Question 56
The network information for a workstation is as follows:

When the workstation's user attempts to access www.example.com. the URL that actually opens is www.notexample.com. The user successfully connects to several other legitimate URLs. Which of the following have MOST likely occurred? (Select TWO).

When the workstation's user attempts to access www.example.com. the URL that actually opens is www.notexample.com. The user successfully connects to several other legitimate URLs. Which of the following have MOST likely occurred? (Select TWO).
Question 57
A systems administrator is reviewing the following information from a compromised server:
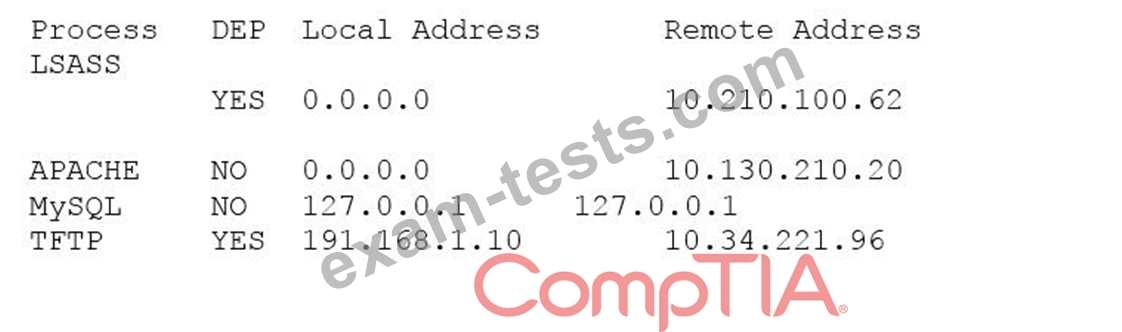
Given the above information, which of the following processes was MOST likely exploited via a remote buffer overflow attack?

