Question 31
A forensic analyst needs to prove that data has not been tampered with since it was collected Which of the following methods will the analyst MOST likely use?
Question 32
A security analyst was asked to evaluate a potential attack that occurred on a publicly accessible section of the company's website The malicious actor posted an entry in an attempt to trick users into cltckmg the following:
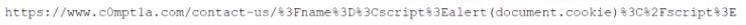
Which of the following was MOST likely observed?
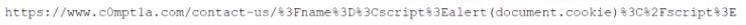
Which of the following was MOST likely observed?
Question 33
Which of the following BEST reduces the security risks introduced when running systems that have expired vendor support and lack an immediate replacement?
Question 34
A company suspects that some corporate accounts were compromised. The number of suspicious logins from locations not recognized by the users is increasing Employees who travel need their accounts protected without the nsk of blocking legitimate login requests that may be made over new sign-in properties. Which of the following security controls can be implemented?
Question 35
Which of the following would BEST provide a systems administrator with the ability to more efficiently identify systems and manage permissions and policies based on location, role, and service level?

