Question 176
Which of the following describes the ability of code to target a hypervisor from inside
Question 177
A security researching is tracking an adversary by noting its attack and techniques based on its capabilities, infrastructure, and victims. Which of the following is the researcher MOST likely using?
Question 178
An organization regularly scans its infrastructure for missing security patches but is concerned about hackers gaining access to the scanner's account. Which of the following would be BEST to minimize this risk?
Question 179
A security analyst has been asked to investigate a situation after the SOC started to receive alerts from the SIEM. The analyst first looks at the domain controller and finds the following events:
To better understand what is going on, the analyst runs a command and receives the following output:
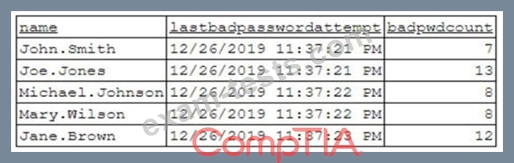
Based on the analyst's findings, which of the following attacks is being executed?
To better understand what is going on, the analyst runs a command and receives the following output:

Based on the analyst's findings, which of the following attacks is being executed?
Question 180
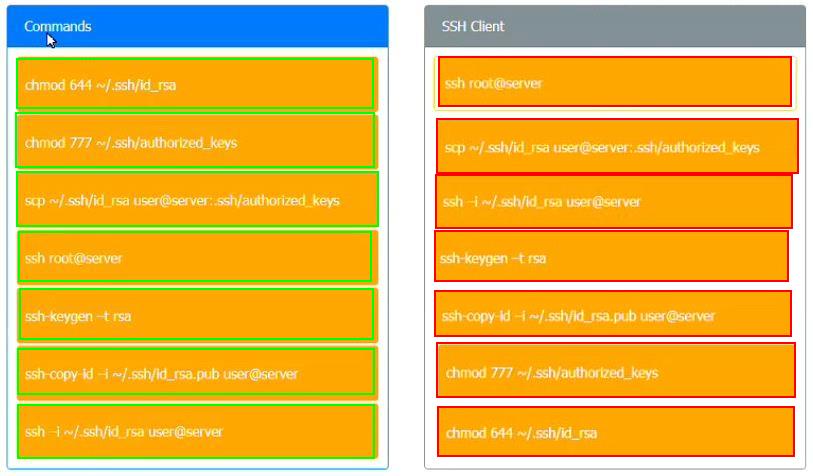
A security engineer is setting up passwordless authentication for the first time.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

Premium Bundle
Newest SY0-601 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing SY0-601 Exam! BraindumpsPass.com now offer the updated SY0-601 exam dumps, the BraindumpsPass.com SY0-601 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com SY0-601 pdf dumps with Exam Engine here: