Question 171
A company has a data classification system with definitions for "Private" and public." The company's security policy outlines how data should be protected based on type. The company recently added the data type "Proprietary" Which of the following is the MOST likely reason the company added this data type?
Question 172
A user needs to send sensitive information to a colleague using PKI. Which of the following concepts apply when a sender encrypts the message hash with the sender's private key? (Select TWO)
Question 173
Ann, a new employee, received an email from an unknown source indicating she needed to click on the provided link to update her company's profile. Once Ann clicked the link, a command prompt appeared with the following output:
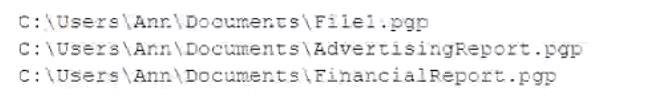
Which of the following types of malware was executed?

Which of the following types of malware was executed?
Question 174
A company just implemented a new telework policy that allows employees to use personal devices for official email and file sharing while working from home. Some of the requirements are:
* Employees must provide an alternate work location (i.e., a home address).
* Employees must install software on the device that will prevent the loss of proprietary data but will not restrict any other software from being installed.
Which of the following BEST describes the MDM options the company is using?
* Employees must provide an alternate work location (i.e., a home address).
* Employees must install software on the device that will prevent the loss of proprietary data but will not restrict any other software from being installed.
Which of the following BEST describes the MDM options the company is using?
Question 175
A security analyst reviews the following output:
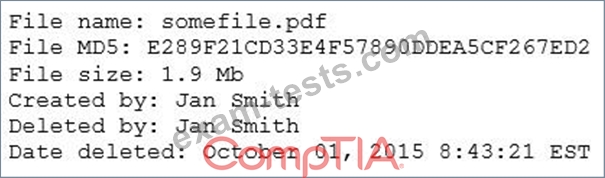
The analyst loads the hash into the SIEM to discover if this hash is seen in other parts of the network. After inspecting a large number of files, the security analyst reports the following:
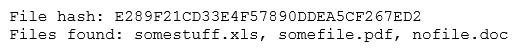
Which of the following is the MOST likely cause of the hash being found in other areas?

The analyst loads the hash into the SIEM to discover if this hash is seen in other parts of the network. After inspecting a large number of files, the security analyst reports the following:

Which of the following is the MOST likely cause of the hash being found in other areas?


