Question 176
A security analyst reviews the following output:
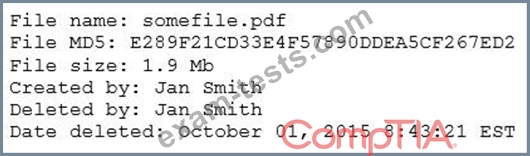
The analyst loads the hash into the SIEM to discover if this hash is seen in other parts of the network. After inspecting a large number of files, the security analyst reports the following:
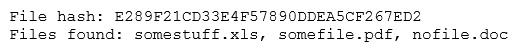
Which of the following is the MOST likely cause of the hash being found in other areas?

The analyst loads the hash into the SIEM to discover if this hash is seen in other parts of the network. After inspecting a large number of files, the security analyst reports the following:

Which of the following is the MOST likely cause of the hash being found in other areas?
Question 177
Attackers have been using revoked certificates for MITM attacks to steal credentials from employees of Company.com.
Which of the following options should Company.com implement to mitigate these attacks?
Which of the following options should Company.com implement to mitigate these attacks?
Question 178
Joe, a contractor, is hired by a firm to perform a penetration test against the firm's infrastructure. While conducting the scan, he receives only the network diagram and the network list to scan against the network. Which of the following scan types is Joe performing?
Question 179
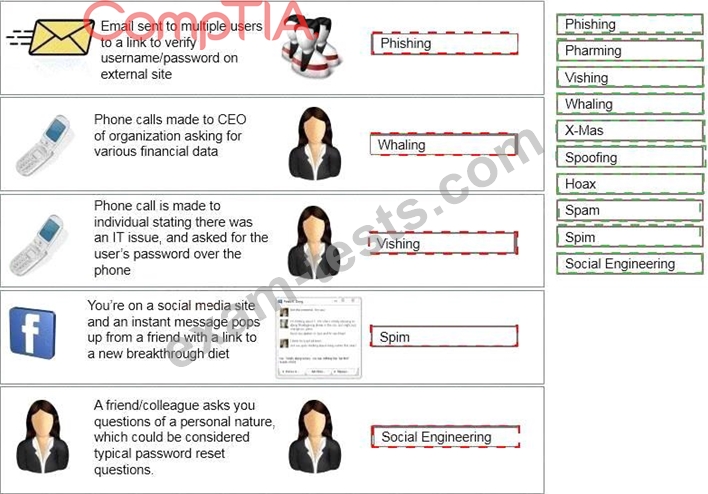
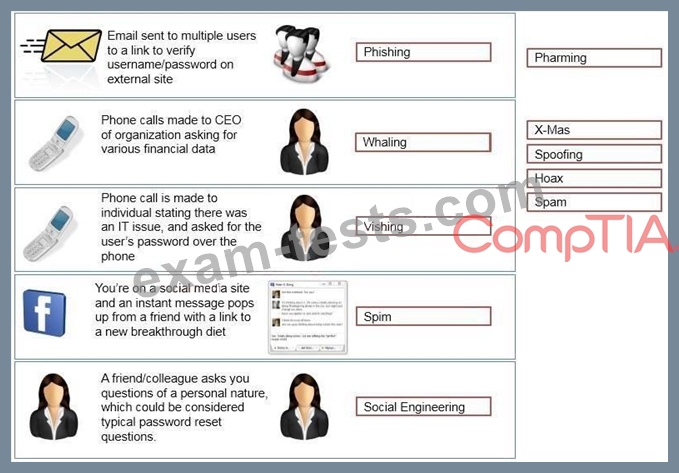
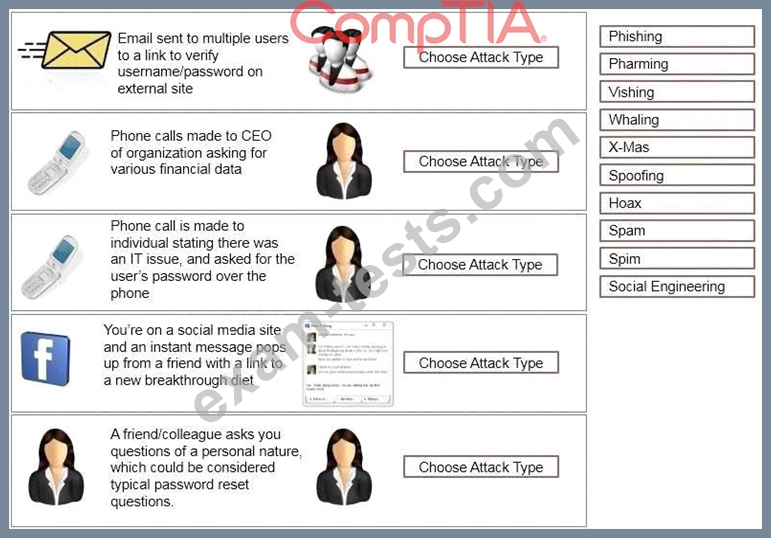
Task: Determine the types of attacks below by selecting an option from the dropdown list.

Question 180
Which of the following would have the GREATEST impact on the supporting, database server if input handling is not properly implemented on a web application?