Question 261
A security analyst is hardening a server with the directory services role installed. The analyst must ensure LDAP traffic cannot be monitored or sniffed and maintains compatibility with LDAP clients. Which of the following should the analyst implement to meet these requirements? (Select two.)
Question 262
A technician has been asked to document which services are running on each of a collection of 200 servers.
Which of the following tools BEST meets this need while minimizing the work required?
Which of the following tools BEST meets this need while minimizing the work required?
Question 263
An organization has several production-critical SCADA supervisory systems that cannot follow the normal
30- day patching policy.
Which of the following BEST maximizes the protection of these systems from malicious software?
30- day patching policy.
Which of the following BEST maximizes the protection of these systems from malicious software?
Question 264
A security analyst has received the following alert snippet from the HIDS appliance:
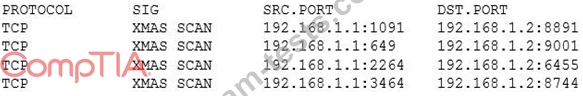
Given the above logs, which of the following is the cause of the attack?

Given the above logs, which of the following is the cause of the attack?
Question 265
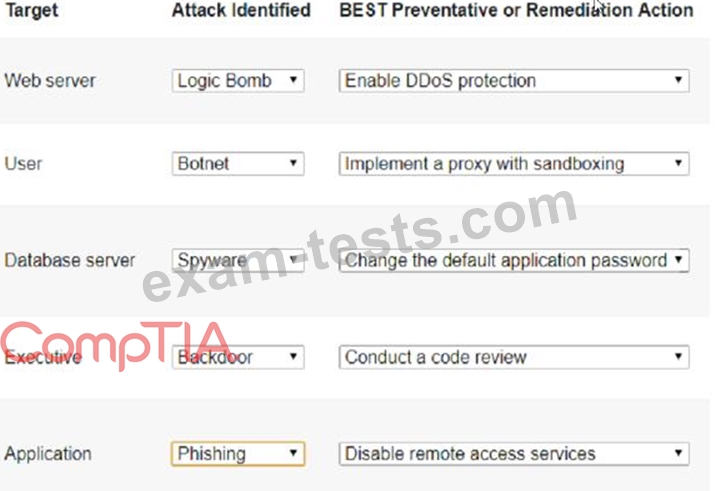
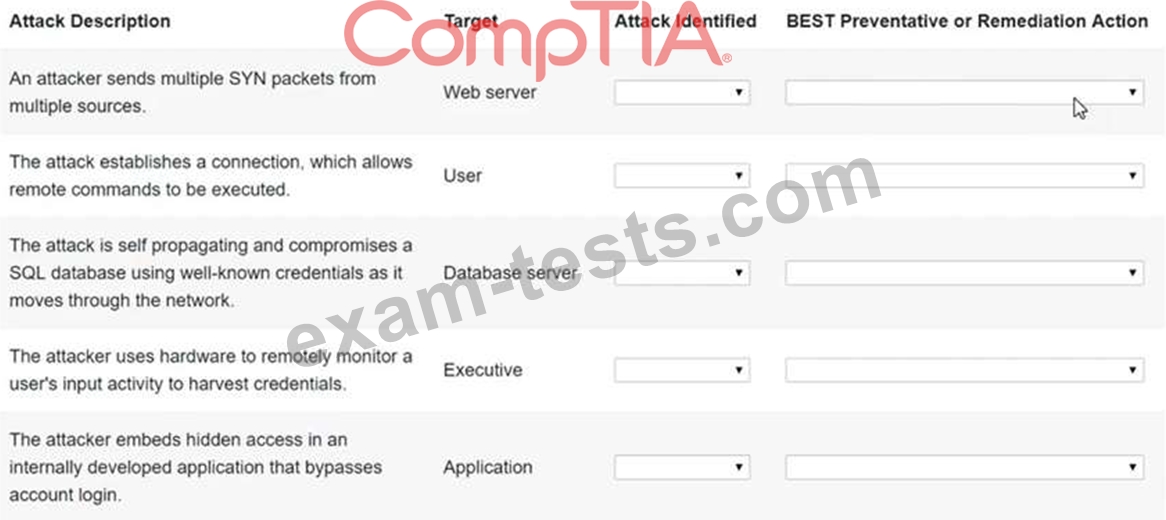
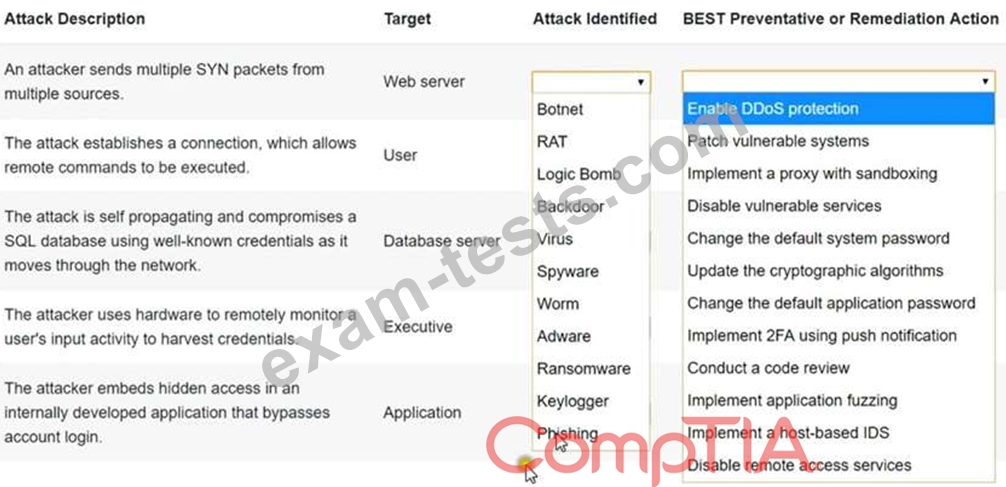
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
INSTRUCTIONS
Not all attacks and remediation actions will be used. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.