Question 271
After segmenting the network, the network manager wants to control the traffic between the segments. Which of the following should the manager use to control the network traffic?
Question 272
Given the following output:
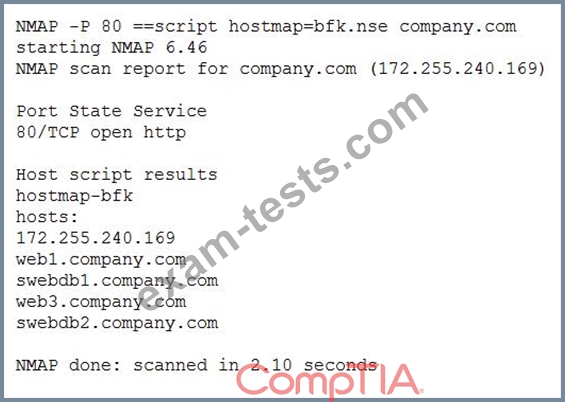
Which of the following BEST describes the scanned environment?

Which of the following BEST describes the scanned environment?
Question 273
After discovering a security incident and removing the affected files, an administrator disabled an unneeded service that led to the breach. Which of the following steps in the incident response process has the administrator just completed?
Question 274
A technician has installed a new AAA server, which will be used by the network team to control access to a company's routers and switches. The technician completes the configuration by adding the network team members to the NETWORK_TEAM group, and then adding the NETWORK_TEAM group to the appropriate ALLOW_ACCESS access list. Only members of the network team should have access to the company's routers and switches.

Members of the network team successfully test their ability to log on to various network devices configured to use the AAA server. Weeks later, an auditor asks to review the following access log sample:
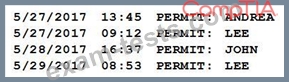
Which of the following should the auditor recommend based on the above information?

Members of the network team successfully test their ability to log on to various network devices configured to use the AAA server. Weeks later, an auditor asks to review the following access log sample:

Which of the following should the auditor recommend based on the above information?
Question 275
Two users need to send each other emails over unsecured channels. The system should support the principle of non-repudiation. Which of the following should be used to sign the user's certificates?

