Question 6
A security administrator has written a script that will automatically upload binary and text-based configuration files onto a remote server using a scheduled task. The configuration files contain sensitive information.
Which of the following should the administrator use? (Select TWO)
Which of the following should the administrator use? (Select TWO)
Question 7
CORRECT TEXT
A security administrator wants to implement strong security on the company smart phones and terminal servers located in the data center. Drag and drop the applicable controls to each asset types? Instructions: Controls can be used multiple times and not all placeholders need to be filled.
When you have completed the simulation, please select the Done button to submit.
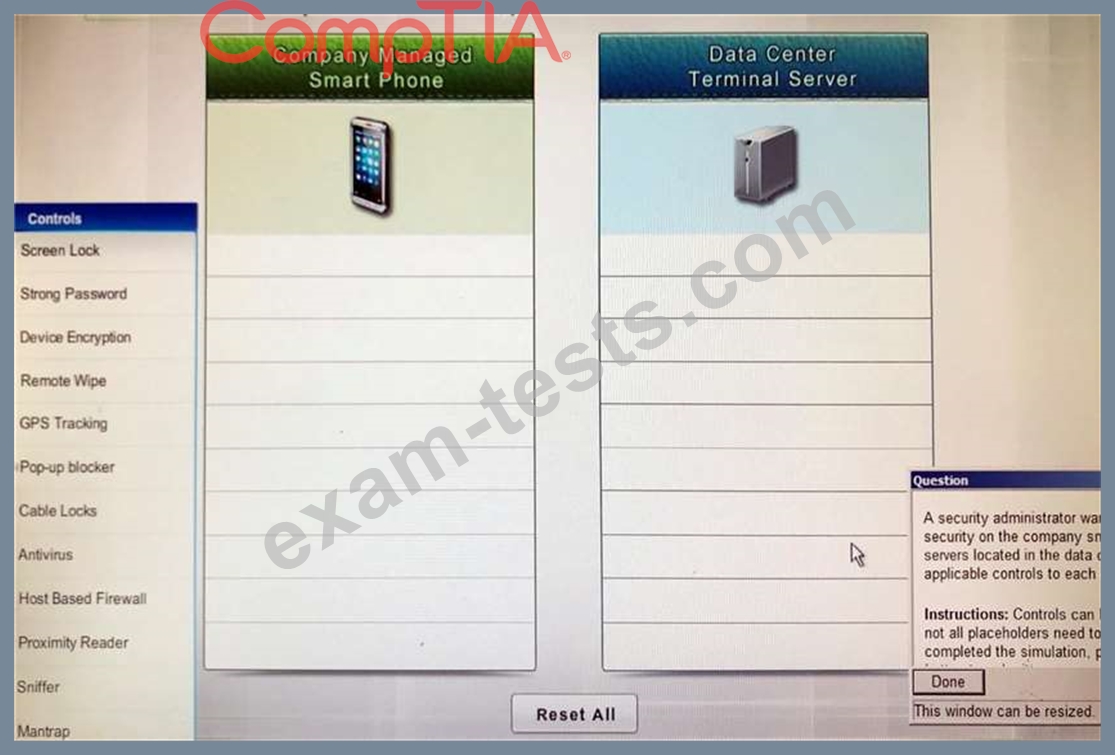
A security administrator wants to implement strong security on the company smart phones and terminal servers located in the data center. Drag and drop the applicable controls to each asset types? Instructions: Controls can be used multiple times and not all placeholders need to be filled.
When you have completed the simulation, please select the Done button to submit.

Question 8
A company wants to host a publicity available server that performs the following functions:
Evaluates MX record lookup

Can perform authenticated requests for A and AAA records

Uses RRSIG

Which of the following should the company use to fulfill the above requirements?
Evaluates MX record lookup

