Question 161
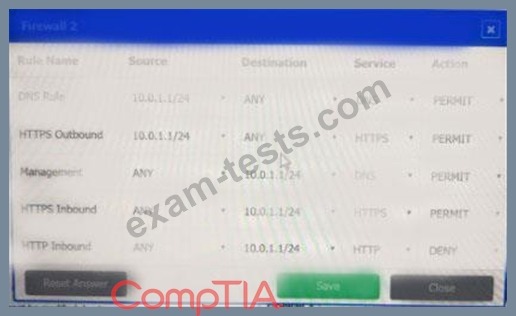
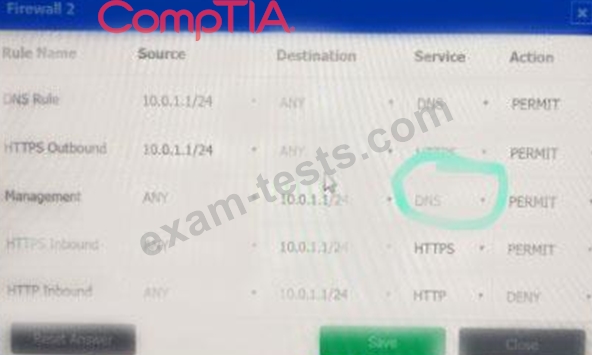
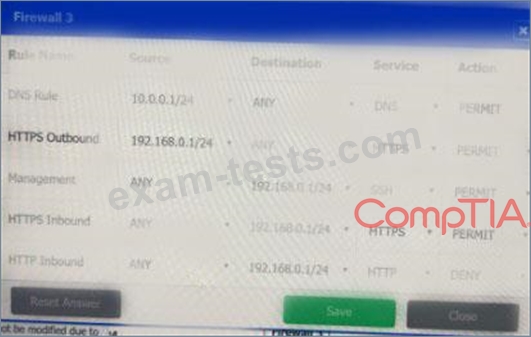
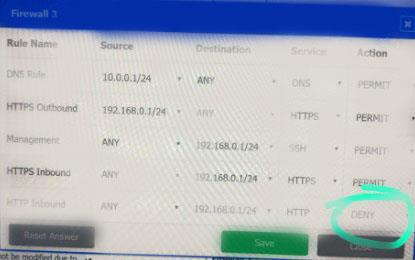
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
* Deny cleartext web traffic.
* Ensure secure management protocols are used.
* Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
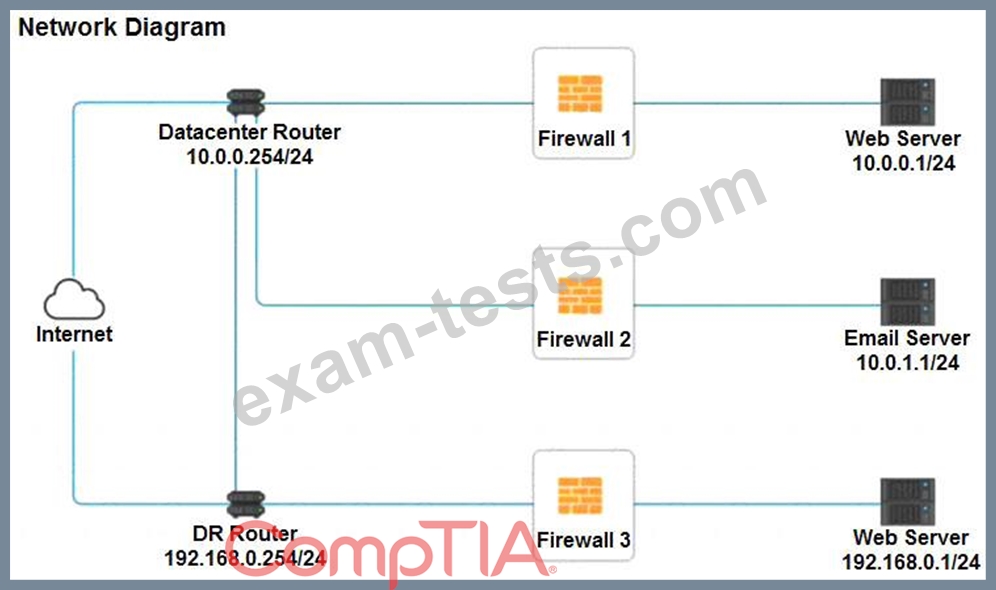
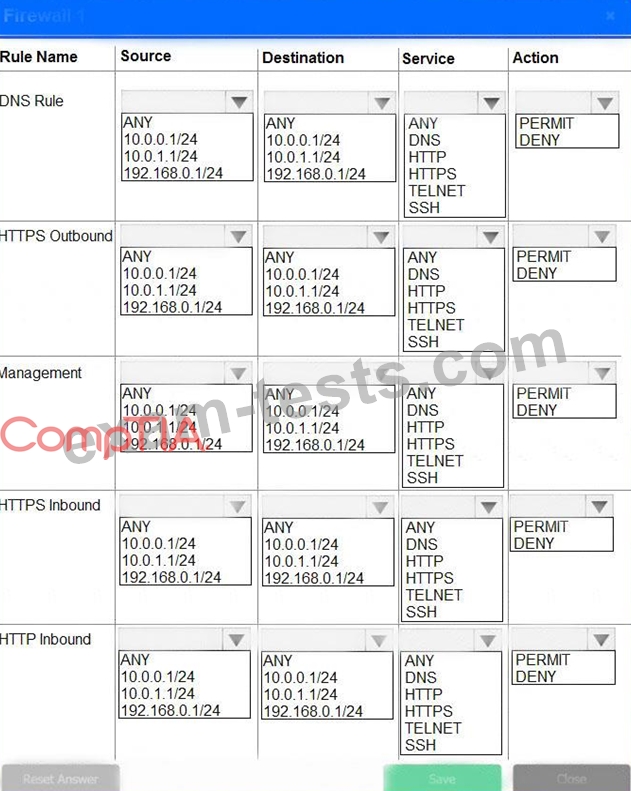
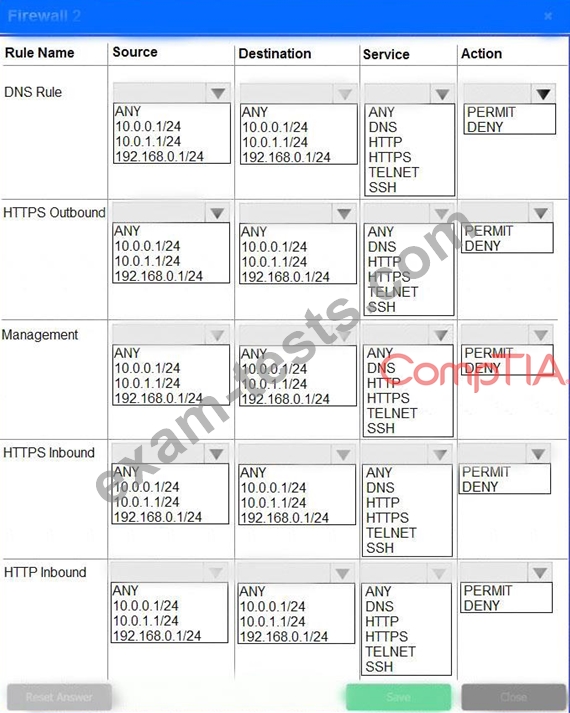