Given the above information, which of the following processes was MOST likely exploited via a remote buffer overflow attack?
Question 58
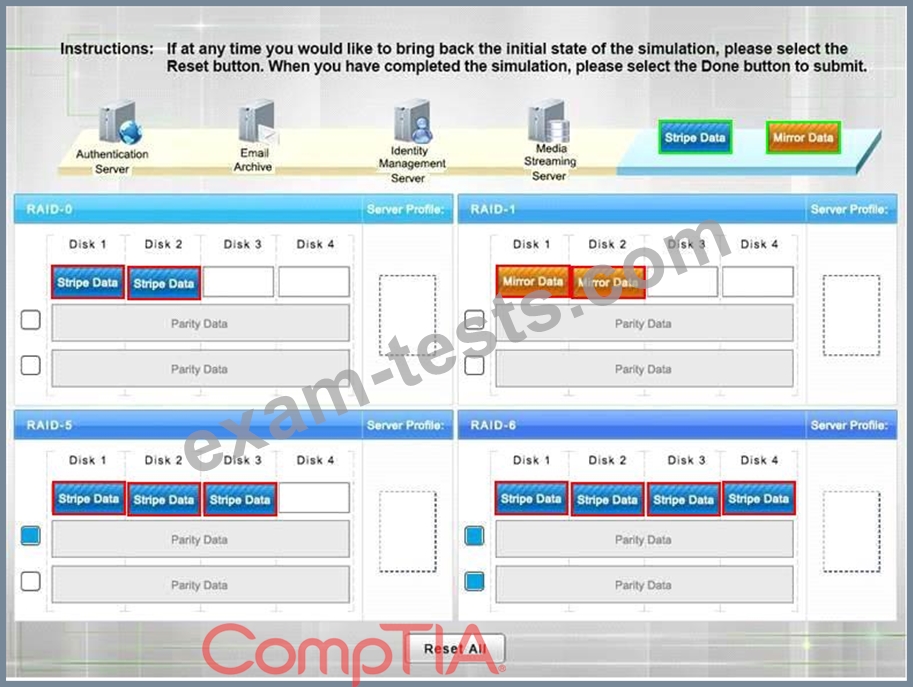
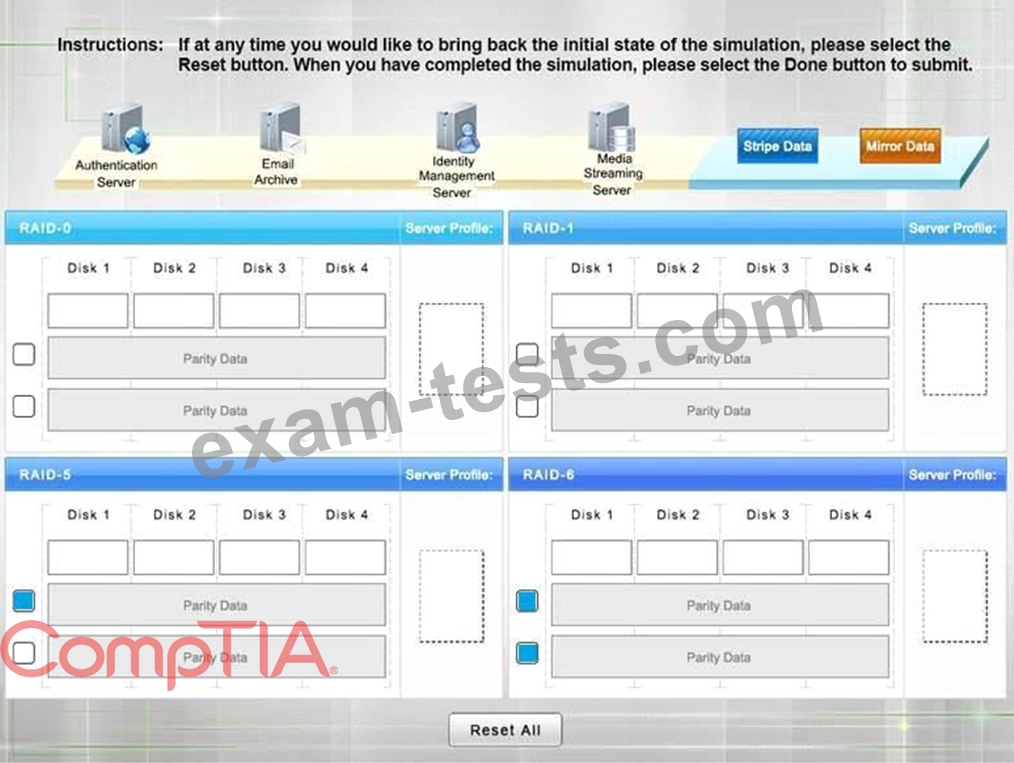
A security administrator is given the security and availability profiles for servers that are being deployed.
Match each RAID type with the correct configuration and MINIMUM number of drives.
Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:
All drive definitions can be dragged as many times as necessary
Not all placeholders may be filled in the RAID configuration boxes
If parity is required, please select the appropriate number of parity checkboxes Server profiles may be dragged only once If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Match each RAID type with the correct configuration and MINIMUM number of drives.
Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:
All drive definitions can be dragged as many times as necessary
Not all placeholders may be filled in the RAID configuration boxes
If parity is required, please select the appropriate number of parity checkboxes Server profiles may be dragged only once If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

Question 59
A Chief Information Security Officer (CISO) has tasked a security analyst with assessing the security posture of an organization and which internal factors would contribute to a security compromise. The analyst performs a walk-through of the organization and discovers there are multiple instances of unlabeled optical media on office desks. Employees in the vicinity either do not claim ownership or disavow any knowledge concerning who owns the media. Which of the following is the MOST immediate action to be taken?
Question 60
A forensic analyst is asked to respond to an ongoing network attack on a server. Place the items in the list below in the correct order in which the forensic analyst should preserve them.