Can perform authenticated requests for A and AAA records

Uses RRSIG

Which of the following should the company use to fulfill the above requirements?
Question 9
An organization has decided to host its web application and database in the cloud. Which of the following BEST describes the security concerns for this decision?
Question 10
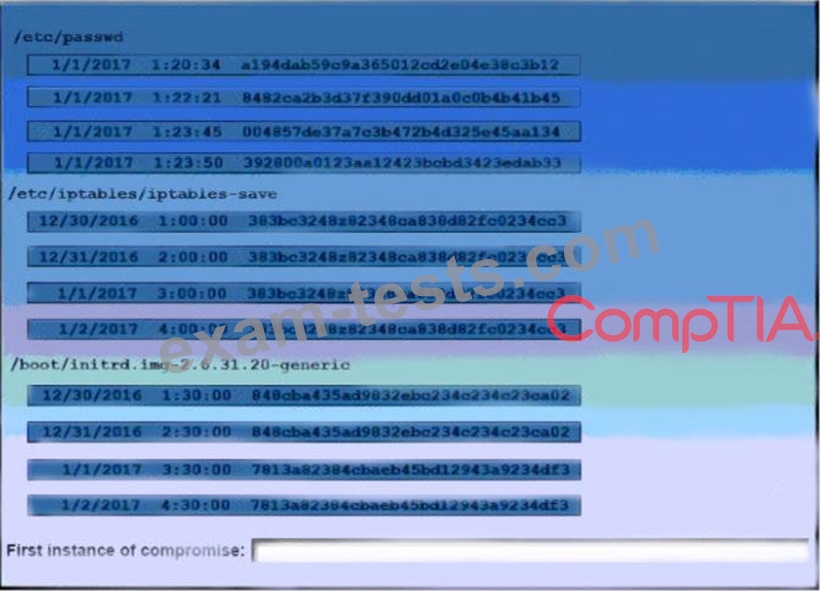
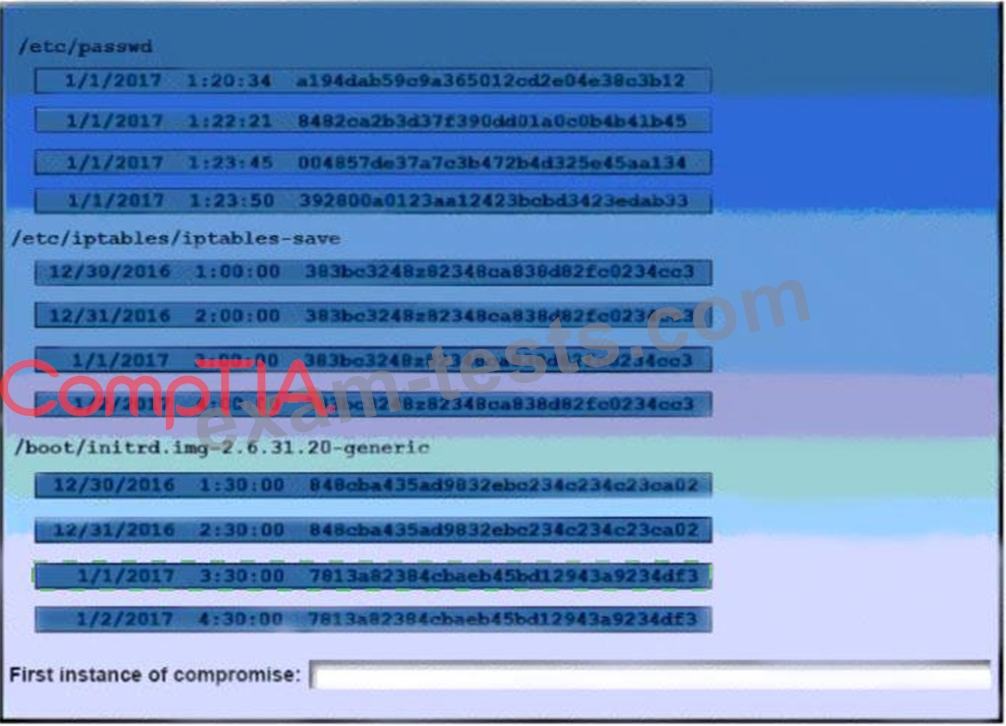
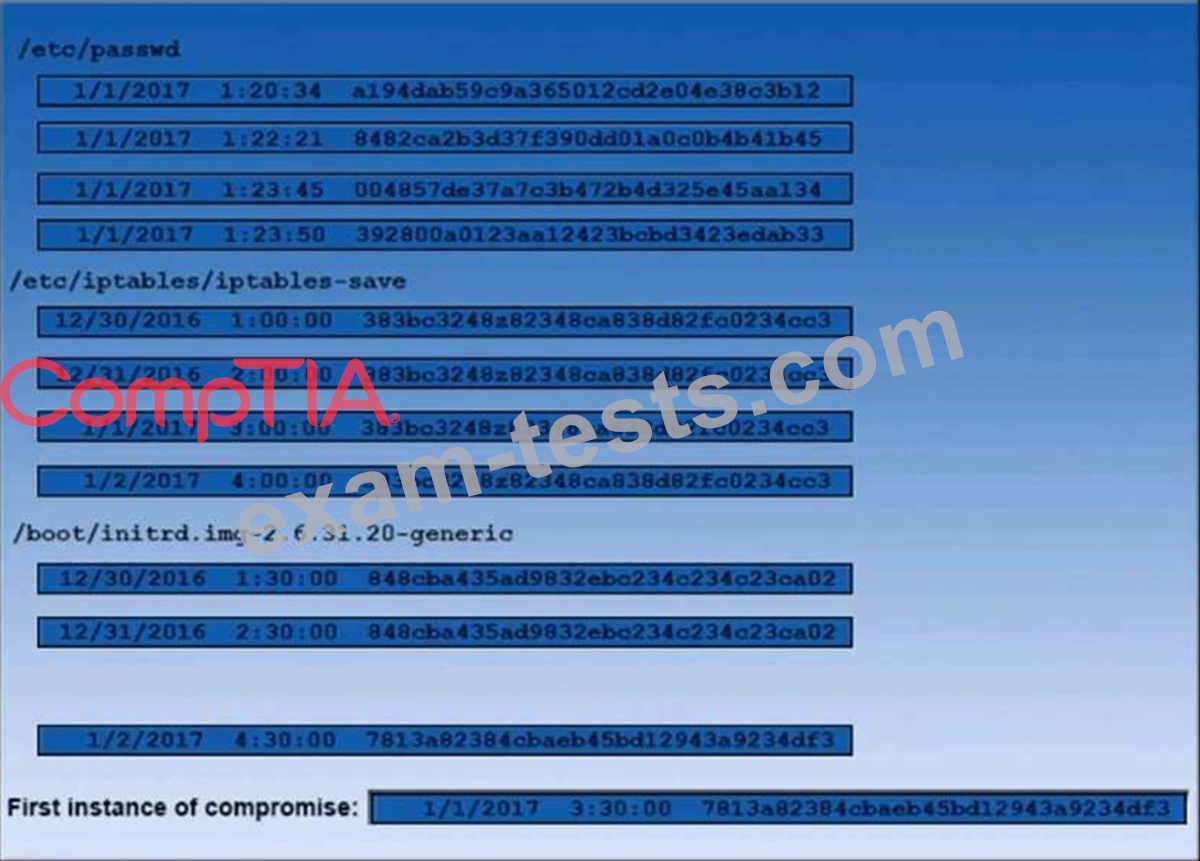
A security auditor is reviewing the following output from file integrity monitoring software installed on a very busy server at a large service provider. The server has not been updates since it was installed. Drag and drop the log entry that identifies the first instance of server compromise.