Question 1
Security analysts are conducting an investigation of an attack that occurred inside the organization's network. An attacker was able to connect network traffic between workstation throughout the network. The analysts review the following logs:
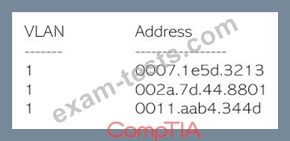
The layer 2 address table has hundred of entries similar to the ones above. Which of the following attacks has MOST likely occurred?

The layer 2 address table has hundred of entries similar to the ones above. Which of the following attacks has MOST likely occurred?
Question 2
A company was compromised, and a security analyst discovered the attacker was able to get access to a service account. The following logs were discovered during the investigation:
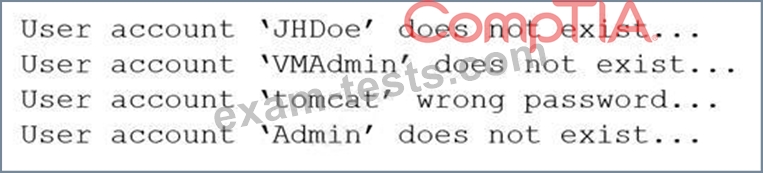
Which of the following MOST likely would have prevented the attacker from learning the service account name?

Which of the following MOST likely would have prevented the attacker from learning the service account name?
Question 3
A company has been experiencing very brief power outages from its utility company over the last few months.
These outages only last for one second each time. The utility company is aware of the issue and is working to replace a faulty transformer. Which of the following BEST describes what the company should purchase to ensure its critical servers and network devices stay online?
These outages only last for one second each time. The utility company is aware of the issue and is working to replace a faulty transformer. Which of the following BEST describes what the company should purchase to ensure its critical servers and network devices stay online?
Question 4
The chief compliance officer from a bank has approved a background check policy for all new hires. Which of the following is the policy MOST likely protecting against?
Question 5
An attacker has successfully exfiltrated several non-salted password hashes from an online system. Given the logs below:

Which of the following BEST describes the type of password attack the attacker is performing?

Which of the following BEST describes the type of password attack the attacker is performing?

