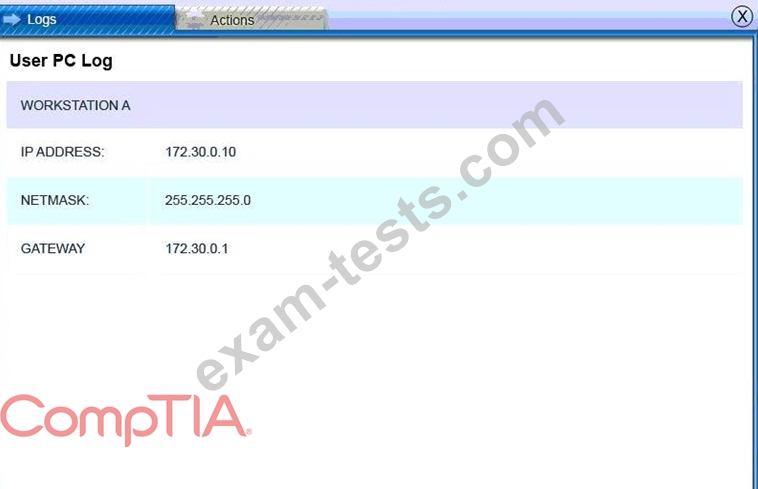
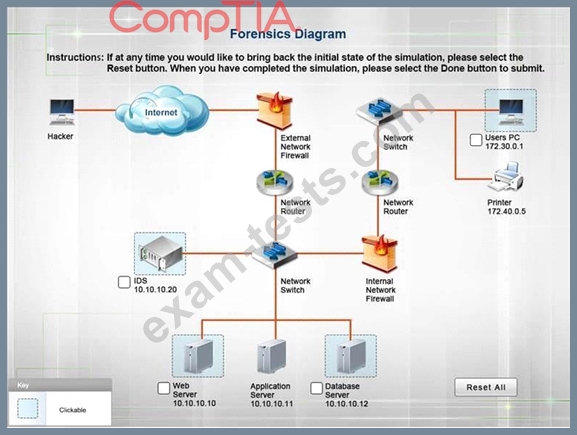
A security administrator discovers that an attack has been completed against a node on the corporate network. All available logs were collected and stored.
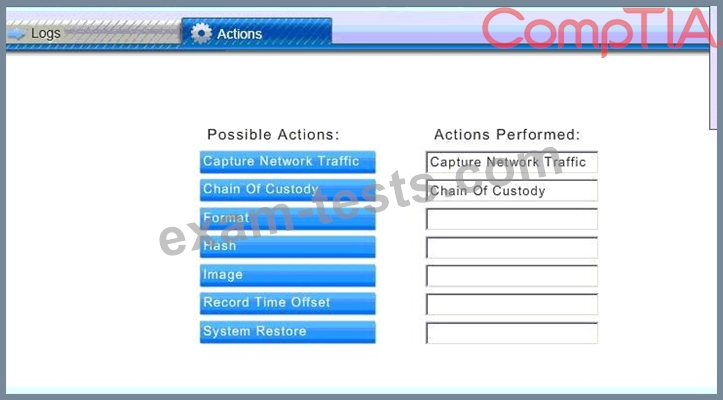
You must review all network logs to discover the scope of the attack, check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. The environment is a critical production environment; perform the LEAST disruptive actions on the network, while still performing the appropriate incid3nt responses.
Instructions: The web server, database server, IDS, and User PC are clickable.
Check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network.
Not all actions may be used, and order is not important.
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit.
Once the simulation is submitted, please select the Next button to continue.
A security administrator discovers that an attack has been completed against a node on the corporate network. All available logs were collected and stored.
You must review all network logs to discover the scope of the attack, check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. The environment is a critical production environment; perform the LEAST disruptive actions on the network, while still performing the appropriate incid3nt responses.
Instructions: The web server, database server, IDS, and User PC are clickable.
Check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network.
Not all actions may be used, and order is not important.
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit.
Once the simulation is submitted, please select the Next button to continue.

Question 2
A security administrator wishes to implement a secure a method of file transfer when communicating with outside organizations.
Which of the following protocols would BEST facilitate secure file transfers? (Select TWO)
Which of the following protocols would BEST facilitate secure file transfers? (Select TWO)
Question 3
The Chief Executive Officer (CEO) of a major defense contracting company a traveling overseas for a conference. The CEO will be taking a laptop.
Which of the following should the security administrator implement to ensure confidentiality of the data if the laptop were to be stolen or lost during the trip?
Which of the following should the security administrator implement to ensure confidentiality of the data if the laptop were to be stolen or lost during the trip?
Question 4
A government agency with sensitive information wants to virtualize its infrastructure. Which of the following cloud deployment models BEST fits the agency's needs?
