Question 201
A malicious system continuously sends an extremely large number of SYN packets to a server.
Which of the following BEST describes the resulting effect?
Which of the following BEST describes the resulting effect?
Question 202
A security administrator would like to ensure that some members of the building's maintenance staff are only allowed access to the facility during weekend hours. Access to the facility is controlled by badge swipe and a man trap.
Which of the following options will BEST accomplish this goal?
Which of the following options will BEST accomplish this goal?
Question 203
You have just received some room and WiFi access control recommendations from a security consulting company. Click on each building to bring up available security controls. Please implement the following requirements:
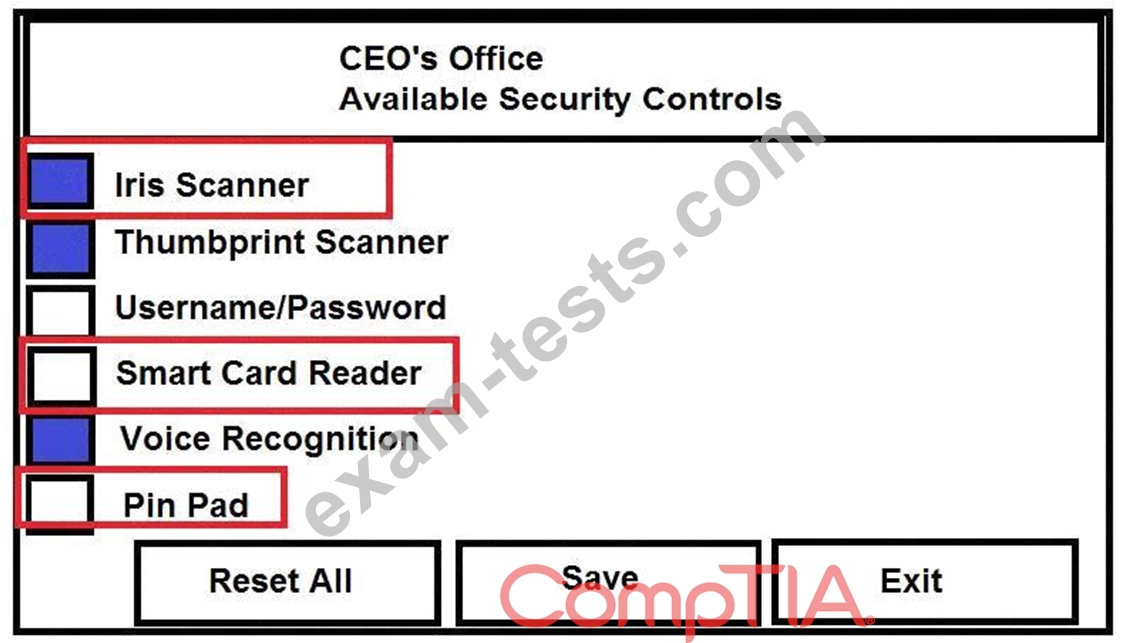
The Chief Executive Officer's (CEO) office had multiple redundant security measures installed on the door to the office. Remove unnecessary redundancies to deploy three-factor authentication, while retaining the expensive iris render.
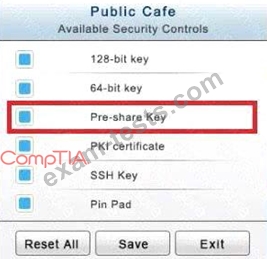
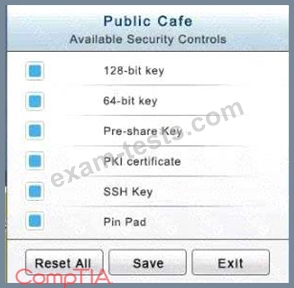
The Public Cafe has wireless available to customers. You need to secure the WAP with WPA and place a passphrase on the customer receipts.
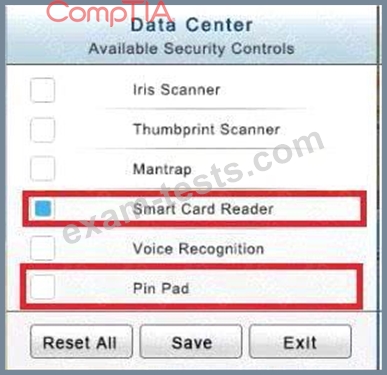
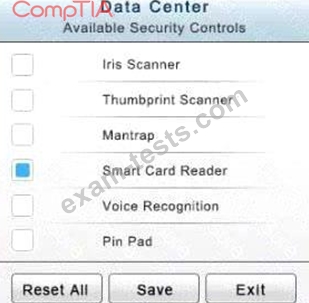
In the Data Center you need to include authentication from the "something you know" category and take advantage of the existing smartcard reader on the door.
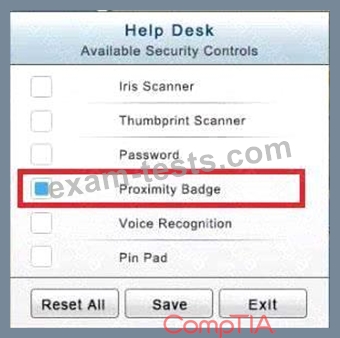
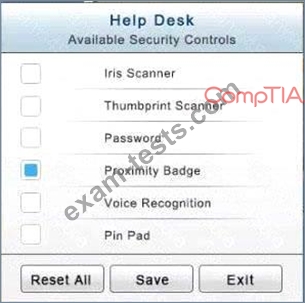
In the Help Desk Office, you need to require single factor authentication through the use of physical tokens given to guests by the receptionist.
