Question 36
A Chief Information Security Officer wants to ensure the organization is validating and checking the Integrity of zone transfers. Which of the following solutions should be implemented?
Question 37
A security engineer was assigned to implement a solution to prevent attackers from gaining access by pretending to be authorized users. Which of the following technologies meets the requirement?
Question 38
A systems administrator reports degraded performance on a virtual server. The administrator increases the virtual memory allocation which improves conditions, but performance degrades again after a few days. The administrator runs an anarysis tool and sees the following output:
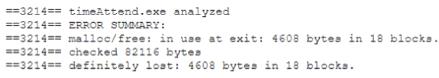
The administrator terminates the timeAttend.exe observes system performance over the next few days, and notices that the system performance does not degrade Which of the following issues is MOST likely occurring?

The administrator terminates the timeAttend.exe observes system performance over the next few days, and notices that the system performance does not degrade Which of the following issues is MOST likely occurring?
Question 39
After gaining access to a dual-homed (i.e.. wired and wireless) multifunction device by exploiting a vulnerability in the device's firmware, a penetration tester then gains shell access on another networked asset This technique is an example of:
Question 40
An ofgantzation has decided to purchase an insurance policy because a risk assessment determined that the cost to remediate the risk is greater than the five-year cost of the insurance policy. The organization is enabling risk