Question 5
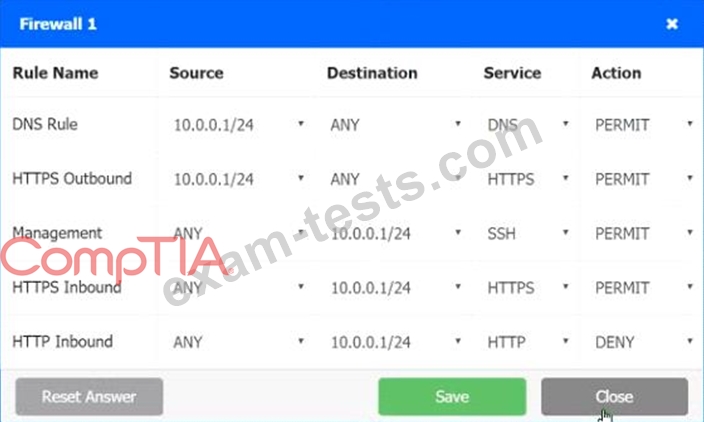
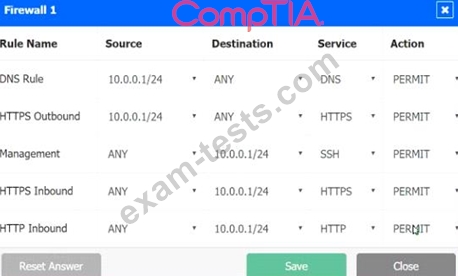
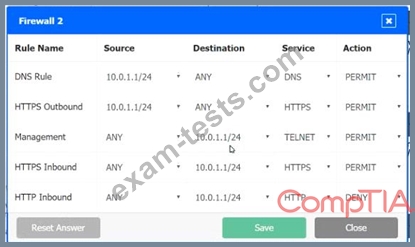
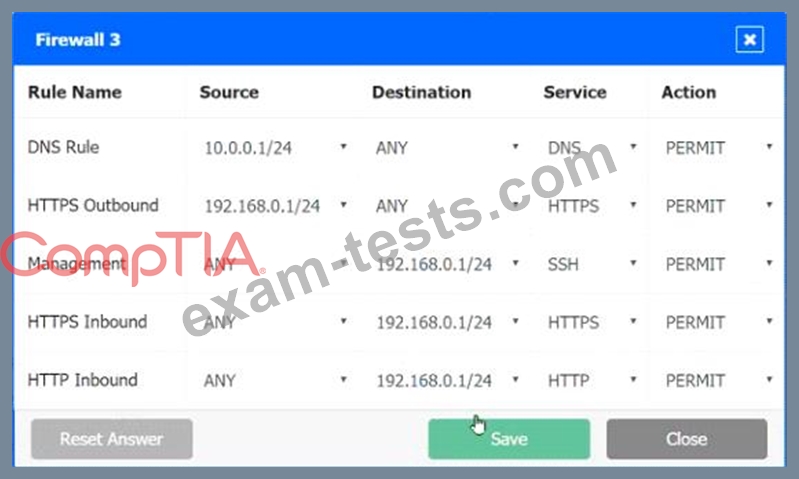
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
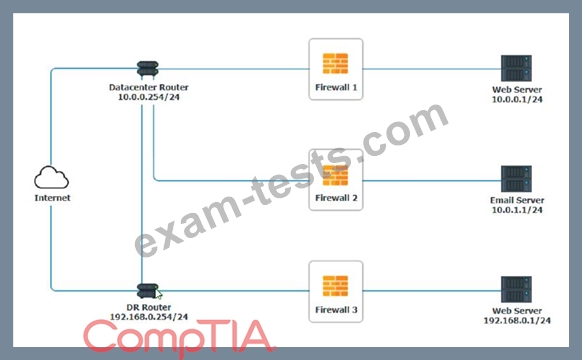
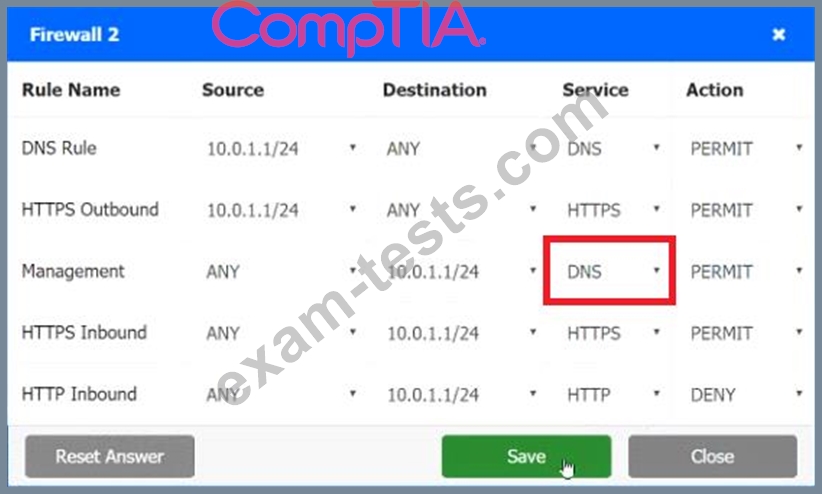
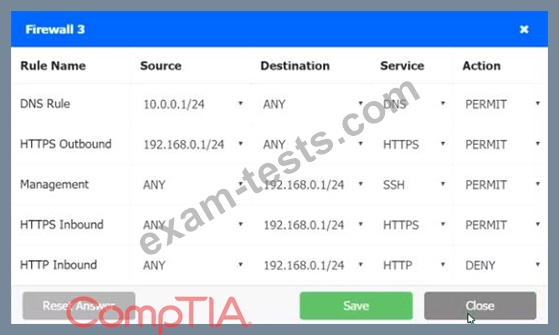
INSTRUCTIONS
Click on each firewall to do the following:
1. Deny cleartext web traffic
2. Ensure secure management protocols are used.
3. Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
Hat any time you would like to bring back the initial state of the simulation, please dick the Reset All button.

INSTRUCTIONS
Click on each firewall to do the following:
1. Deny cleartext web traffic
2. Ensure secure management protocols are used.
3. Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
Hat any time you would like to bring back the initial state of the simulation, please dick the Reset All button.