Question 51
A security incident has been resolved Which of the following BEST describes the importance of the final phase of the incident response plan?
Question 52
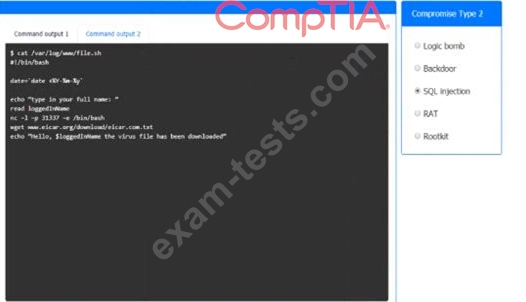
An incident has occurred in the production environment.
Analyze the command outputs and identify the type of compromise.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
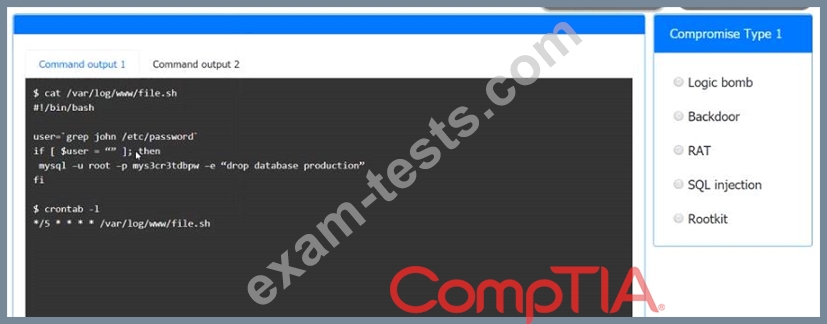
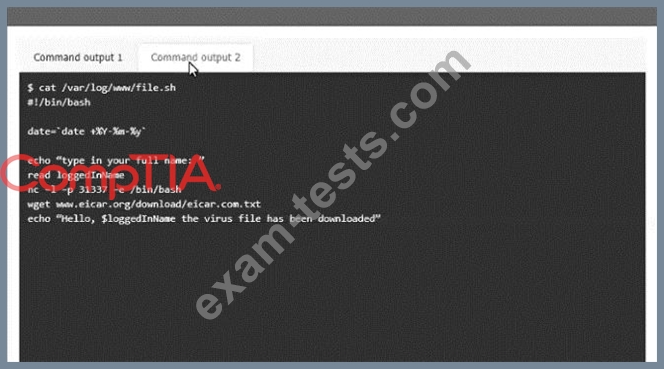
Analyze the command outputs and identify the type of compromise.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


Question 53
A security policy states that common words should not be used as passwords. A security auditor was able to perform a dictionary attack against corporate credentials Which of the following controls was being violated?
Question 54
The Chief information Security Officer wants to prevent exfilitration of sensitive information from employee cell phones when using public USB power charging stations. Which of the following would be the Best solution to implement?
Question 55
The Chief Information Secunty Officer (CISO) requested a report on potential areas of improvement following a security incident. Which of the following incident response processes is the CISO requesting?