INSTRUCTIONS
Click on each firewall to do the following:
* Deny cleartext web traffic.
* Ensure secure management protocols are used.
* Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.




Question 162
Which of the following controls would BEST identify and report malicious insider activities?
Question 163
A symmetric encryption algorithm is BEST suited for:
Question 164
A network engineer created two subnets that will be used for production and development servers. Per security policy, production and development servers must each have a dedicated network that cannot communicate with one another directly. Which of the following should be deployed so that server administrators can access these devices?
Question 165
A user reports constant lag and performance issues with the wireless network when working at a local coffee shop. A security analyst walks the user through an installation of Wireshark and get a five-minute pcap to analyze. The analyst observes the following output:
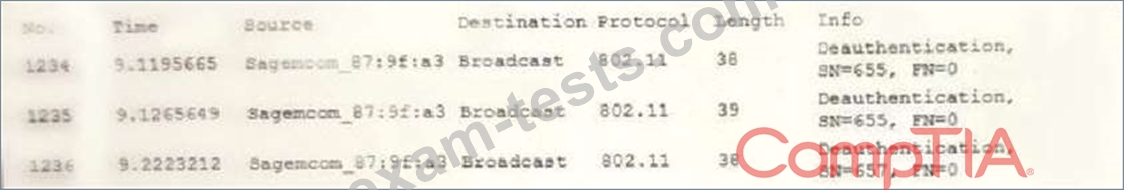
Which of the following attacks does the analyst MOST likely see in this packet capture?

Which of the following attacks does the analyst MOST likely see in this packet capture?
Premium Bundle
Newest SY0-601 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing SY0-601 Exam! BraindumpsPass.com now offer the updated SY0-601 exam dumps, the BraindumpsPass.com SY0-601 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com SY0-601 pdf dumps with Exam Engine here: