Question 211
A chief information officer (CIO) is concerned about PII contained in the organization's various data warehouse platforms. Since not all of the PII transferred to the organization is required for proper operation of the data warehouse application, the CIO requests the in needed PII data be parsed and securely discarded. Which of the following controls would be MOST appropriate in this scenario?
Question 212
After being alerted to potential anomalous activity related to trivial DNS lookups, a security analyst looks at the following output of implemented firewall rules:
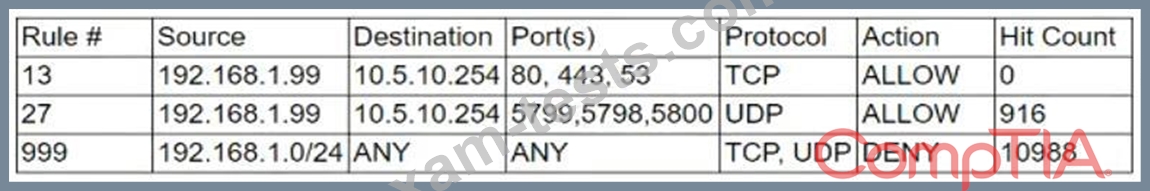
The analyst notices that the expected policy has no hit count for the day. Which of the following MOST likely occurred?

The analyst notices that the expected policy has no hit count for the day. Which of the following MOST likely occurred?
Question 213
A system administrator runs a network inventory scan every Friday at 10:00 am to track the progress of a large organization's operating system upgrade of all laptops. The system administrator discovers that some laptops are now only being reported as IP addresses. Which of the following options is MOST likely the cause of this issue?
Question 214
A security administrator learns that PII, which was gathered by the organization, has been found in an open forum. As a result, several C-level executives found their identities were compromised, and they were victims of a recent whaling attack.
Which of the following would prevent these problems in the future? (Select TWO).
Which of the following would prevent these problems in the future? (Select TWO).
Question 215
A new security administrator ran a vulnerability scanner for the first time and caused a system outage.
Which of the following types of scans MOST likely caused the outage?
Which of the following types of scans MOST likely caused the outage?

