Question 226
Which of the following precautions MINIMIZES the risk from network attacks directed at multifunction printers, as well as the impact on functionality at the same time?
Question 227
Which of the following types of security testing is the MOST cost-effective approach used to analyze existing code and identity areas that require patching?
Question 228
Proprietary information was sent by an employee to a distribution list that included external email addresses.
Which of the following BEST describes the incident that occurred and the threat actor in this scenario?
Which of the following BEST describes the incident that occurred and the threat actor in this scenario?
Question 229
Joe, a member of the sales team, recently logged into the company servers after midnight local time to download the daily lead form before his coworkers did. Management has asked the security team to provide a method for detecting this type of behavior without impeding the access for sales employee as they travel overseas.
Which of the following would be the BEST method to achieve this objective?
Which of the following would be the BEST method to achieve this objective?
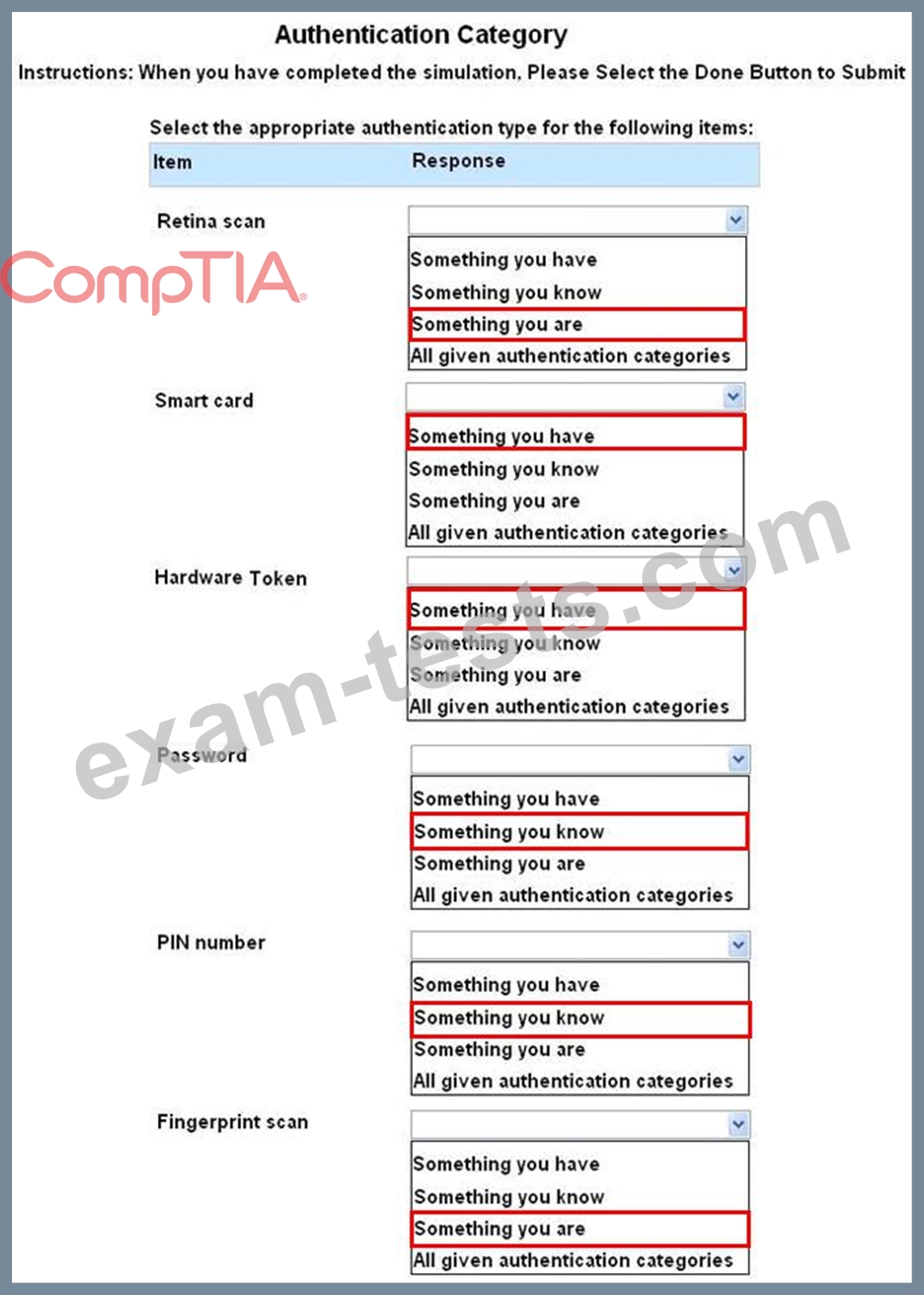
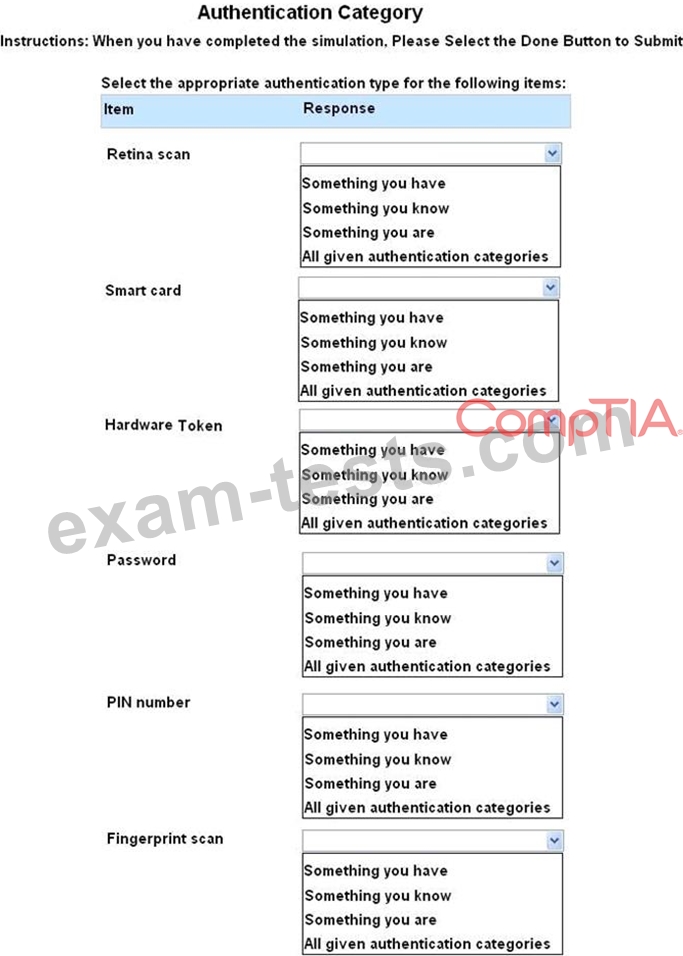
Question 230
For each of the given items, select the appropriate authentication category from the dropdown choices.
Instructions: When you have completed the simulation, please select the Done button to submit.
Instructions: When you have completed the simulation, please select the Done button to submit.