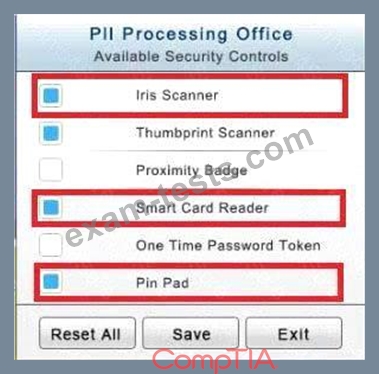
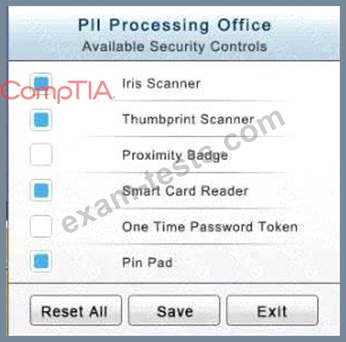
The PII Office has redundant security measures in place. You need to eliminate the redundancy while maintaining three-factor authentication and retaining the more expensive controls.
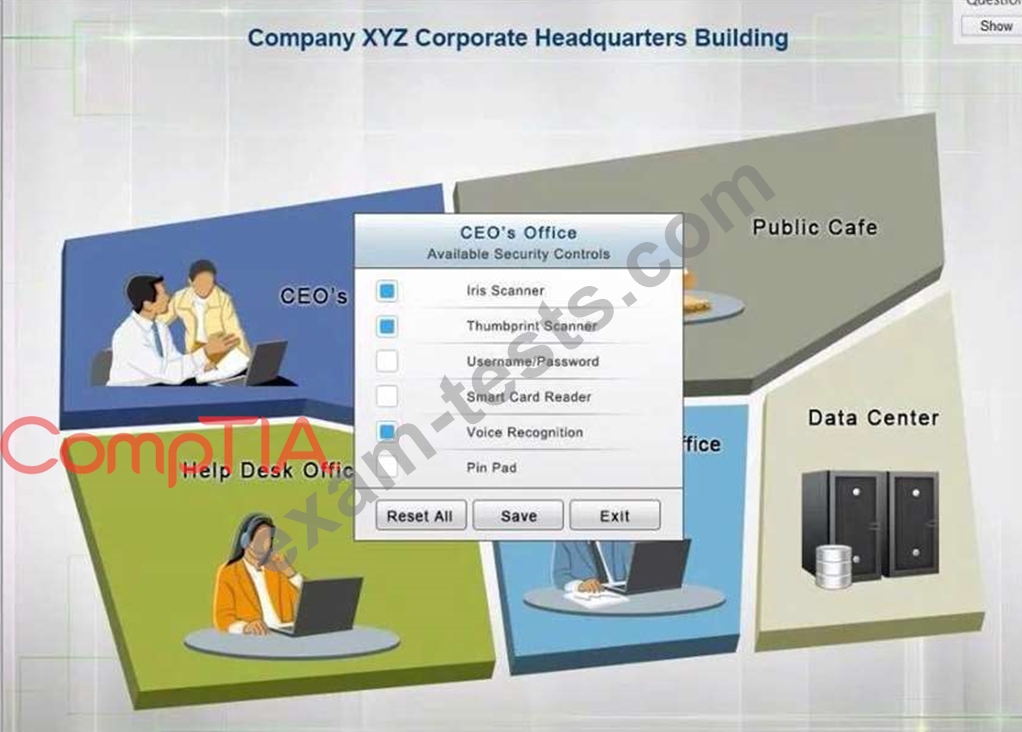
Instructions: The original security controls for each office can be reset at any time by selecting the Reset button. Once you have met the above requirements for each office, select the Save button. When you have completed the entire simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
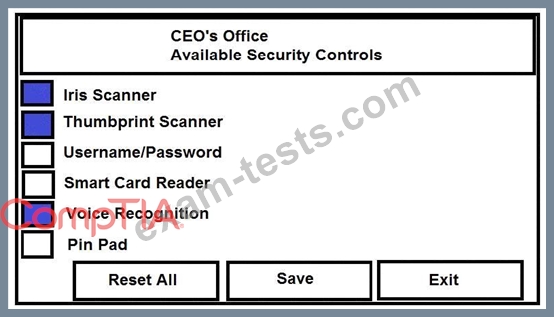
The Chief Executive Officer's (CEO) office had multiple redundant security measures installed on the door to the office. Remove unnecessary redundancies to deploy three-factor authentication, while retaining the expensive iris render.
The Public Cafe has wireless available to customers. You need to secure the WAP with WPA and place a passphrase on the customer receipts.
In the Data Center you need to include authentication from the "something you know" category and take advantage of the existing smartcard reader on the door.
In the Help Desk Office, you need to require single factor authentication through the use of physical tokens given to guests by the receptionist.
The PII Office has redundant security measures in place. You need to eliminate the redundancy while maintaining three-factor authentication and retaining the more expensive controls.

Instructions: The original security controls for each office can be reset at any time by selecting the Reset button. Once you have met the above requirements for each office, select the Save button. When you have completed the entire simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.





Question 204
An analyst has determined that a server was not patched and an external actor extiltrated data on port 139.
Which of the following sources should the analyst review to BEST ascertain how the incident could have been prevented?
Which of the following sources should the analyst review to BEST ascertain how the incident could have been prevented?
Question 205
While performing surveillance activities, an attacker determines that an organization is using 802.1X to secure LAN access.
Which of the following attack mechanisms can the attacker utilize to bypass the identified network security?
Which of the following attack mechanisms can the attacker utilize to bypass the identified network security?