Question 21
A recently discovered zero-day exploit utilizes an unknown vulnerability in the SMB network protocol to rapidly infect computers.
Once infected, computers are encrypted and held for ransom. Which of the following would BEST prevent this attack from reoccurring?
Once infected, computers are encrypted and held for ransom. Which of the following would BEST prevent this attack from reoccurring?
Question 22
A forensics investigator is examining a number of unauthorized payments that were reported on the
00mpany's website. Some unusual log entries show users received an email for an unwanted mailing list and clicked on a link to attempt to unsubscribe. One of the users reported the email to the phishing team, and the forwarded email revealed the link to be:
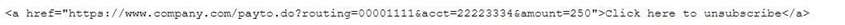
Which of the following will the forensics investigator MOST likely determine has occurred?
00mpany's website. Some unusual log entries show users received an email for an unwanted mailing list and clicked on a link to attempt to unsubscribe. One of the users reported the email to the phishing team, and the forwarded email revealed the link to be:
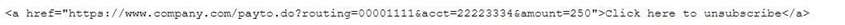
Which of the following will the forensics investigator MOST likely determine has occurred?
Question 23
Joe, a user at a company, clicked an email link led to a website that infected his workstation. Joe, was connected to the network, and the virus spread to the network shares. The protective measures failed to stop this virus, and It has continues to evade detection. Which of the following should administrator implement to protect the environment from this malware?
Question 24
An analyst Is generating a security report for the management team. Security guidelines recommend disabling all listening unencrypted services. Given this output from Nmap:

Which of the following should the analyst recommend to disable?

Which of the following should the analyst recommend to disable?
Question 25
A security analyst has been asked to investigate a situation after the SOC started to receive alerts from the SIEM. The analyst first looks at the domain controller and finds the following events:
To better understand what is going on, the analyst runs a command and receives the following output:
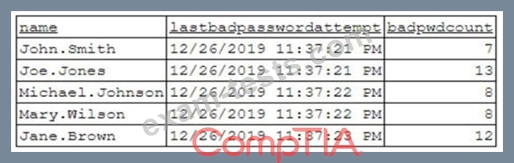
Based on the analyst's findings, which of the following attacks is being executed?
To better understand what is going on, the analyst runs a command and receives the following output:

Based on the analyst's findings, which of the following attacks is being executed?
Premium Bundle
Newest SY0-601 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing SY0-601 Exam! BraindumpsPass.com now offer the updated SY0-601 exam dumps, the BraindumpsPass.com SY0-601 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com SY0-601 pdf dumps with Exam Engine here:

