Question 71
An organization's internal auditor discovers that large sums of money have recently been paid to a vendor that management does not recognize. The IT security department is asked to investigate the organizations the organization's ERP system to determine how the accounts payable module has been used to make these vendor payments.
The IT security department finds the following security configuration for the accounts payable module:
* New Vendor Entry - Required Role: Accounts Payable Clerk
* New Vendor Approval - Required Role: Accounts Payable Clerk
* Vendor Payment Entry - Required Role: Accounts Payable Clerk
* Vendor Payment Approval - Required Role: Accounts Payable Manager
Which of the following changes to the security configuration of the accounts payable module would BEST mitigate the risk?
The IT security department finds the following security configuration for the accounts payable module:
* New Vendor Entry - Required Role: Accounts Payable Clerk
* New Vendor Approval - Required Role: Accounts Payable Clerk
* Vendor Payment Entry - Required Role: Accounts Payable Clerk
* Vendor Payment Approval - Required Role: Accounts Payable Manager
Which of the following changes to the security configuration of the accounts payable module would BEST mitigate the risk?
Question 72
A company is deploying a new VoIP phone system. They require 99.999% uptime for their phone service and are concerned about their existing data network interfering with the VoIP phone system. The core switches in the existing data network are almost fully saturated.
Which of the following options will pro-vide the best performance and availability for both the VoIP traffic, as well as the traffic on the existing data network?
Which of the following options will pro-vide the best performance and availability for both the VoIP traffic, as well as the traffic on the existing data network?
Question 73
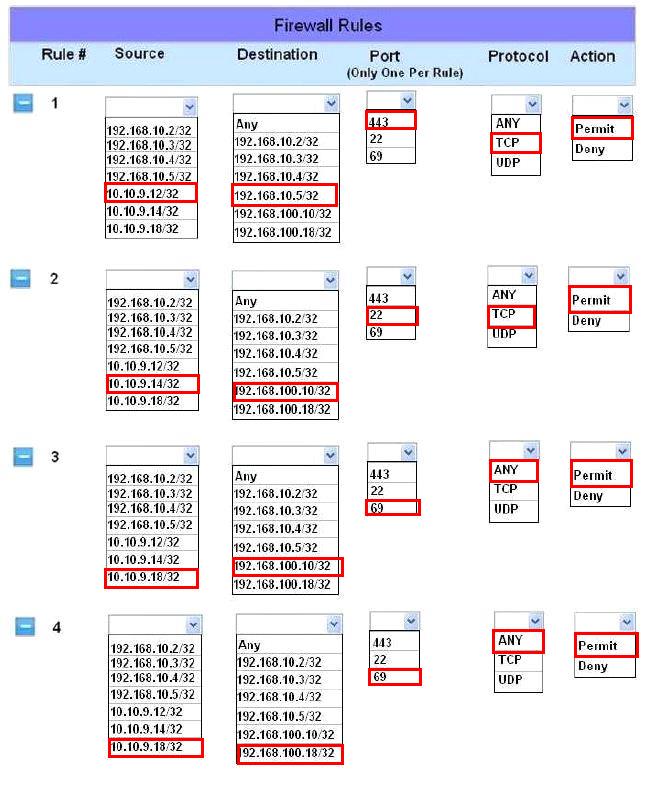
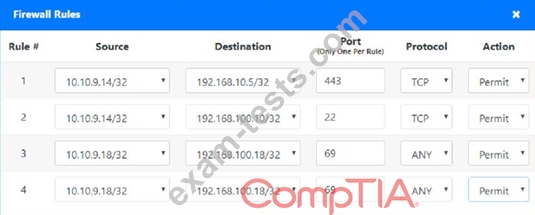
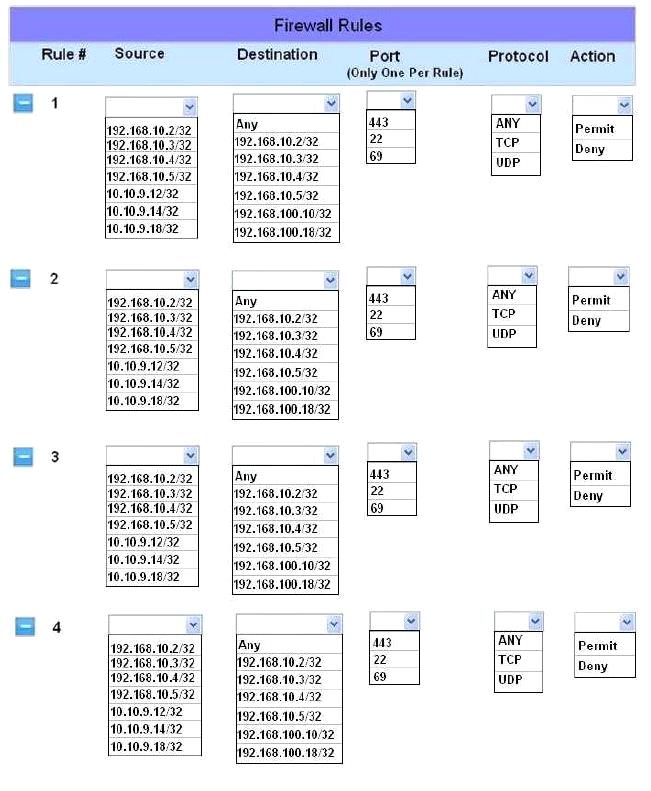
The security administrator has installed a new firewall which implements an implicit DENY policy by default.
INSTRUCTIONS:
Click on the firewall and configure it to allow ONLY the following communication.
