Question 1
Which of the following is the BEST example of a cost-effective physical control to enforce a USB removable media restriction policy?
Question 2
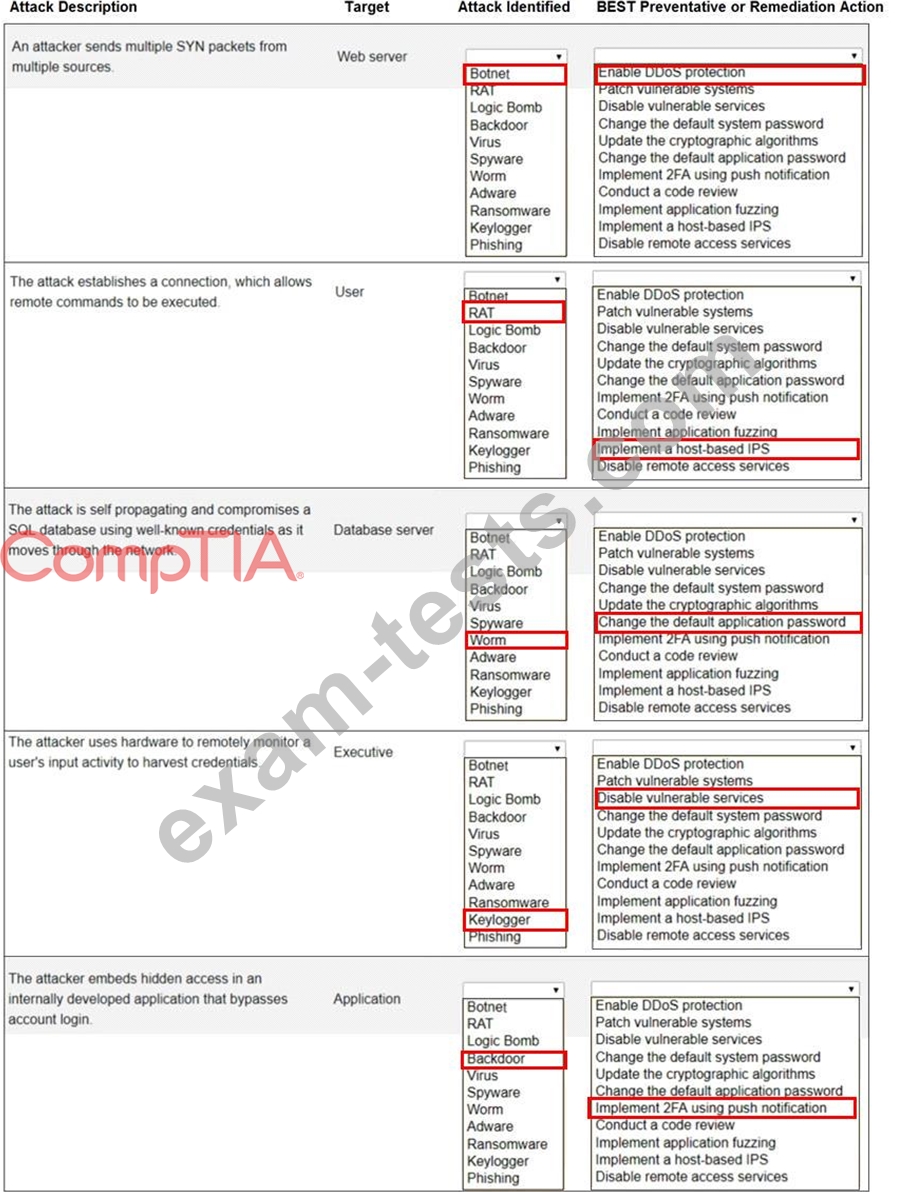
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
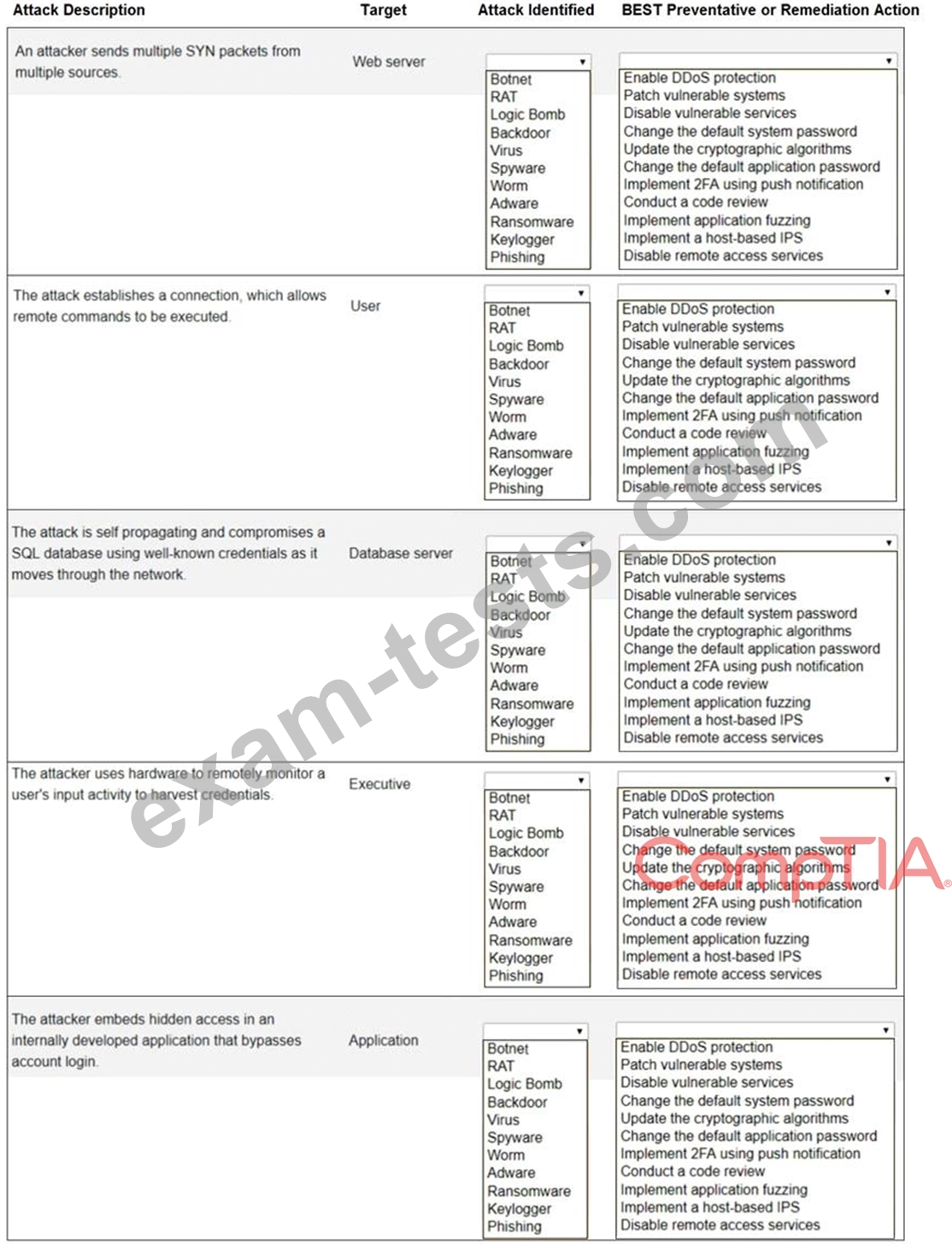
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

Question 3
A security analyst is investigating suspicious traffic on the web server located at IP address 10.10.1.1. A search of the WAF logs reveals the following output:
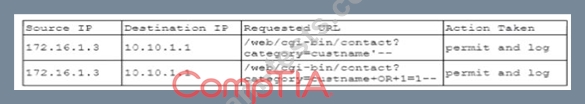
Which of the following is MOST likely occurring?

Which of the following is MOST likely occurring?
Question 4
A security analyst wants to fingerpnnt a web server Which of the following tools will the security analyst MOST likely use to accomplish this task?
Question 5
Which of the following is a known security nsk associated with data archives that contain financial information?