Question 16
A security analyst b concerned about traffic initiated to the dark web from the corporate LAN. Which of the following networks should he analyst monitor?
Question 17
A dynamic application vulnerability scan identified code injection could be performed using a web form. Which of the following will be BEST remediation to prevent this vulnerability?
Question 18
A company's help desk received several AV alerts indicating Mimikatz attempted to run on the remote systems. Several users also reported that the new company flash drives they picked up in the
break room only have 512KB of storage. Which of the following is MOST likely the cause?
break room only have 512KB of storage. Which of the following is MOST likely the cause?
Question 19
While investigating a data leakage incident, a security analyst reviews access control to cloud-hosted dat a. The following information was presented in a security posture report.
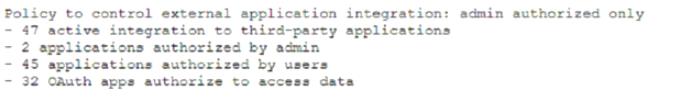
Based on the report, which of the following was the MOST likely attack vector used against the company?

Based on the report, which of the following was the MOST likely attack vector used against the company?
Question 20
A security analyst is investigating an incident to determine what an attacker was able to do on a compromised laptop. The analyst reviews the following SIEM log:
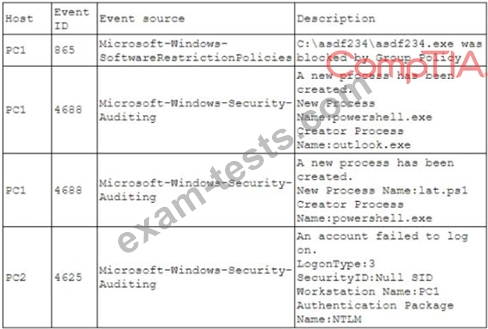
Which of the following describes the method that was used to compromise the laptop?

Which of the following describes the method that was used to compromise the laptop?