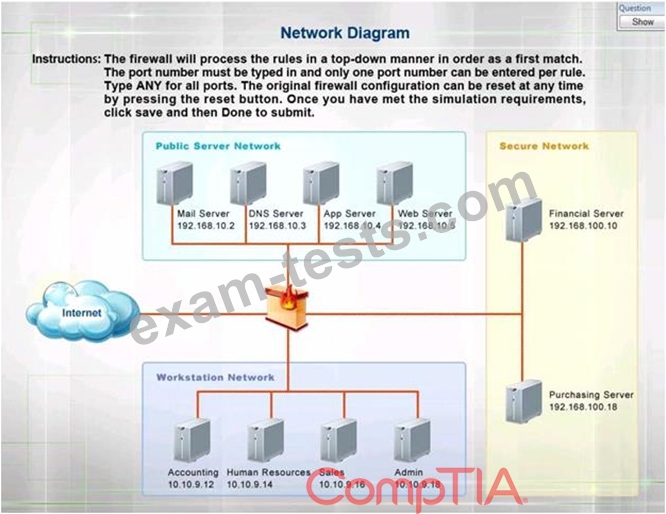
1. The Accounting workstation can ONLY access the web server on the public network over the default HTTPS port. The accounting workstation should not access other networks.
2. The HR workstation should be restricted to communicate with the Financial server ONLY, over the default SCP port
3. The Admin workstation should ONLY be able to access the servers on the secure network over the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match The port number must be typed in and only one port number can be entered per rule Type ANY for all ports. The original firewall configuration can be reset at any time by pressing the reset button. Once you have met the simulation requirements, click save and then Done to submit.
Hot Area:
INSTRUCTIONS:
Click on the firewall and configure it to allow ONLY the following communication.
1. The Accounting workstation can ONLY access the web server on the public network over the default HTTPS port. The accounting workstation should not access other networks.
2. The HR workstation should be restricted to communicate with the Financial server ONLY, over the default SCP port
3. The Admin workstation should ONLY be able to access the servers on the secure network over the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match The port number must be typed in and only one port number can be entered per rule Type ANY for all ports. The original firewall configuration can be reset at any time by pressing the reset button. Once you have met the simulation requirements, click save and then Done to submit.

Hot Area:

Question 74
An administrator is replacing a wireless router. The configuration of the old wireless router was not documented before it stopped functioning. The equipment connecting to the wireless network uses older legacy equipment that was manufactured prior to the release of the 802.11i standard. Which of the following configuration options should the administrator select for the new wireless router?
Question 75
A technician has installed new vulnerability scanner software on a server that is joined to the company domain. The vulnerability scanner is able to provide visibility over the patch posture of all company's clients. Which of the following is being used?