Question 256
A security analyst conducts a manual scan on a known hardened host that identifies many non-compliant configuration items.
Which of the following BEST describe why this has occurred? (Choose two.)
Which of the following BEST describe why this has occurred? (Choose two.)
Question 257
A company is evaluating cloud providers to reduce the cost of its internal IT operations. The company's aging systems are unable to keep up with customer demand. Which of the following cloud models will the company MOST likely select?
Question 258
A security analyst is reviewing an assessment report that includes software versions, running services, supported encryption algorithms, and permission settings. Which of the following produced the report?
Question 259
SIMULATION
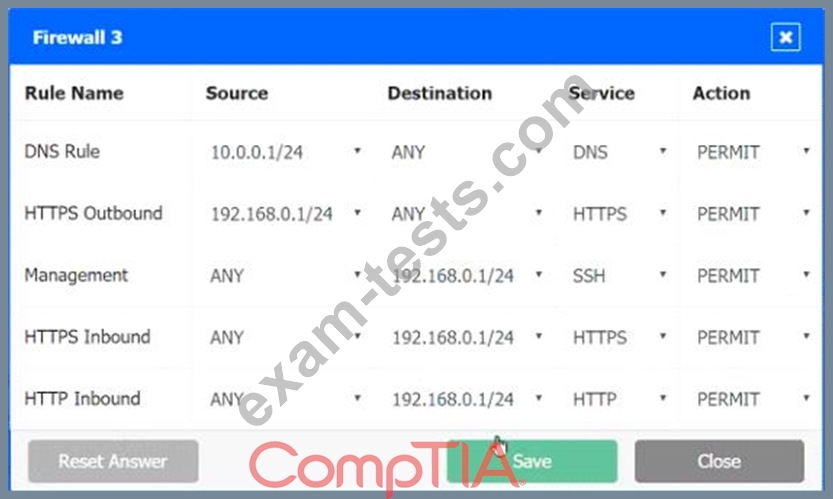
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
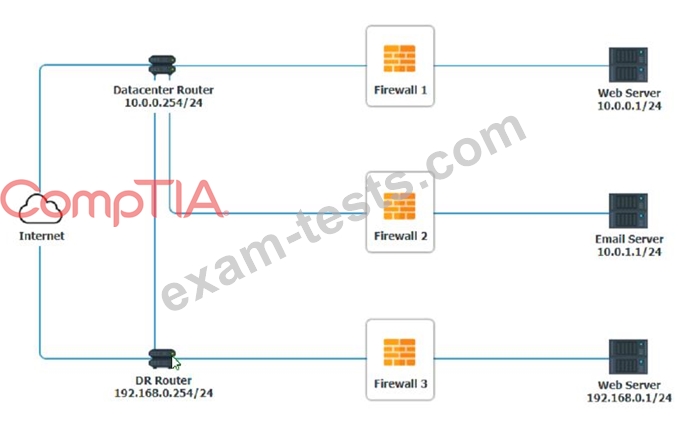
INSTRUCTIONS
Click on each firewall to do the following:
1. Deny cleartext web traffic
2. Ensure secure management protocols are used.
3. Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
Hat any time you would like to bring back the initial state of the simulation, please dick the Reset All button.
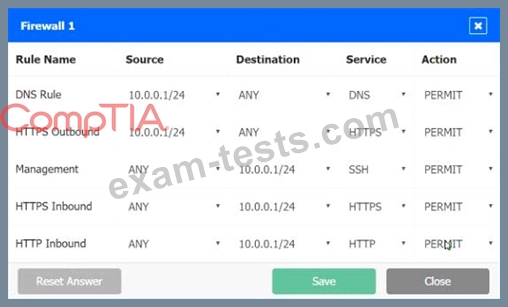
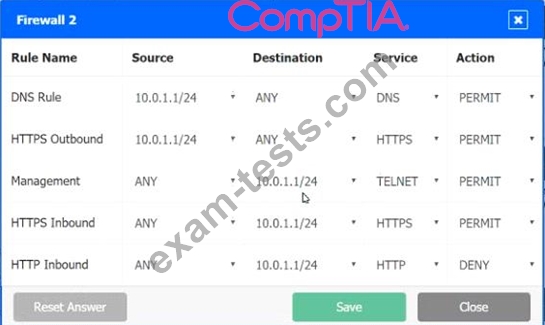
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.

INSTRUCTIONS
Click on each firewall to do the following:
1. Deny cleartext web traffic
2. Ensure secure management protocols are used.
3. Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
Hat any time you would like to bring back the initial state of the simulation, please dick the Reset All button.



Question 260
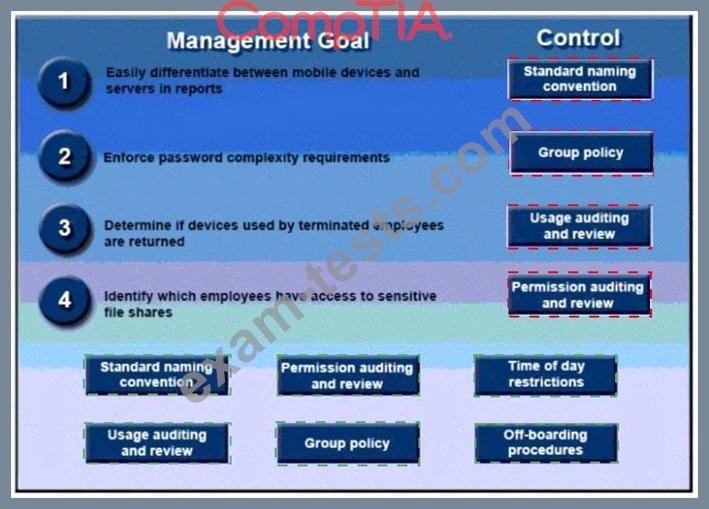
A security administrator has been tasked with implementing controls that meet management goals. Drag and drop the appropriate control used to accomplish the account management goal. Options may be used once or not at all.